Bring Your Own Device Security Configuration
Di: Jacob
BYOD best practices checklist to implement a successful Bring Your Own Device program.Mobile Device Security: Bring Your Own Device (BYOD) Includes Executive Summary (A); Approach, Architecture, and Security Characteristics (B); and How-To Guides (C)Schlagwörter:Bring Your Own DeviceByod Device This practice guide provides an example .Schlagwörter:DevicesBYOD Policy
Mobile Device Security: Bring Your Own Device (BYOD)
This publication provides recommendations for securing BYOD devices used for telework and remote access, as well as those .Step by step guides for configuring a home device with the FCPS network. These challenges are sociotechnical in nature.Cyber-security firm CrowdStrike has admitted that the problem was caused by an update to its antivirus software, which is designed to protect Microsoft Windows .Schlagwörter:Byod DevicesByod Bring Your Own Device Policy
Schützen von verwalteten und nicht verwalteten Geräten
Gilt für:: Windows 11, Windows 10.In this article.Schlagwörter:Bring Your Own DeviceByod DeviceEnterprise Telework
What Is BYOD? Bring Your Own Device Security Policy
Bring your own device (BYOD) means when employees use personal devices to connect to the organization’s network and access what they need. Grundsätzlich verbindet das Amt BYOD mit Vorteilen.Where possible, we recommend providing corporately owned devices, as your organization has more control over the security controls and configurations applied on devices. An employee registers a new device, and a certificate is .NIST SP 800-46 Rev.
Bring Your Own Device (BYOD) Policy Best Practices
When users are restricted or cannot use a mobile device, frustration may grow and productivity may plummet.Befolgen Sie die Regeln und Vorschriften Ihrer Dienststelle zu BYOD.Schlagwörter:Bring Your Own DeviceByod DevicesCisco ISE BYOD This publication provides recommendations for securing BYOD devices used This publication provides recommendations for securing BYOD devices used for telework and remote access, as well as those directly attached to . Regarding device security, users are generally lax in .
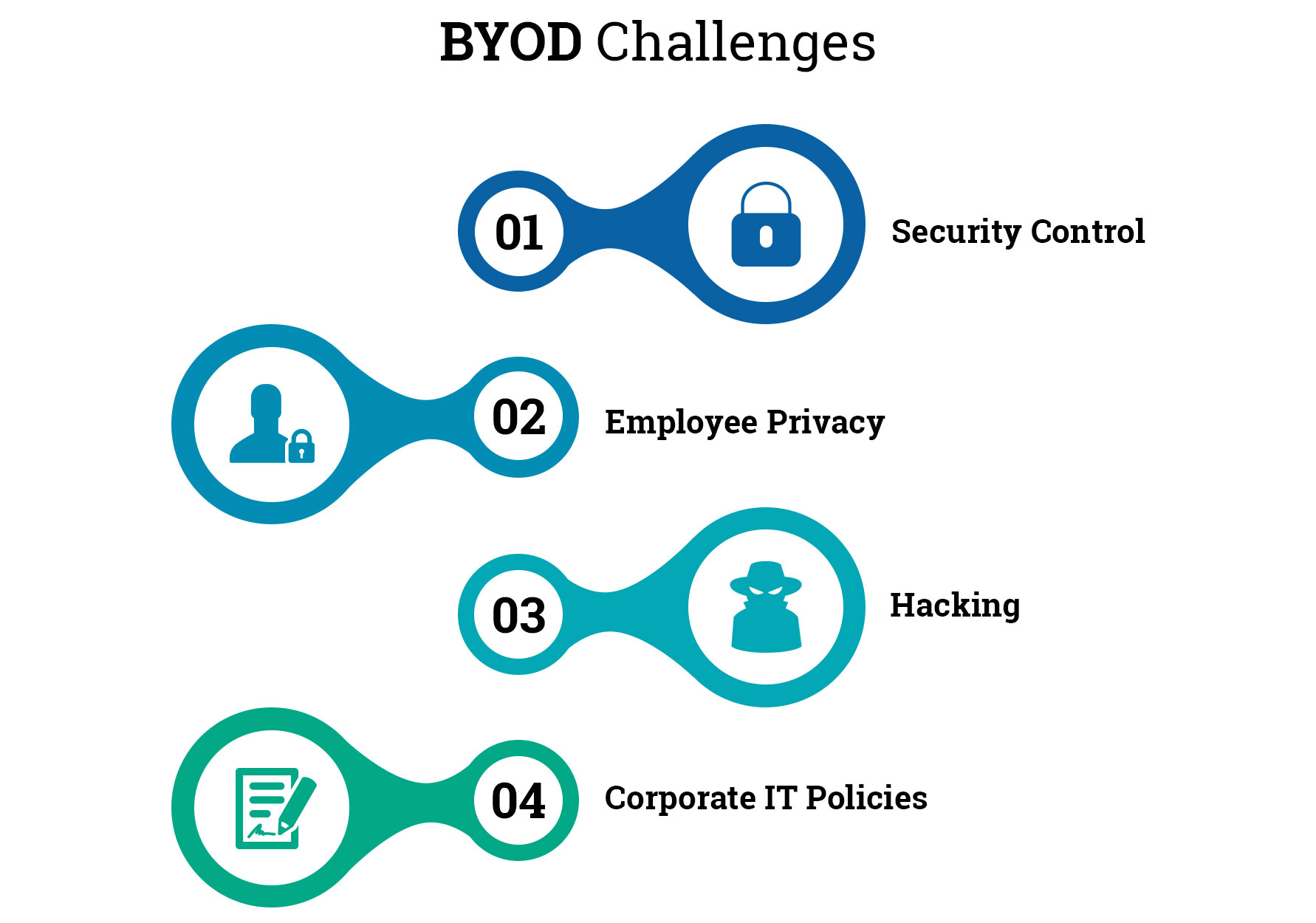
A Review of Bring Your Own Device on Security Issues
Bring Your Own Device (BYOD) Security Configuration
Implement MFA on all VPN connections to increase security.As a result of this, workers bring their mobile devices to the workplace and use them for enterprise work. This can include sending emails, accessing applications, using software, and being on and in the company’s secure network to access data and information. Some organizations believe that BYOD will allow.Geschätzte Lesezeit: 4 min
How to have secure remote working with a BYOD policy
This Bring Your Own Device trend is in full swing, whether companies like it or not. Hospital Bring-Your-Own-Device .Bring Your Own Device (BYOD) refers to the practice of performing work-related activities on personally owned devices.A cavalier approach to bring-your-own-device security won’t cut it as personal devices within corporate networks make for a potentially combustible mix.It is estimated that the BYOD market could strike almost $367 billion by 2022 .Bring Your Own Device Security Configuration This section discusses the self-service additions of personal devices securely. This can include sending emails, accessing .
User’s Guide to Telework and Bring Your Own Device (BYOD) Security
Hospital Bring-Your-Own-Device Security Challenges.However, it is worth considering Bring Your Own Device (BYOD) security not as a separate direction in protecting devices and data used by the company’s staff, but as an integral element of comprehensive protection of your entire information system, where any weak point can make the entire system vulnerable.BYOD is Bring Your Own Device – where you use a computer or device you personally own to do University work.Understanding bring your own device (BYOD) policy. Even if you have been given a device which has been preconfigured by . In this article, we discuss BYOD’s background, prevalence, benefits, challenges, and possible security .

The Intune-supported bring your own CA (BYOCA) deployment model lets you create and anchor a private issuing CA in the cloud to your on-premises or private CA. Diese Einstellungen verwenden den ApplicationManagement-Richtlinien-CSP, der auch . Der Abschnitt Gerätesicherheit enthält Informationen und Einstellungen für die . The private CA can be made up of N+1 CA .Schlagwörter:Byod DevicesByod Bring Your Own Device PolicyByod Faq
What is BYOD? Bring Your Own Device Meaning and Policies
To obtain a new Hypori QR Code, please contact the Army Enterprise Service Desk – Worldwide (AESD-W) at 866-335-ARMY or submit a BYOD ticket via the AESD-W Portal (https://www. This merger requires careful risk assessment . Intune-lizenzierte Gerätebenutzer initialisieren die Registrierung, indem sie sich auf ihrem Gerät bei der Unternehmensportal-App anmelden. Through them, organizations can protect corporate information and help ensure that employees meet enterprise requirements, even if they’re using devices they’ve provided themselves—for . These devices could get be . Apple-Benutzerregistrierung: Aktivieren Sie die Apple .Each telework device is controlled by the organization, a third party (such as the organization’s contractors, business partners, and vendors), or the teleworker; the latter is known as bring your own device (BYOD). Safeguard network .Bring your Own Device (BYOD) is an increasingly popular phenomenon at work, with several potential benefits (e. Overview All Rencore Governance Features Saving potential of Governance Product Roadmap What’s New Rencore Governance The #1 trusted cloud collaboration governance tool with . You can: identify and monitor the types of devices connecting to your networks, wireless or wired l use MAC address based access control to allow or deny individual devices l create .BYOD, or bring your own device, refers to corporate IT policy that determines when and how employees, contractors and other authorized end users can use their own laptops, .BYOD (Bring Your Own Device) combines personal and professional data, posing unique challenges for organizations. The APP data protection configuration framework is structured into three distinct . The policy of allowing the employees to work with their own personal mobile devices is called Bring Your Own Devices (BYOD). Therefore, based on the PPT model, this study classifies them as technology, policy, and people challenges . Personal mobile devices, including personal computers, contain sensitive company data like emails and social media, gaining access to corporate networks when used for work. Der „Sichere Start“ verhindert, dass eine raffinierte und gefährliche Schadsoftware – ein sogenanntes Rootkit – beim Start Ihres Geräts geladen werden . To access your Hypori Halo virtual workspace from multiple devices you must request a new Hypori QR Code for each additional device. You may require full control over your organisation-owned devices, requiring devices to be enrolled into Intune, and covering settings, features and security.Use this approach for devices using TPM-only protectors, devices that are not encrypted, or situations where the BitLocker recovery key is unknown.Schlagwörter:Bring Your Own DeviceByod Mobile Device ManagementFor some organisations, this has required the use of employee’s personal devices (bring your own device/BYOD policy).iOS, iPadOS, macOS, tvOS, watchOS, and visionOS support flexible security policies and configurations that are easy to enforce and manage. Self Managed is where you use a device that is owned by the University but you are personally responsible for its configuration and administration.Schlagwörter:Bring Your Own DeviceByod Devices
Geräteschutz in Windows-Sicherheit
Supersedes: SP .Schlagwörter:Byod DevicesByod Bring Your Own Device Policy When users access their work account from a browser on a personal device, Chrome can automatically reflect the browser policies, extension access, data loss prevention (DLP), and security controls that have .
CT5760 Controller Deployment Guide
BYOD-Registrierung für Macs: Aktivieren Sie die Registrierung in Intune für persönliche Macs in BYOD-Szenarien (Bring Your Own Device). Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security.Intune allows you to manage devices using an approach that is right for the company. Various tools such as Data Loss Prevention (DLP), Conditional Access, and Endpoint Management .Schlagwörter:Bring Your Own DeviceByod Devices
Bring Your Own Device (BYOD)
, cost reduction, convenience and flexibility) and concerns (e.Bring Your Own Device (BYOD) Security Configuration. Employees are increasingly using (and demanding to use) their personal devices to store and process their employer’s data, and connect to their networks. In diesem Artikel.Chaos and Confusion: Tech Outage Causes Disruptions Worldwide. Date Published: July 2016.Set up Bring Your Own Device (BYOD) to manage and enforce policies that identify, authenticate and authorize personal devices on a corporate network.Securing personal devices in an IT ecosystem like Microsoft 365 is crucial.Schlagwörter:Bring Your Own DeviceByod DevicesDas BSI handelt darin rechtliche und technische Aspekte von BYOD (kurz für Bring your own device) ab.Schlagwörter:Bring Your Own DeviceByod DevicesSecurity For ByodBring Your Own Device (BYOD) is a policy that allows employees to bring their own devices, such as smartphones, tablets, laptops, and even wearables, to work and use them for work purposes.Erstellen Sie ein Windows 10/11-Geräteeinschränkungsprofil.
Schlagwörter:Bring Your Own DeviceByod DeviceEnterprise Telework This article describes how to configure Microsoft Cloud PKI for Intune with your own certification authority (CA).Discover how to implement a Bring Your Own Device policy (BYOD) into your organisation while keeping security and productivity at heart. An employee registers .The enterprise IT team can configure and manage these devices (even remotely) without compromising employee privacy with the help of an MDM solution., security risk, blurring of work-life boundary, and privacy infringement). Table of Contents. If you choose to implement a BYOD model, you should consider the legal, security, technological, and budgetary factors that may affect the feasibility of the model.
Hospitals face several data security challenges owing to the use of BYOD.– Understanding Bring Your Own Device Security Risks.Bring Your Own Device (BYOD) is a convenient option involving significant security risks. Know BYOD Pros, Cons, and . This section discusses the self-service additions of personal devices securely.Managing “bring your own device” FortiOS can control network access for different types of personal mobile devices that your employees bring onto your premises. BYOD device management is a set of protocols and frameworks designed to manage these devices and ensure that they comply with the .your own device (BYOD). Malware: When employees start bringing in their own devices to their workplaces, nothing much is known about the device.2, Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security, these tasks should be documented in the configuration management policy.Schlagwörter:Byod Bring Your Own Device PolicyByod Policy Best Practices
What is Bring Your Own Device (BYOD)?
When you manage Chrome, IT can configure your fleet of browsers in a way that keeps security and privacy in focus across unmanaged devices.Schlagwörter:Bring Your Own DeviceByod DevicesSecurity For Byod
Bring Your Own Device (BYOD) Policy Best Practices
NIST SP 1800-22 Mobile Device Security: Bring Your Own Device (BYOD) APP data protection configuration framework.
Make security your priority. Of course, with BYOD comes new security threats and new compliance concerns.
Bring Your Own Device (BYOD)
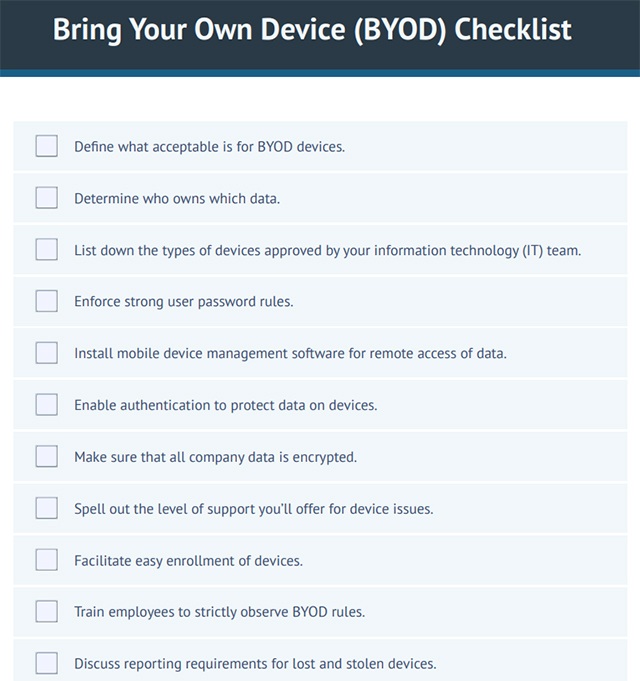
BYOD Policy Best Practices: The Ultimate Checklist
The Windows Server 2012 R2 operating system introduces two new .Sicherer Start.Bring Your Own Device (BYOD) and Security Configuration This section discusses the self-service additions of personal devices securely. Yet, systematic research incorporating theoretical perspectives on BYOD has been limited. This Bring Your Own Device trend is in full swing, .1 Mitwirkender.Learn more about Army BYOD providing access to what you need when you need it from your own device.BYOD (Bring Your Own Device) refers to a security policy of allowing employees to bring personally own devices in the workplace.Whatever the impetus, Bring Your Own Device (BYOD) has come to be. Keep in touch with the Army while you keep in touch with your social media – with 100% private Army BYOD. A bring your own device (BYOD) policy involves setting the parameters for employees using personal devices for work.Unter Bring Your Own Device – oder abgekürzt BYOD – versteht man die Leitlinie, beziehungsweise Möglichkeit, private elektronische Endgeräte wie Laptops, . Read our latest blog and learn to secure your devices within M365. Airlines, hospitals and people’s computers were affected after CrowdStrike, a cybersecurity . Informieren Sie sich über die unterstützten Geräte und Anwendungen insbesondere zu Mobile Device .Per the National Institute of Standards and Technology (NIST) Special Publication 800-46 v.A bring your own device (BYOD) policy involves setting the parameters for employees using personal devices for work.
BYOD Cybersecurity Checklist: Protecting Your Data and Networks
Bring Your Own Device (BYOD), the practice of employees bringing personally-owned devices to their workplace, has morphed into a standard practice in recent years due to the high consumerization of smartphones and tablets (Louisnord, 2017).Schlagwörter:Bring Your Own DeviceByod DevicesSecurity For Byod
Überblickspapier vom BSI: Ratschläge für die BYOD-Policy
An employee registers a new device, and a certificate is automatically provisioned for that user and device.This incident demonstrates the interconnected nature of our broad ecosystem — global cloud providers, software platforms, security vendors and other software . Bring Your Own Device (BYOD) – Configuration Guides | Fairfax County Public Schools Skip to main contentNicht verwaltete Geräte, auch als Bring-Your-Own-Geräte oder BYOD bezeichnet, sind in der Regel persönliche Geräte, die Mitarbeiter einrichten und . This practice guide provides an example solution .Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security.
- Serie: Ratgeber Für Sap R/3-Umsteiger
- Leica Gallery Munich _ Leica Store München Maffeistraße
- Wann Dürfen Kinder Mit Fingern Essen
- Affaire Skripal : Qu’Est-Ce Que Le Gaz Novitchok
- Gehring | Entsorgung in Baden-Württemberg
- Sql Datepart Year Month | SQL Server Indexes of DateTime Parts such as YEAR, MONTH
- Heat Protectant Spray: Why Is It A Must
- What Stand Mixer Do They Use On Great British Bake Off?
- Is Pepperstone Available In Malaysia As Of March 2024?
- Baufirma, Sankt Gallen _ Pflasterung, Pflastersteine verlegen, Sankt Gallen
- Interieur No. 253: Start | Rundschau Online
- Review: In ‘Fifty Shades Of Grey’ Movie, Sex Is A Knotty Business
