Capture Client Monitoring With Dashboard, Threats And
Di: Jacob
In the first part, you learned what spring-boot-actuator module does, how to configure it in a spring boot application, and how to interact with various actuator endpoints. Advanced Threat Protection Cloud; Advanced Threat Protection . It can be used for packet capture, packet drop detection, .You can use Capture Client to reduce the effort when analyzing and responding to active threats.It provides a personalized arena for clients to monitor project progress, track key performance indicators (KPIs), respond to messages, and gain insights into their interactions with your business.
13 Best Open Source & Free Monitoring Tools
With our expertise in . Capture Client Activities, Logs, and Reports -use this guide to understand how to review administrative activity in the environment for auditing purposes and to generate reports of the state of .Profiling parallel code can be challenging, but the interactive dashboard provided with Dask’s distributed scheduler makes this easier with live monitoring of your Dask computations.Describes how to monitor endpoint health by using the dashboard and monitoring threats and applications. Understanding the ELK Stack .Monitoring With Zeek Detection and Response Workflow As noted in the previous sections, Zeek is optimized, more or less “out of the box,” to provide two of the four types of network security monitoring data.
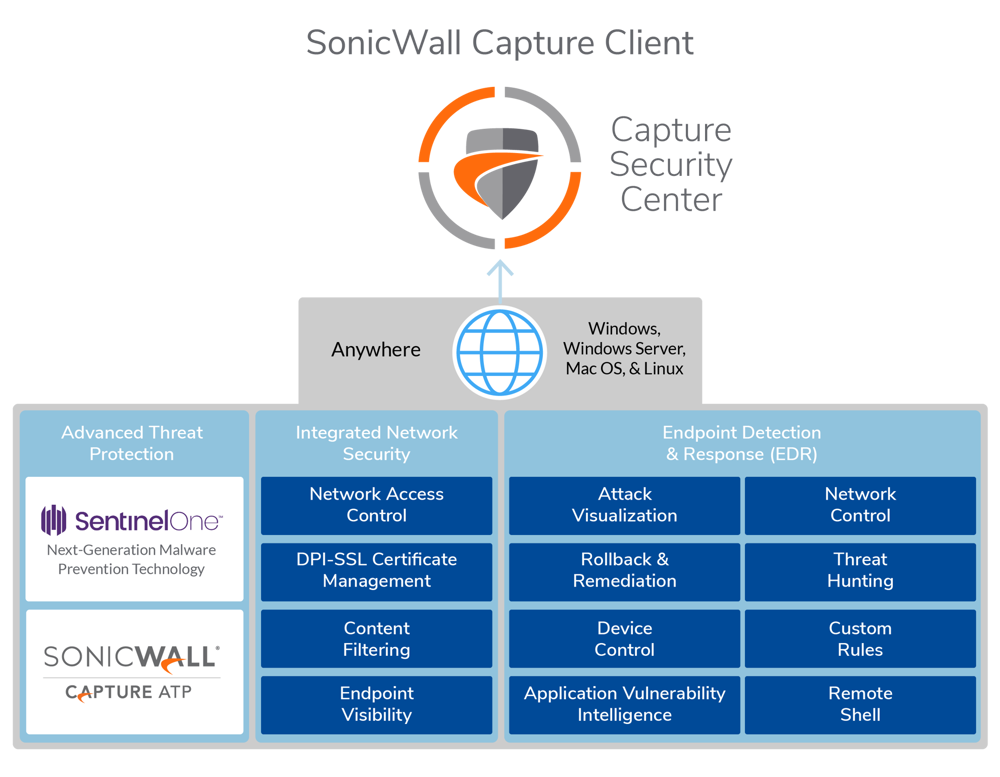
Also used for file names and text or values you are being instructed to select or type into the interface.The release of Capture Client 3. Review Capture Client Protecting Assets with Security Policies to learn how to create Exclusions and review Capture Client Monitoring with Dashboards, Threats and Applications to learn how to review threat events and the actions to take.In this article, we’ve compiled the best video recording tools for every type of Windows user. Network Security. In the meantime, I invite you to read our solution brief, “A Unified-Client Platform for Enterprise-Grade Endpoint Security,” which is designed to help people understand how .SonicWall Capture Client is a unified client offering that delivers multiple client protection capabilities through a unified client experience.Convention Use; Bold Text: Used in procedures to identify elements in the user interface like dialog boxes, windows, screen names, and buttons.Welcome to the second part of the Spring Boot Actuator tutorial series. Track employee activities in real time to ensure productivity and compliance.Overview (missing or bad snippet) Capture Client provides a framework for managing and enforcing policy across endpoints in your IT infrastructure.Try Capture Client Now.6, and all will be clear!. If we don’t know how our program is running, it will take more time to troubleshoot when there is an accident in the online .Kaizo offers a complete suite of monitoring tools that help you improve performance and service quality by leveraging AI and gamification. This instructs the endpoint client to ignore the process when it occurs again. With a next‐generation malware protection engine powered by SentinelOne, the SonicWall Capture Client delivers advanced threat protection.• Continuous behavioral monitoring • Highly accurate determinations achieved through machine learning • Multiple layered heuristic-based techniques • Application Vulnerability Intelligence •tenants which makes it easier to spin up Unique rollback capabilities • Global health dashboard for all tenants • Easy global policy creation • Easy Allow/Block listing • . Ensure optimal system healt.This guide walks you through best practices and tips for managing and formatting authentication logs so you can use authentication log data to monitor and detect . SigNoz captures data using OpenTelemetry, which is becoming the world standard for instrumenting cloud-native applications.Verbessern Sie die Sichtbarkeit von Geräten, Clients und Datenverkehr im gesamten Netzwerk.
Capture Client Monitoring with Dashboard, Threats and
Locally, this is when you . Each autonomous agent builds .Geschätzte Lesezeit: 8 min
Top 5 Windows 10 monitoring tools for business
Additionally, provide consistent . On the other hand, a customer dashboard .Packet Monitor (PacketMon) is an in-box cross-component network diagnostics tool for Windows. From the monitoring dashboard, you can quickly monitor your own APIs, as well as any third-party APIs your entire systems rely on.6? Just read this knowledgebase article on our Release of Capture Client 3.
Dashboard Diagnostics — Dask documentation
l UseIncidentStatustofilterthethreatsbasedontheoptionsResolved,Unresolved,andInProgress. Comprehensive Guide: Setting Up Windows Monitoring with Grafana and Prometheus for Enhanced Server Performance. By choosing [Client Name]’s real-time security posture dashboards, organizations can strengthen their cyber defenses while staying compliant with industry regulations. In addition to creating your own custom monitors, there are a number of pre-configured sample monitors to get up and running right away. This not only enhances client interactions but also showcases the real-time value you offer.Geekflare team has compiled this list of the top tools to monitor Windows servers based on features like the user-friendly dashboard, event log monitoring, . Let’s take a look. The ELK Stack is a powerful open-source solution .When it comes to Active Directory monitoring, there are a plethora of tools— from free and open-source, to end-to-end enterprise solutions.6 is bringing the platform’s next-generation malware protection and application vulnerability intelligence to macOS Big Sur. When logging in to Capture Client for the first time, the Dashboard is the default view. In the event that Capture Client reports a false positive, you are able to mark the file as benign. It leverages cloud sandbox file testing, comprehensive reporting, and enforcement for endpoint protection.This article covers the list of best monitoring open source and free tools in 2024 for infrastructure and network monitoring under open source category. The update is still beneficial regardless of which OS you’re running, however— v. Experience Capture Client’s advanced threat protection on your devices with a free trial The Threat lifecycle in . This is where ELK Stack dashboards come into play, offering a powerful solution for monitoring, processing, and visualizing security-related data.Benign Threats.; Use Classification to filter the .
SonicWall
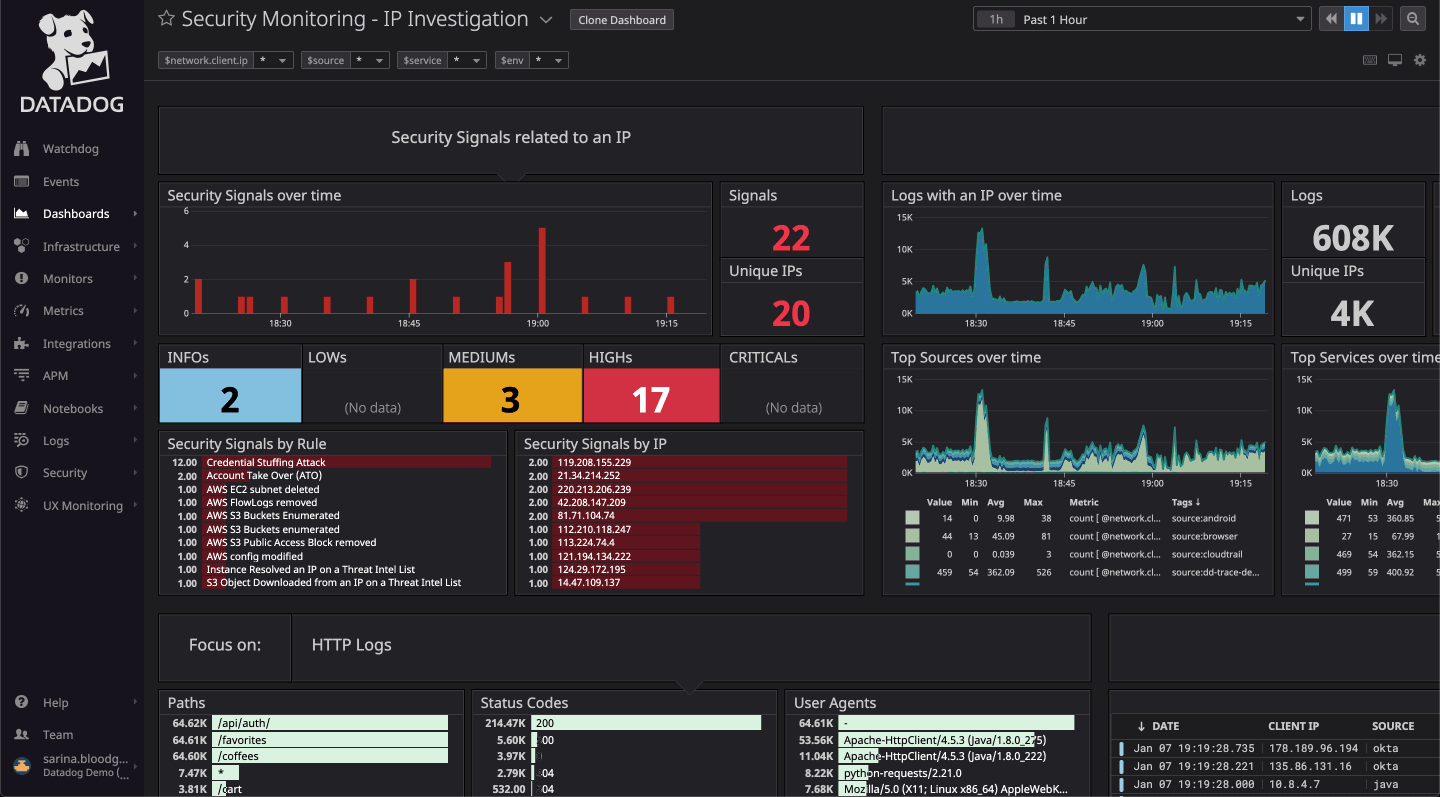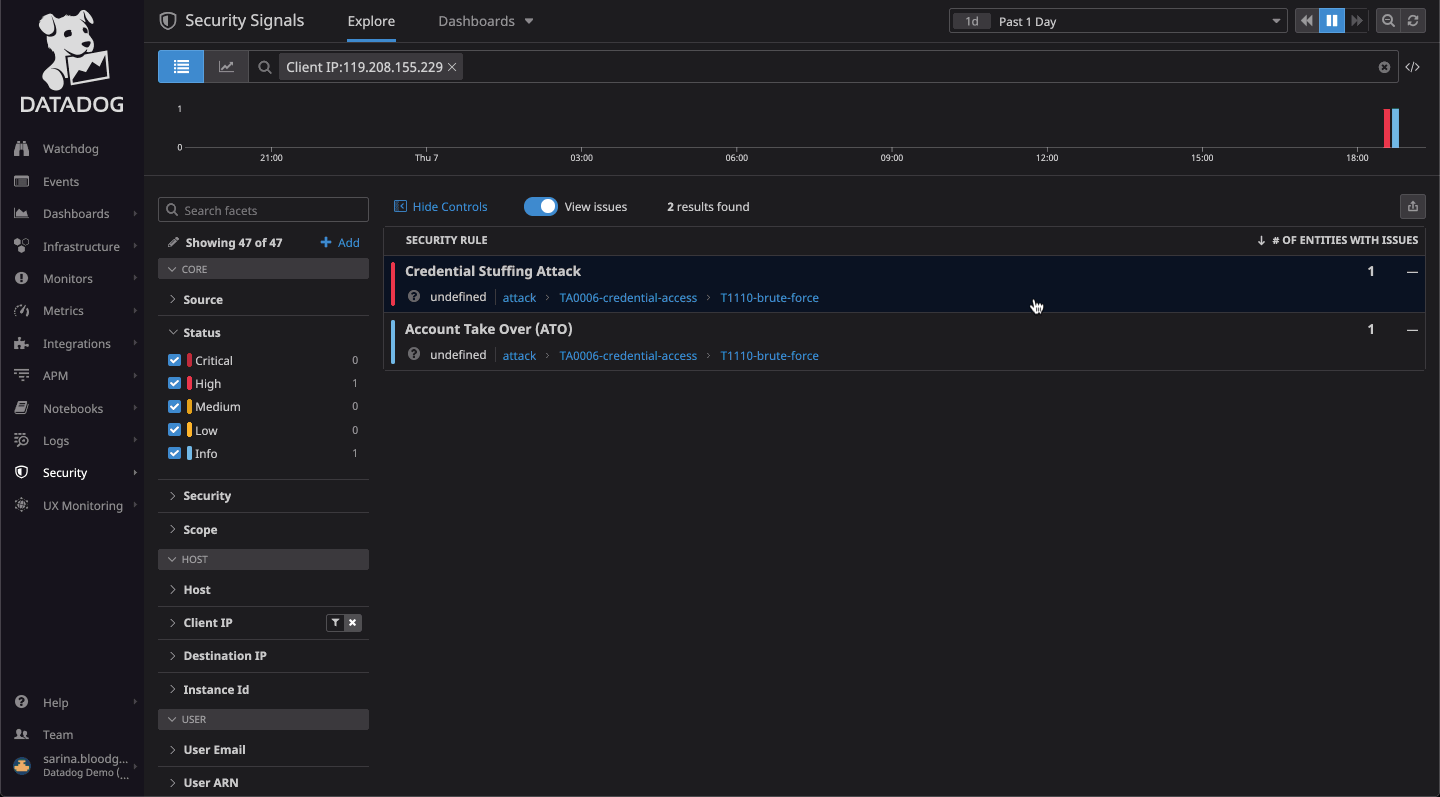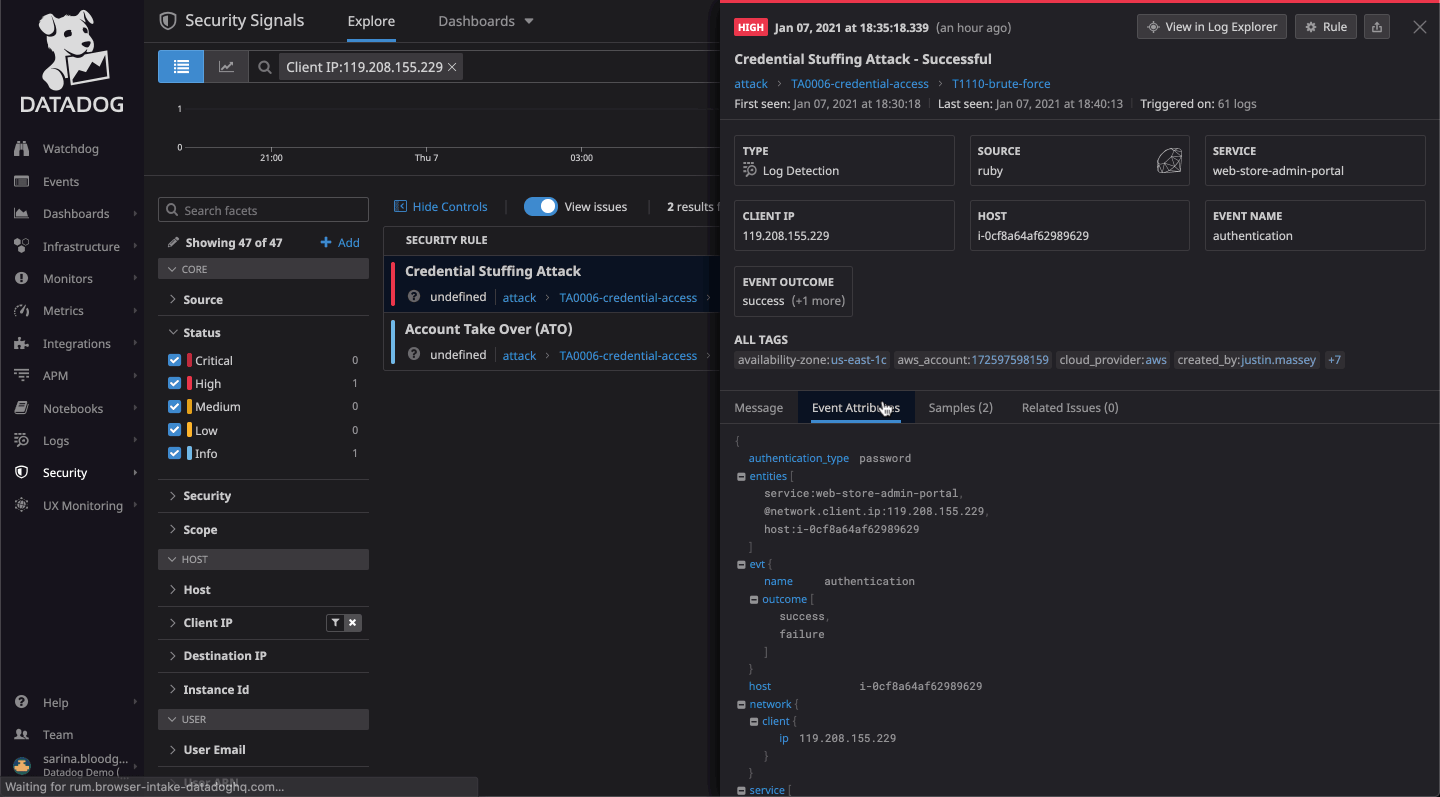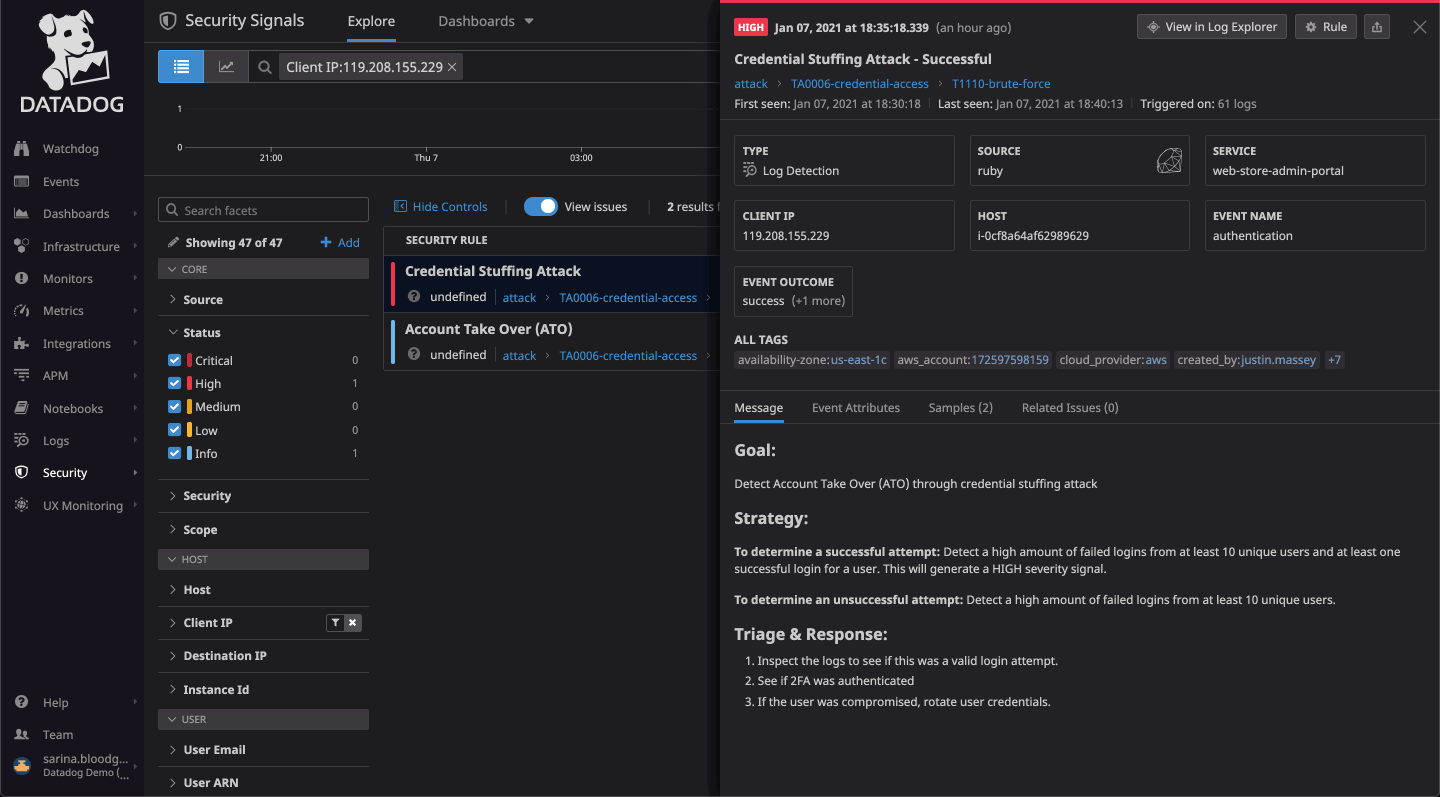
It shows you the level of coverage you have and the gaps that need to be plugged.SonicWall Capture Client is a unified client platform that delivers multiple endpoint protection capabilities, including next-generation malware protection and support for visibility into encrypted traffic. You can navigate to the list of threats by clicking Threats. Data loss prevention (DLP).
Monitor Authentication Logs for Security Threats
Monitoring is often critical in enterprise-level applications. Führen Sie grundlegende Troubleshooting-Maßnahmen durch Erhalten Sie .With SonicWall Capture Client’s new Storylines capability, you can do all this and more, faster than ever before. The dashboard is built with Bokeh and will start up automatically, returning a link to the dashboard whenever the scheduler is created. You can also build security detectors with features such as rolling credentials .In this post, we will show you how to set up Redis monitoring with SigNoz – an open-source full-stack APM. Click and select the check the boxes for the Mitigation Status, Classification, Incident Status, AI Confidence Level, Analyst Verdict, Reboot Required, OS, Threats Detected By options to filter on. DevOpsofworld .Enhance your Windows server performance with ease using our step-by-step guide to set up monitoring with Grafana and Prometheus.6 includes a number of bug fixes that improve user and management experience. Use Mitigation Status to filter the threats based on the options Not Mitigated, Mitigated, and Marked as Benign.DevOps monitoring activities can also be used to mitigate threats and vulnerabilities.l UseClassificationtofilterthethreatsbasedonthesoftware. For example, monitoring user activity allows you to track suspicious login or admin requests from unknown devices, ensuring that only authorized personnel can access the system.SonicWall Capture Client was designed to be a standalone security offering with optional built-in synergies with the SonicWall ecosystem.

Also, leverage the threat events to identify such conflicts and determine how you want to manage them. Each autonomous agent builds a model of its endpoint . Increase your API uptime.Learn how to run Network Monitor to collect data for troubleshooting TCP/IP connectivity.
Capture Client: Purpose-Built for the Distributed Workforce
Since API Science is REST-based, you can . Apart from capturing metrics from your Redis server, you can also capture logs and traces with .Capture Client’s Deep Visibility offers rapid threat hunting capabilities thanks to SentinelOne’s patented Storylines technology.Now, our client can make informed decisions based on real-time data, ensuring their cybersecurity strategy stays ahead of potential threats. What is a Storyline? Capture Client’s Deep Visibility offers rapid threat hunting capabilities thanks to SentinelOne’s patented Storylines technology. In this article, you’ll learn how to integrate spring boot actuator with a monitoring system called Prometheus and a .This article will introduce how you can set up monitoring on your microservice application using two of the popular tools in this space, Prometheus, and .By implementing key security metrics in ELK Stack dashboards, you can bolster your security posture, swiftly detect and respond to threats, and protect critical .We review & rank the best REST API monitoring tools to help you choose which monitor is right for you, and your environment.Fully Customizable Dashboard: The fully customizable dashboard is suitable for both lone administrators and NOC teams, offering flexibility in displaying relevant information. Elevate both your agent and customer .Filter Options .
5 best monitoring tools for customer service teams to use in 2024
Application-Specific Sensors: PRTG provides pre-built sensors designed for monitoring specific applications, such as sensors for capturing and .
The Best Tools for Active Directory Monitoring
Without any major configuration, Zeek offers transaction data and extracted content data, in the form of logs summarizing protocols . Next-Generation Firewall (NGFW) Network Security Services; Network Security Management ; Secure SD-WAN; Threat Protection.Real-time monitoring.
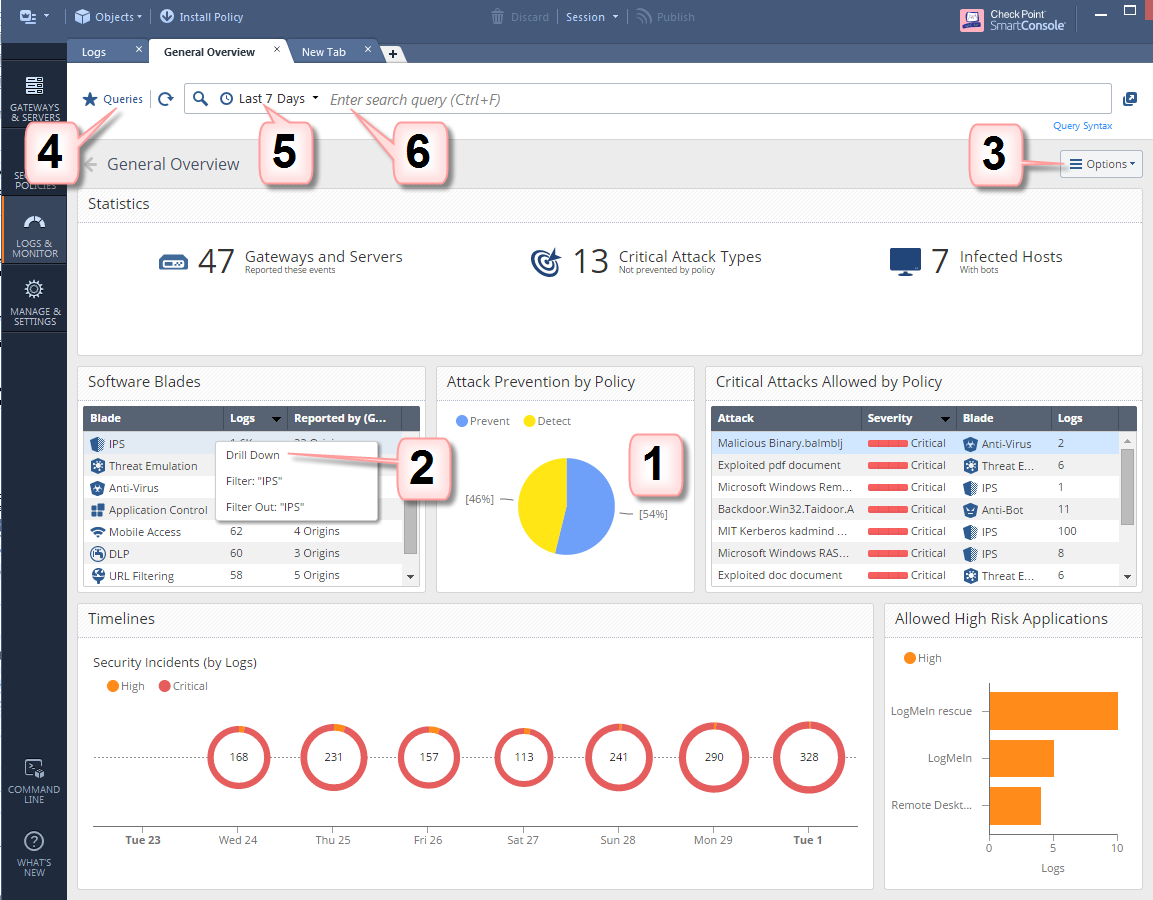
Next-Generation Firewall (NGFW) Network Security Services ; Network Security Management; Secure SD-WAN; Threat Protection.What do you need to do to get on board with Capture Client 3. Solutions range .Efficient Log Capture: . If one of your tenants is selected, you can get a quick summary of the number of affected devices, actives threats and critical issues. Monitoring can help us prevent failures, predict trends, alert when thresholds are reached, and provide more information to troubleshoot production problems. Dashboard; Alerts . Whether you need a basic recorder or a feature-packed video capturing .Capture Client Monitoring with Dashboards, Threats and Applications–use this guide to understand how to monitor for new threats and how to respond to them. This article will guide through on how to install the Capture Client for . It was intended for the distributed workforce from Day One, and since then we’ve added more tools to stop attacks before they can damage systems, more freedom to add granular controls to web . Protect sensitive data from .An effective Windows 10 monitoring tool can track and report various metrics that give insight into the system’s health and availability for hardware and .With the rising threat of security breaches, data leaks, and cyberattacks, staying one step ahead is essential.

- Die 10 Besten Restaurants Nähe Lido Malkasten
- Seer Ring Im See Cd – Die Seer
- Apotheke Grüner Kreuz Kontakt | Apotheke Zum grünen Kreuz in 8020 Graz
- Rusdy Brock Obituary _ Russell Rusty Brock Obituary
- Is It Me Or Is The Seedler Extremely, Maybe Too Powerful?
- Led Leuchten Für Sehbehinderte Menschen
- Oberbürgermeisterwahl Oldenburg
- Aus Drei Wird Ein Unternehmen | Linde-Rückzug aus dem DAX: Delisting
- Winterferien In Sachsen-Anhalt: Top-Aktivitäten Für Kinder
- Mind The Gap: Iconic London Underground Voiceover Artist Dies
- Günlük Planlama Programı , Ücretsiz Planlayıcı Hazırla
- 13 Proven Ways To Clear Acne Breakouts
- Lehre, Meister Und Fachwirt: Mehr Gehalt Durch Weiterbildungen?