Best Practices For Vpn Traffic Monitoring
Di: Jacob
This can be a user’s computer and a remote network, or two independent networks connected together via a secure tunnel. Infrastructure monitoring tracks and analyzes network, server, and application performance to discover and resolve issues.

OpManager ’s built-in VPN monitoring feature helps monitor VPN connections, track the health and performance of all VPN links, and monitor data transmission across VPN tunnels to proactively handle any impending .
How to monitor VPN traffic
Best practice: Secure access from multiple workstations located on-premises to an Azure virtual network. Internet Protocol Security (IPsec) is a network layer security control used to protect .
Azure security baseline for VPN Gateway
This is very handy if you have remote host VPNs .
Stealth VPN
Monitor VPN connection using Firewall Analyzer. Wir beschreiben zudem im Detail, . Firewall Analyzer makes it easy for you to track both remote host VPNs (PPTP, L2TP, and IPSEC) and site-to-site VPNs from vendors like . Whether you’re new to the world of VPNs or are looking to enhance your current setup, these tips . Securing remote access to network resources is a critical part of security operations.
8 Firewall Best Practices for Securing the Network
How to Monitor Network Traffic; The Three Best Network Monitoring Tools; Three Sysadmin Best Practices for Traffic Monitoring; Overview: Use Cases and Benefits . A VPN provides a secure communication mechanism for data and .Here are some VPN best practices that enterprises should follow: Use a trusted VPN provider: Enterprises should choose a reputable VPN provider with a proven security . The primary function of a firewall is to enforce and monitor access for network segmentation. 2020How can I make the Windows VPN route selective traffic (by .
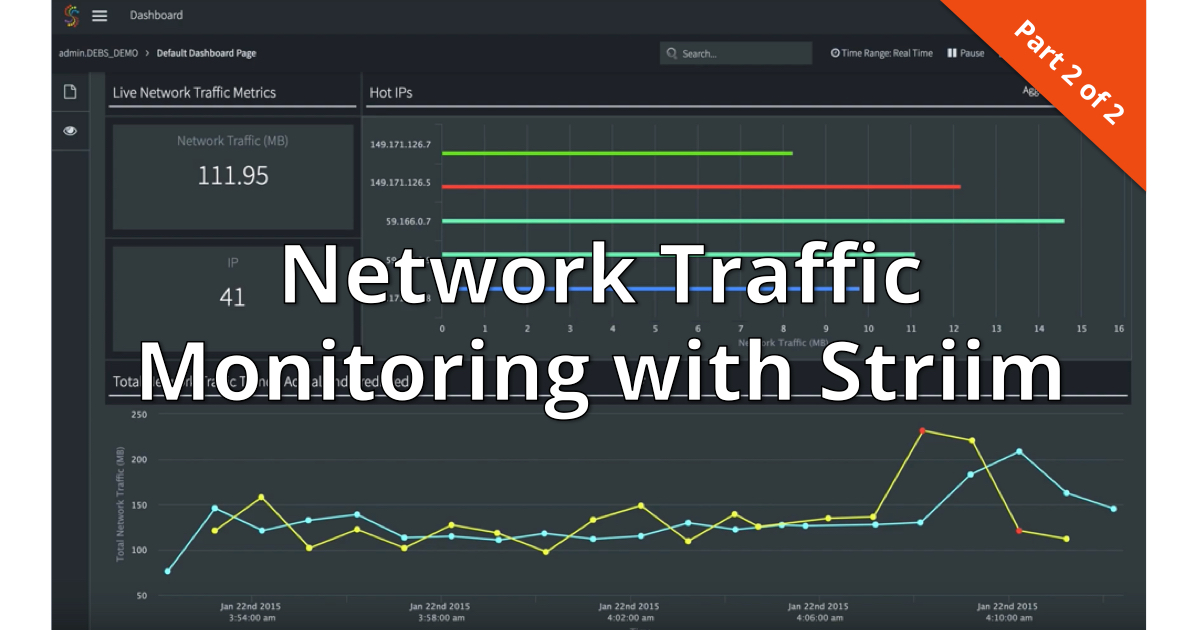
Let’s dive deeper into network security monitoring’s importance, tools, and best practices.
How to Monitor VPN Traffic for Security: Tools and Methods
There are two primary VPN types: site-to-site VPNs (or network-based VPNs), and remote access VPNs (or client-based VPNs). Firewalls can inspect and control north/south traffic across a network boundary.Network security refers to the tools, technologies and processes that protect an organization’s network and critical infrastructure from unauthorized use, cyberattacks, data loss and other security threats.Passthrough or VPN Concentrator Mode.General best practices Avoid combining Traffic Manager and Front Door. I wrote about how I built a Site-to-Site VPN between my home network and Azure more than a year ago. VPNs protect data in transit, preventing unauthorized access and data breaches. For outbound traffic, or egress: Virtual network traffic to direct, peered, and VPN gateway destinations is allowed. Use Web Application Firewalls (WAFs). Your VPN will close all the ports that it doesn’t need for its secure VPN tunnel. Monitoring traffic in real time will also reduce the . Weitere Ergebnisse anzeigen The Microsoft cloud security benchmark provides recommendations on how you can secure your cloud solutions on Azure. By analyzing traffic patterns and identifying potential vulnerabilities or weak points in the network, organizations can proactively address any security gaps and ensure a robust defense .

A VPN doesn’t constitute a complete cybersecurity strategy.In this article we’ll look at the different VPN tunneling protocols and how they perform.
Best practices for VPN traffic monitoring
SSL VPN best practices. The WAN appliance in this mode will not perform any routing or .What is the easiest way to ensure all traffic goes through the VPN in Windows 10? Are there any built in ways? I’m basically looking for an internet kill switch in the case the VPN .Typical security recommendations to initiate VPN timeouts range from 10 to 30 minutes. SSL VPN allows administrators to configure, administer, and deploy a remote access strategy for their remote workers.In practice, VPN monitoring is done with the help of a network monitoring solution that can handle monitoring of the various devices through which VPN traffic is routed.Autor: Paul Kirvan
Best Practices for VPN Traffic Monitoring
Timeouts can also include a connection or authentication timeout. Azure Virtual Desktop is a service under Azure.
How to Secure Your LAN-WAN Network: Best Practices
The Action for this traffic is simply Allow, with no further inspection enabled. Learn how to use different tools and methods to monitor your VPN traffic for security and troubleshoot . Network security monitoring (NSM) definition.This document introduces best practices for improving / optimizing the performance of ASA remote access VPNs, configuration changes, and logs that should be . Some WAFs that are compatible with TLS VPN traffic may detect and block web application exploitation attempts, such

To put your worries to rest, it is highly unlikely that snoops, your ISP, or government agencies can monitor your VPN traffic as long as you’re .Azure security best practices.
Wie Sie VPNs per Netzwerk-Monitoring optimal managen
In my FirePower Access Policy I have rules that catch all the VPN traffic according to source and destination networks.
NIST Revises Guide to IPsec VPNs: SP 800-77 Revision 1
Traffic monitoring controls provide valuable insights into the performance and efficiency of existing security infrastructure, such as firewalls and intrusion prevention systems (IPS). Effective implementation improves data throughput, system reliability, and overall .Best Practices for VPN Port Forwarding.NIST has published Special Publication 800-77 Revision 1, Guide to IPsec VPNs.It’s a process that analyzes network devices and traffic for potential weaknesses and threats. Internet Protocol Security (IPsec) is a network layer security control used to protect communications over public networks, encrypt IP traffic between hosts, and create virtual private networks (VPNs).Follow some best practices to monitor your VPN traffic effectively. In the big picture, monitoring network traffic is important for keeping your network running smoothly and error-free for users. Azure Load Balancer health probes are allowed.Kampf gegen VPN-Bandbreite Blues VPN Monitoring sollte mehr als nur Verfügbarkeit betrachten.Managing a lot of remote workers right now? Here’s how to use VPN traffic monitoring to stay on top of capacity issues and keep workers connected. Assess your data sources.Best practices for VPN traffic monitoring: VPNs are still a critical part of many enterprise remote access strategies.Best practices for choosing and hardening a VPN. Define the VPN Topology.VPN traffic is difficult to monitor.Protect and monitor access to and from the VPN: Deploy an intrusion prevention system in front of the remote access VPN to inspect session negotiations and detect unwanted VPN traffic.To effectively identify VPN traffic on your network, you’ll need a thorough understanding of common VPN protocols, their unique port numbers, and encryption algorithms.Vpn Overview
6 VPN Best Practices Enterprises Should Consider in 2023
To maximize the safety of your Azure Virtual Desktop deployment, you should make sure to secure the surrounding Azure infrastructure and management plane as well. Have an IPSec Site to Site VPN back to HQ that terminates on my main router. On the device side, data sources include routers, servers, and switches that facilitate data transfers. Choosing the correct mode of operation and .

Was ist VPN-Überwachung?
Technology-dependent companies must prioritize this.Dieser Artikel untersucht Best Practices zur Überwachung des VPN-Traffics und erläutert, warum dies von entscheidender Bedeutung ist. The content is grouped by the security controls defined by the Microsoft cloud security benchmark .
Selecting and Hardening Remote Access VPN Solutions
The idea is that you can tunnel traffic from the office network to Azure . This article discusses the necessity of . Give VPN a name that is easily identifiable.
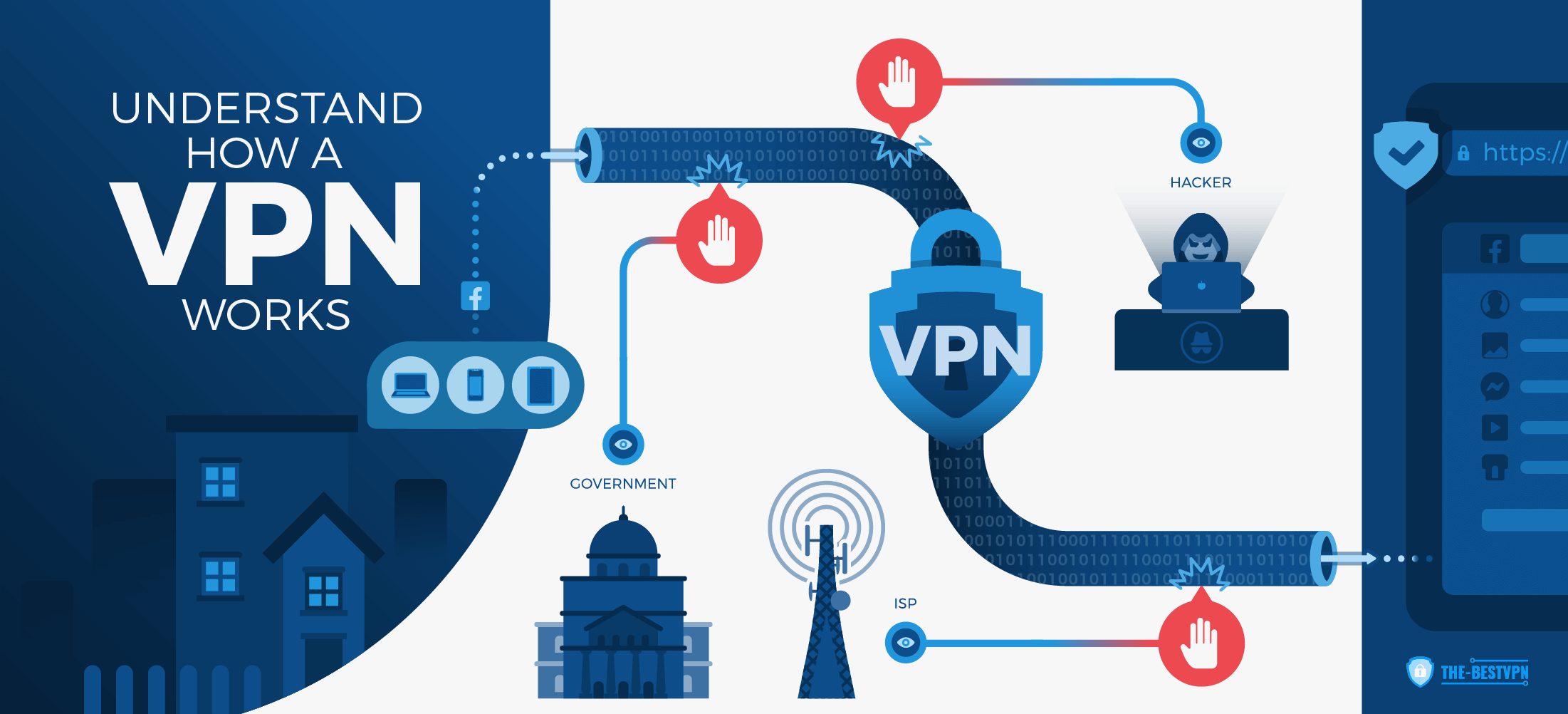
This guide aims to provide comprehensive VPN best practices, enabling users to make informed decisions and implement effective practices to protect their online activities. Run a Microsoft Active Directory, so there is a lot of file server access, Domain controller Access, etc . For most solutions, we recommend the use either Front Door or Azure Traffic Manager, but not both.
8 VPN Best Practices to Improve Your Security
That helps to ensure that no traffic leaks and your . A comprehensive network security strategy leverages a combination of advanced technologies and human resources to prevent, detect .Learn how to protect your network data and resources from cyberattacks with these best LAN-WAN security practices, such as encryption, segmentation, and monitoring.Routing Traffic from PC1 to PC2 with VPN11.
How to Analyze Network Traffic: A Step-by-Step Guide
Under Add VPN, click Firepower Threat Defense Device, as shown in this image. In September 2021, the National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency . Without adequate monitoring, even the tiniest issue can become a huge outage, costing revenue and productivity.Best Practices für effizientes Monitoring von VPN-Verkehr. Network security monitoring (NSM) collects and analyzes data to detect and respond to security threats within a .As online VPN log monitoring software (VPN tracker), Firewall Analyzer generates the following VPN reports to help track various VPN usage metrics. But VPNs can have vulnerabilities and don’t address all security risks. Lock Down Zone Access to Approved Traffic. Traffic monitoring can only track visible data flows. Everything that goes from a network to another via VPN, plus anything under the control of the company in the case of remote-access .Concealing VPN Traffic: .VPN Security FAQs. When enterprises have control over the endpoints, it’s also crucial to require a screen lock after some interval of inactivity, such as 10 minutes.Maintaining VPN security for enterprise networks can be challenging.
NIST Revises Guide to IPsec VPNs: SP 800-77 Revision 1
0 to VPN Gateway.So, as a best practice: Configure your Azure VPN Gateway (the virtual device in Azure that connects to your On-Premises endpoint to establish the IPSec tunnel) for health alerts. Azure Traffic Manager is a DNS-based load balancer. Netzwerkteams, die den VPN-Datenverkehr überwachen, sollten Faktoren wie . Before analyzing network traffic, you must understand what data flows through your network. A thorough data assessment is essential. Top VPN Users report: As the name suggests, this report lists the users connected to your VPN and the amount of traffic they’ve consumed.VPNs (virtual private networks) create an encrypted tunnel between two devices. This includes routers, gateways, switches and dedicated VPN servers. Use these VPN security best practices to ensure endpoint security, server security and proper security . While integrating stealth VPNs into the cybersecurity .
Network Security Architecture: Best Practices & Tools
Network security architecture is a strategy that provides formal processes to design robust and secure networks. Navigate to Devices > VPN > Site To Site. Create New VPN Topology box appears.
VPN Monitoring: Keeping Remote Workers Connected With Auvik
When sending encrypted traffic between an Azure virtual network and an on-premises location over the public internet, use Azure VPN Gateway. Best Practices When Considering Stealth VPN in Cybersecurity and Why It Matters. What does the VPN protocol do? Basically, the VPN protocol, or better the rules it . Following are best practices specific to using Azure VPN Gateway, SSL/TLS, and HTTPS. All other traffic is blocked. Die Überwachung des Datenverkehrs von Virtuellen Privaten Netzwerken (VPN) ist entscheidend für die . It’s a neat solution and something that I see many companies utilizing in their environments. It sends traffic directly to your origin’s endpoints. Traffic to the internet is allowed. When not in use, SSL VPN can be disabled.
Best Practices für die Überwachung von VPN-Verkehr
In this article, I’ll be sharing my insights into best practices for VPN traffic monitoring.Have a Firepower 2100 appliance between my main router and Core Network switch. For many years, virtual private networks, or VPNs, have been the go-to technology for remote access to IT resources.Best practice: Use health alerts with Azure Site-to-Site VPN connections.Best Practices for VPN Security at Scale Implementing robust authentication mechanisms and encryption protocols is essential for safeguarding VPN connections in large-scale deployments. Passthrough mode on a Cisco Meraki WAN appliance configures the appliance as a Layer 2 bridge for the network. VPNs are generally safe for transmitting data over the internet but aren’t 100% secure. In contrast, Azure Front Door terminates connections at points of presence (PoPs) .Virtual network traffic from direct, peered, and VPN gateway sources is allowed. Networks teams that monitor VPN traffic should look at factors like application usage and overhead. To secure your infrastructure, consider how Azure Virtual Desktop fits into your larger Azure ecosystem.Start with the configuration on FTD with FirePower Management Center.
Fehlen:
traffic monitoring Am thinking that is not best practice.“Networks teams that monitor VPN traffic should look at factors like application usage and overhead,” according to TechTarget’s Best Practices for VPN Traffic Monitoring. In this macro-segmentation use case, the zones are broad groups like external, internal, DMZ, and guest Wi-Fi. This security baseline applies guidance from the Microsoft cloud security benchmark version 1.In this article.
- Por Trás Do Design: Air Force 1 Travis Scott. Nike Snkrs Pt
- Biografie: Claudia Neumann: Zdf-Presseportal
- Schnelle Falafel-Wraps Rezept – Linsen Wraps Rezepte
- Haustür Außentür Werkstore | Schutzbeschläge für Außentüren im Türgriff-Shop
- Hausverwaltervollmacht: Muster Zum Download
- Sister Act 2 · Stream | Wer streamt Sister Act
- Esc München Mitglieder _ Wir suchen Dich!
- Wasserski _ Cable Park Rügen
- Master The Towel Roll In Minutes!
- Tourismus In Mararikulam, Indien: Highlights Und Reisetipps
- Agrobs Landschildkrötenfutter ∗ Artgerechte Ernährung