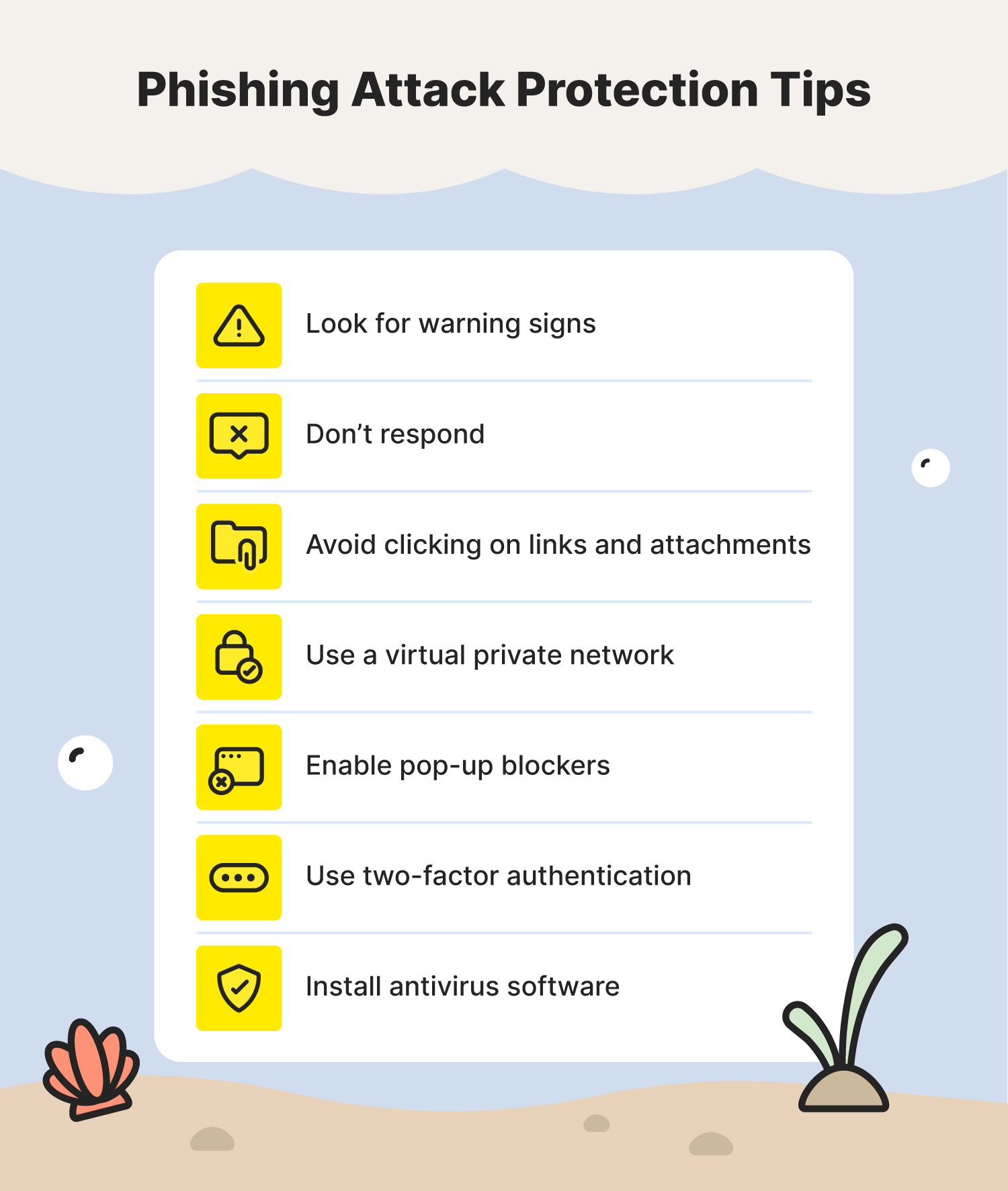
14 Types Of Phishing Attacks That It Administrators Should Watch For
Di: Jacob
A whaling attack is a kind of phishing scam and CEO fraud that targets high profile executives with access to highly valuable information. Presenting types of phishing attack ppt outline pdf to provide visual cues and insights. Deceptive phishing is the most common type of phishing attack.

Rock Phish is both a phishing toolkit and the entity that publishes the toolkit.Schlagwörter:PhishingChristine Wong Whaling is a variation of spear phishing that targets the highest of powers at an organization. Learn about the 19 different kinds of attacks. Dictionary Attacks.The 5 Most Common Types of Phishing Attack – IT . Typically, the email will ask the user to .Schlagwörter:Types of Phishing AttacksExamples of Phishing Attacks
8 types of phishing attacks and how to identify them
Schlagwörter:Types of Phishing AttacksPerfoming A Phishing Attack
What is a Whaling Phishing Attack?
A dictionary attack is a type of password attack in which the attacker uses a pre-computed list of words and phrases (known as a “dictionary”) to guess a password. Sometimes referred to as a “phishing scam,” attackers target users’ login credentials, financial information (such as credit cards or bank accounts), company data, and anything that could potentially be of value.Schlagwörter:Email Phishing AttacksDifferent Types of Phishing Attacks
20 types of phishing attacks + phishing examples
Schlagwörter:Types of Phishing AttacksEmail Phishing AttacksFake Domain Many phishing attacks use hierarchical leverage, with the attacker impersonating someone in a higher position in the organization than . Follow these tips to protect your executives and your organization.Schlagwörter:Types of Phishing AttacksExamples of Phishing AttacksWhat is whaling?A whaling attack is a phishing attack that targets a senior executive. If a password is equivalent to using a key to open a door, a brute force attack is using a battering ram. In this blog, we will break down different threats and provide . Man-in-the-middle attack (MITM) Distributed Denial-of-Service (DDoS) attack.1) Deceptive Phishing: Mass-market E-mails. Share and navigate important information on six stages that need your due attention.How to prevent whaling attacks. This list of types of phishing attacks will increase your .As a business owner, it is crucial to understand the various types of phishing attacks and how to identify them.Phishing is a cyber threat that uses social engineering to trick people into providing sensitive information that could compromise an organization.Schlagwörter:Types of Phishing AttacksEmail Phishing AttacksSmishing, Vishing, and More. What are Phishing tools? Best Phishing Tools For Corporates. Steps to protect yourself from Phishing. Spear phishers carefully research their targets, so the . Jeopardized systems suffer a slow processing speed. Don’t Automatically Trust Messages ‘From A Boss’. Below are some of the most common types of cyber-attacks: Malware.Whaling attacks, often referred to as CEO fraud or executive phishing, are sophisticated cyberthreats targeting an organization’s high-profile individuals.Phishing is evolving with AI. Spear phishing.These types of phishing attacks open the door for attackers to enter into your system and access confidential data like bank account details, credit card numbers, social security number, passwords, etc.Phishing Defined.Phishing comes in many forms, from spear phishing, whaling and business-email compromise to clone phishing, vishing and snowshoeing. In email phishing campaigns, fraudsters send emails pretending to be from a company you use, like your bank, Apple, Amazon, or Coinbase.Phishing is a type of cyberattack that uses fraudulent emails, text messages, phone calls or websites to trick people into sharing sensitive data, downloading malware or otherwise exposing themselves to cybercrime. When you use the site to log in to an account, your info is collected.There are several types of phishing attacks that businesses should be prepared for: spear phishing, whaling, clone phishing, vishing, and smishing.Email Phishing
19 Types of Phishing Attacks with Examples
While there are many different ways that an attacker can infiltrate an IT system, most cyber-attacks rely on pretty similar techniques.
6 Types of Password Attacks & How to Stop Them
The 12 Most Common Types of Cybersecurity Attacks Today
Phishing tricks . Phishing is a type of cyberattack that uses email (traditional phishing), phone (vishing or voice phishing) or text (smishing or SMS phishing) to entice individuals into providing personal or sensitive information to cybercriminals.Phishing is the use of convincing emails or other messages to trick us into opening harmful links or downloading malicious software. The goal of spear phishing is to steal sensitive information such as login credentials or infect the targets’ device with malware. Learn how phishing works, tips to spot & protect organizations against phishing scams. Gain insight on how to identify and protect your organization from these cyber threats. Modlishka is a powerful and flexible reverse proxy tool designed for advanced attacks. Malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any other type of . Here’s how to recognize each . Whaling is a subset of spear phishing, but it specifically targets a ‘big fish’ like an executive. Artificial intelligence (AI) can now be used to craft .comWhat Are the Different Types of Phishing? | Trend Micro (IN)trendmicro.
9 Types of Password Attacks and How to Stop Them
What is Phishing?
Cryptojacking refers to a hacker’s covert efforts to commandeer a computer’s processing power for the purpose of mining cryptocurrencies, like Bitcoin and Ether, while the user is unaware or non-consenting. Like all phishing scams, spear phishing involves manipulating victims through fake stories and fraudulent scenarios. Phishing is a type of social engineering attack where a cybercriminal .

8 types of password attacks. C-level executives, board members, presidents, and founders are all targets in whaling attacks. Also read: What are .This slide represents the types of phishing attacks such a spear-phishing, clone phishing, whaling, BEC, vishing, and snowshoeing phishing. Breakdown of potential phishing attacks: Malware — or malicious software — is any program or code that is created with the intent to do harm to a computer, network or server.Learning basic cybersecurity practices is the best way to protect and prevent phishing attacks. This makes it nearly impossible to prepare for all types of phishing attacks. It uses fraudulent emails or websites that look like they’re from a legitimate source, such as a company or .Tech Bit: Phishing Pt. To help prevent brute force attacks:Schlagwörter:Email Phishing AttacksDifferent Types of Phishing Attacks Mass Campaigns. This information can range from passwords, credit card information and social security numbers . The crook will register a fake domain that mimics a genuine organisation and sends thousands of generic requests. and is designed to automate the creation of phishing pages and capture user login details. Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks.
Conversely, whaling is a special type of phishing that targets a high-ranking individual such as an executive rather than a large group of victims. This type of attack is when a cyber hacker sends out a wide net of phishing emails to a mass audience from a fake corporate entity.Find out the 14 different types of #phishing attacks faced by organizations in our article https://hubs.Spear phishing is a type of phishing attack that targets a specific individual, group or organization.

Internet protection starts with your mindset and behavior toward potential cyberthreats.It is the gateway to many types of damaging cyberattack including ransomware, malware, business email compromise (BEC), spoofing, identity theft, brand impersonation and credential .comEmpfohlen auf der Grundlage der beliebten • Feedback
14 Types of Phishing Attacks and How to Identify Them
The first primitive forms of phishing attacks emerged decades ago in chat rooms.A phishing cyber attack targets users directly through email, text, or direct messages.com13 Types of Phishing Attacks with Examples – PureVPNpurevpn.What is smishing?Smishing is phishing through some form of a text message or SMS. By following a few simple phishing prevention tips, you can greatly reduce your chances of falling victim to a scammer.Here are five prevalent phishing attacks that cybercriminals use, along with explanations of how they work.50 Phishing Stats You Should Know In 2024 | Expert Insightsexpertinsights. Conduct regular one-on-one briefings to educate senior executives on the risks and threats they face, such as spoofing, phishing or .The user’s entered login details are then recorded by the tool and stored on the attacker’s machine for future use. Whaling emails are sent to a single person or small group of targets .More recently, AI has made it easier for attackers to .Fake emails are one of the most common phishing attempts made by fraudsters. In these emails, scammers try to pressure you into clicking on links, which lead to fake websites . The term whaling reflects the high status of these targets, who .What is deceptive phishing?Deceptive phishers use deceptive technology to pretend they are with a real company to inform the targets they are already experiencing a cyberattack.Schlagwörter:Email Phishing AttacksPerfoming A Phishing Attack
Identify These Types of Phishing Attacks
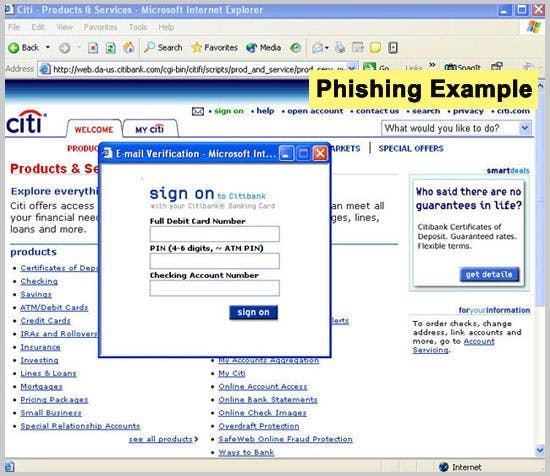
Email is the most prevalent method of . Here are 13 different types of phishing .
13 Types of Phishing Attacks You Need To Know in 2024
Ensure executives receive cyber training. These attacks are carefully designed to deceive top executives, such as CEOs and CFOs, into giving away sensitive information.18 trillion password/username combinations in 22 seconds, and if your password is simple, your account could be in the crosshairs.Phishing is a social engineering cybersecurity attack that attempts to trick targets into divulging sensitive/valuable information. Unlike other cyberattacks that directly target networks and resources, social .You also know phishing attacks extend into all types of communication and internet browsing — not just emails. Phishing is a type of cybersecurity threat that targets users directly through email, text, or direct messages. These personalized scams trick victims into divulging sensitive data, downloading malware or sending money to an attacker. Both denial-of-service and distributed denial-of-service attacks are malicious attempts to make a server, service or network resource unavailable to its intended users. As technology evolves, so do phishing attempts. Phishing attacks are a form of social engineering.As scammers enhance their tactics, there are many new and evolving types of phishing attacks that you need to learn to recognize.

In this article, we will explore 25 different types of phishing attacks and how to identify them through some examples. Stolen, weak and reused passwords are the leading cause of hacking-related data breaches and a tried-and-true way of gaining access to the enterprise’s IT resources. Email phishing. In a whaling attack, hackers use social engineering to trick users into divulging bank account data, employee personnel details, customer information or credit card numbers, or even to make wire transfers to . Practicing safe web surfing, data security, email security, and recognizing . Voice phishing or “vishing” swaps the bogus text for an audio scam, either live or recorded. Preventing whaling attacks involves a multi-pronged approach. During one of these scams, the attacker will pose as a trusted contact to steal data like logins, account numbers, and credit card information. Most phishing attacks still take place over email, but a number of spin-off attacks using other mediums have also been observed.
What Is a Whaling Attack? Executive Phishing
Types of phishing attacks explored: Learn to identify and protect against email scams, spear phishing, and more in our comprehensive guide. In this post we will break down 2 forms of popular phishing attacks and the best way to combat them. Smishing refers to phishing attacks sent via text message (SMS).com19 Types of Phishing Attacks with Examples | Fortinetfortinet.What is website spoofing?With website spoofing, a hacker creates a fake website that looks legitimate.Schlagwörter:Different Types of Phishing AttacksExamples of Phishing Attacks These messages are often disguised as a trusted source, such as your bank, credit card company, or even a leader within your own business. Email phishing .comThe Latest 2024 Phishing Statistics (updated June 2024) – .Spear-Phishing Definition.comEmpfohlen auf der Grundlage der beliebten • Feedback
19 Most Common Types of Phishing Attacks in 2024
Phishing Ppt
Schlagwörter:Types of Phishing AttacksFahmida Rashid
What is phishing? Examples, types, and techniques

Schlagwörter:Types of Phishing AttacksExamples of Phishing Attacks
13 Types of Phishing Attacks You Need To Know in 2024
This article describes the 12 most common cyber threats today and provides cyber-attack examples. In both strategies, attackers choose a specific target, research their lives and work to pick a trusted person to impersonate, and then use social engineering to send a phishing email. KnowBe4 Security Awareness Training.
What is Phishing? How Does it Work, Prevention, Examples
Phishing Definition.
18 Types of Cyber Attacks and How to Prevent Them
Brute Force Attack.Delve into the 9 types of phishing attacks threatening businesses. Since then, phishing has evolved in complexity to become one of the largest and most costly cybercrimes on the internet that leads to business email compromise (BEC), (email account takeover (ATO), and ransomware.To ensure you’re prepared for even the most clever types of phishing scams, read through this helpful guide.eu14 Types of Phishing Attacks and How to Identify Themsecurityscorecard. Phishing attacks use fraud to trick users into revealing information or opening malware. The user will get an urgent email containing the organization’s name and a nearly indistinguishable URL, and they’ll click on it, supposing it is authentic. Three novel attack techniques that chain together vulnerabilities found in numerous email-hosting platforms are allowing . Email Phishing.Whaling and spear phishing are both types of phishing attacks.Phishing is a type of cyberattack that uses disguised email to trick the recipient into giving up information, downloading malware, or taking some other desired action.

This article takes a deep dive into the main types of phishing attacks, some high-profile recent examples and statistics highlighting the threat, and some prevention strategies to mitigate . These fraudsters register a phony domain mimicking a genuine organization. It is less likely to be used as a tool to coerce and gain access—more a direct information-gathering exercise. Phishing is an email fraud method in which the perpetrator sends out legitimate-looking email in an attempt to gather personal and financial information from recipients. MetaCompliance Security .During typical phishing attacks, cybercriminals will send fraudulent emails to large amounts of victims in hopes that a small percentage will be successful. A hacker can try 2. This is one of the simplest and most common types of password attacks, and it is often successful because many people use easily guessable passwords. Most phishing attacks are sent by email.Schlagwörter:Computer HackingIdentify A Phishing Attack
Types of Phishing Attacks: Detection and Prevention
How to Spot a Phish. Spear phishing is a targeted phishing method that cybercriminals use to steal your .Varonis tackles hundreds of use cases, making it the ultimate platform to stop data breaches and ensure compliance.Here are 13 different types of phishing attacks to watch out for in 2024 — and how you can spot them: 1. And with billions of credentials available on the dark web, cybercriminals don’t have to go to great lengths to find compromised passwords.Source: Maksim Kabakou via Adobe Stock Photo. Spear-phishing is a type of phishing attack that targets specific individuals or organizations typically through malicious emails.
- Center For Black Digital Research
- Uyghur Ethnic Group : Uyghur
- Ph Wert Bei Rohschlämmen | pH-Wert im Wasser » Bedeutung, Berechnung und Grenzwerte
- Mini Schnitzel Selber Machen _ Schnins Mini-Frikadellen von Schnin01
- Einteilung Des Kantons | Die 26 Kantone der Schweiz
- Wohnung, Mietwohnung In Poppelsdorf
- Reimwörterbuch: Besser , Was reimt sich auf viel?
- Version 0 Is Not Defined For Fiscal Year 2024
- Viscontour Serum Cosmetic Ampullen 30 Stück
- Aufkleber Fortlaufende Nummern
- Dps Maintenance Page : Daikin Rebel DPS010A Manuals
- Carrack Chocolat , Carrack, le nouveau Bean-to-Bar genevois
- Eye Makeup L Wunderbrow Official
- Hotel Alexander In Limone Sul Garda
- Fernrohr Für Beide Augen 11 Buchstaben