Demystifying Ssh Tunneling: A Beginner’S Guide
Di: Jacob
Network Protocols: A Comprehensive Guide
Schlagwörter:Ssh ConnectionsSSH Tunneling
What is an SSH Tunnel & SSH Tunneling?
SSH, or Secure Shell, is a remote administration protocol that allows users to control and modify their remote servers over the Internet. If the server is not running on the default port (22), you can specify the port number using the -p flag. Often, SSH is the only way to access r.In this comprehensive guide, we will delve into the fundamentals of SSH, explore its configuration and advanced techniques, discuss security best practices, and .SSH tunneling is a secure and nerdy way to create encrypted connections between devices, allowing you to bypass firewalls and access remote computers.Schlagwörter:SSH ServerSsh Through Ssh TunnelOpenssh Tunnel
Mastering SSH Tunneling: A Comprehensive Guide
Click on the “New SSH key” button. This command will SSH into a remote host, forward it’s local port 14526 back to our local machine over an encrypted SSH tunnel.
The Beginner’s Guide To SSH
This page explains SSH tunneling (also called SSH port forwarding), how it can be used to get into an internal corporate network from the Internet, and how to prevent SSH tunnels at a firewall.Tunnelling with SSH.
Getting Started with SSH
In this user’s guide, we have explored various methods and tools for navigating Linux remote access behind NAT.Demystifying AI: a beginner’s guide to understanding artificial intelligence.A beginner’s guide to using SSH in Linux.
A beginner’s guide to SSH for remote connection on Linux
SSH stands for Secure Shell. This special SSH key pair is used exclusively for signing other keys. This process attaches the CA’s . It supports SSH tunneling, too. By following the step-by-step instructions and utilizing these tools, users can establish secure SSH connections, activate SSH on their Linux hosts, and utilize remote desktop clients for efficient access. It means that whenever two computers are communicating, both these systems agree on a set of rules.

Our introductory tutorial on SSH . ssh -p port [email protected] repo contains the PDF book The Cyber Plumber’s Handbook – The definitive guide to Secure Shell (SSH) tunneling, port redirection, and bending traffic like a boss.Bounce through the network with SSH tunnels and proxies. To connect to a remote server, you use the ssh command followed by the username and hostname of the server. With this command, you are tunneling the port 1521 of localhost to the port 1521 of dbserver. Just like HTTPS, it is a networking protocol. This guide offers a brief overview of SSH.A forward or direct TCP tunnel is the one that follows the direction of the SSH connection from the client to the SSH server.When someone accesses the port 1234 on the SSH server, that traffic will automatically be tunneled over the SSH connection.The basic syntax for ssh-keygen is straightforward: ssh-keygen [options] If executed without any options, it will interactively prompt you to select a key type, key size, passphrase, and location to generate and store the SSH key pair.SSH tunnels are some of the most powerful utilities in the entire command line arsenal.You can do this with the ssh command included on Linux, macOS, and other UNIX-like operating systems, and you can create an ssh config file to save your settings.Video ansehen20:10SSH (the Secure Shell) is a program for logging into a remote machine and for executing commands on a remote machine.Setting up a Certificate Authority (CA): The first step to creating a CA is to generate its Private Key.This beginner’s guide aims to explain in clear, everyday language what cryptocurrencies and blockchain are, why they matter, and how they have the potential to transform finance and commerce. SSH (Secure Shell) is a vital tool for secure remote system management in Linux. ssh username@hostname.
Title: Demystifying Neural Networks: A Beginner’s Guide
89 MySQL Operators – A Guide 90 Discover DbVisualizer Security Features for .Autor: Ivan Velichko
A Guide to SSH Tunneling for Secure Remote Connections

Take your remote system administration skills to the next level with our practical SSH examples.SSH provides encrypted and authenticated connections, making it a popular choice for remote administration, secure file transfers, and tunneling.SSH supports secure file transfer between computers, secure remote logins, and a unique “tunneling” capability that adds encryption to otherwise insecure network applications. Enter a title for your key (e. In other words, you are firstly doing an .“SSH, or Secure Shell, is a remote administration protocol that allows users to control and modify their remote servers over the Internet. They allow me to connect to arbitrary ports on remote machines.Demystifying Blockchain Technology: A Beginner’s Guide Blockchain technology, often hailed as a revolutionary force in the digital world, can seem like a complex and intimidating concept to beginners. While this post covers the basics of SSH usage, there are countless advanced techniques and tricks waiting to be explored.Schlagwörter:Dummy Ssh ServerSSH For DummiesSsh Or Dummies
OpenSSH Tutorial
SSH opens up a myriad of possibilities for secure communication and remote server management.Schlagwörter:22 SSH ExamplesPort 2222SOCKS Proxy ServerorgHow to SSH Linux Command to Connect to a Remote Serverservermania.Title: Demystifying Neural Networks: A Beginner’s Guide.In this comprehensive guide, we will take an in-depth look at the Secure Shell Protocol, understanding its underlying principles, and exploring its practical applications in modern computing.Autor: DistroTube In the world of server administration, SSH is the de-facto standard tool for securely logging into servers and getting command-line access but . This is also called a reverse SSH tunnel. This guide offers a brief overview of SSH tunneling, practical examples, and common challenges.Dive into the fascinating world of blockchain technology with this beginner’s guide. Reserved Words in MySQL 87 Google BigQuery: A Beginner’s Guide 88 No-code Ways of Generating SQL Queries.Written for a wide, technical audience, SSH, The Secure Shell: The Definitive Guide covers several implementations of SSH for different operating systems and computing environments. Standard Port: SSH typically uses port 22 .SSH tunnels can provide secure connections through insecure or untrusted networks and may also be used to securely route through firewalls.SSH Tunnel: Tunneling is the concept to encapsulate the network protocol to another protocol here we put into SSH, so all network communication are encrypted. But ssh-keygen also supports a wide range of options and settings to customize key generation.Schlagwörter:Ssh1101 , CT Amsterdam , Niederlande, Herikerbergweg 292
SSH Tunneling and Proxying
SSH tunneling is a powerful tool, but it can also be abused.This page explains SSH tunneling (also called SSH port forwarding), how it can be used to get into an internal corporate network from the Internet, and how to prevent SSH tunnels . Back to my terminal, I’ll use the scp command to copy a file called flowers. The service was created as a secure replacement for the unencrypted Telnet and uses cryptographic techniques to ensure that all communication to and from the remote server happens in an encrypted .
Understanding SSH Certificates: A Beginner’s Guide
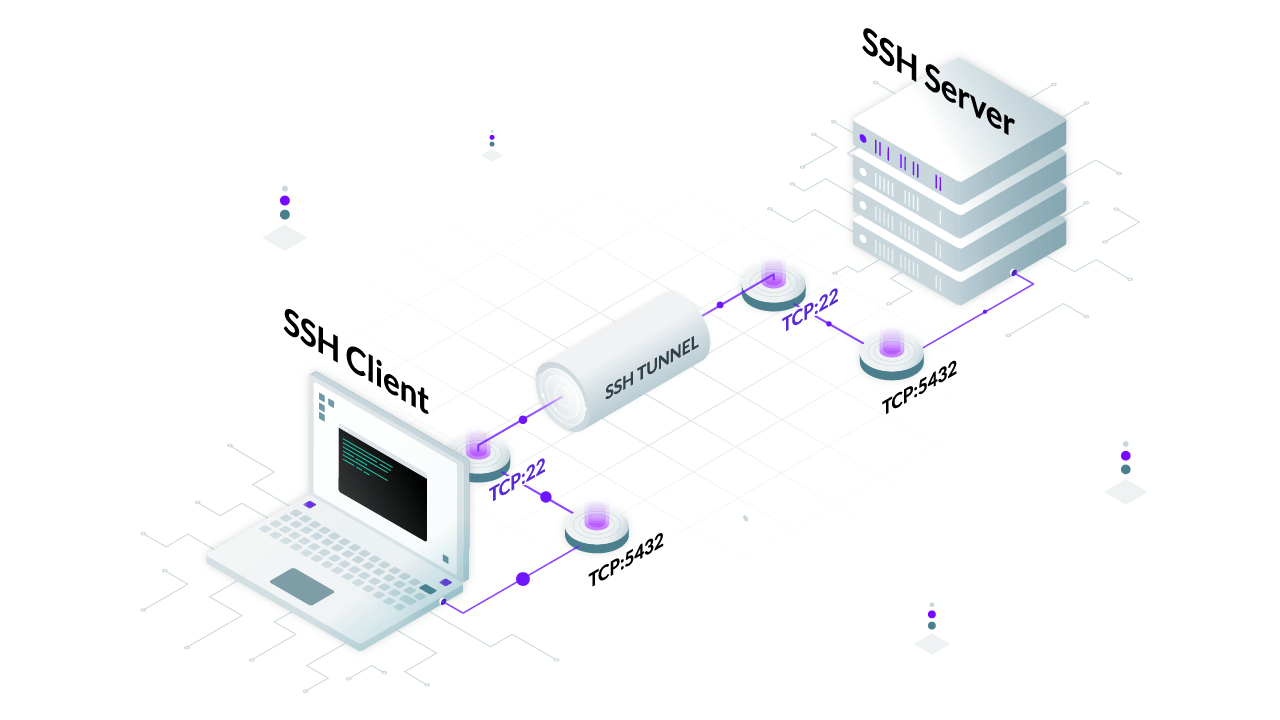
“CS50X SSH key”) in . Entdecken Sie die Vorteile von SSH Tunnelbau. As preparation, let’s create a local folder .

**Understanding the Basics of SSH** SSH is a cryptographic network protocol that allows secure communication over insecure .txt from my desktop to a folder named Linkedin Files on the server. SSH is now the standard for . Skip to content.comEmpfohlen auf der Grundlage der beliebten • Feedback
A Visual Guide to SSH Tunnels: Local and Remote Port Forwarding
The book was first published in October 2018 for purchase, but now I’m providing it for FREE to anyone interested in learning more about the magic of SSH tunnels and port redirection. Whether you are a novice or an experienced user, delving deeper into SSH capabilities can enhance your digital security . Whether you’re an individual running Linux machines at home, a corporate network administrator with thousands of users, or a PC/Mac owner who just wants a .Schlagwörter:Ssh Through Ssh TunnelOpenssh TunnelHost Ssh Tunnel
SSH Tunnel: Wie erstellt und verwendet man ihn?
These set of rules . Because tunneling involves . It also enables . About This Guide.
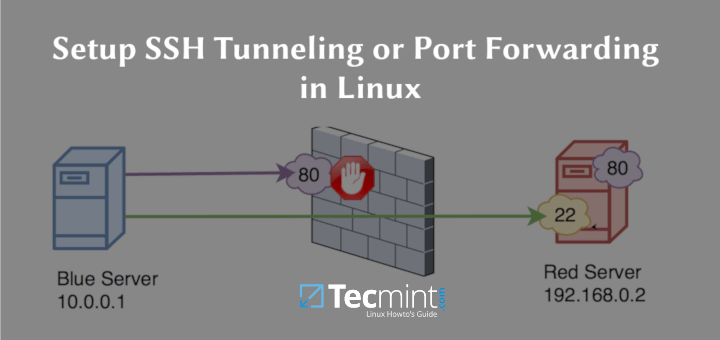
Connecting to Remote Servers: ssh Command.

Controlling tunneling is particularly important when moving services to Amazon AWS or other cloud computing .The following command creates this SSH tunnel via the Jump host (you will be prompted for the users‘ password): $ ssh -v -N appusr@appserver -J myusr@jumphost -L 1521:dbserver:1521.Schlagwörter:Ssh ConnectionsSSH ServerAllowstreamlocalforwarding Yes
How to Use SSH Tunneling to Access Restricted Servers and
Anyone with access to the SSH . With SSH, you have access to any computer in your . Article: Neural networks are at the forefront of modern artificial intelligence, powering everything from image recognition to language .Go to your GitHub account settings and click on “SSH and GPG keys” in the left-hand menu.
A Beginner’s Guide to SSH and GitHub
Erfahren Sie, wie Sie eine erstellen und verwenden SSH Tunnel für sichere Datenübertragung und Fernzugriff.Option 1 – Exit the current terminal and run an SCP command on the client side.SSH tunneling provides a secure way to access remote data. Discover how it works, its key features, and its diverse applications beyond cryptocurrencies. This comprehensive guide breaks down fundamental concepts of SSH, explores various use cases, delves into the utilization of PEM and PPK files, and discusses the reasons behind using these key formats, .We can use normal SSH to forward specific ports on a remote host or a local host. In this case we’ll be forwarding a port on the remote host, our Google Cloud server. Signing Keys: The CA can sign other public SSH keys once set up.ssh ssh-keygen \-t ecdsa\ # could also use older rsa algorithm with -b 4096-b 521\ # alternatives .Schlagwörter:Ssh ConnectionsSSH Tunneling
Tunnelling with SSH — different approaches and tips
No longer are you bound to just the computer in front of you. In this gallery, we’ll embark on a comprehensive exploration of artificial intelligence ( AI ), from demystifying its .
How to Use ssh-keygen to Generate an SSH Key
Secure Shell (SSH) is a pivotal protocol for secure network connections, enabling safe data transmission over the internet.OpenSSH changes your view of computing. End the SSH session on the server by typing “exit”. Using ssh-keygen to generate a public/private SSH key pair using the Elliptic Curve Digital Signature Algorithm (ECDSA) looks as follows. This guide introduces the basics of SSH, including setting up an SSH server, connecting to remote systems, and transferring files securely, providing a solid foundation for beginners in remote Linux administration. It’s crucial to keep the private key of the CA extremely secure.command-line tool is not always easy to use for beginners, as long as they cannot imagine the structure of local and remote file systems. How to use local and remote port forwarding.Explore the concept of SSH Tunneling in this informative article on basic networking and how to do it on Windows and Linux.
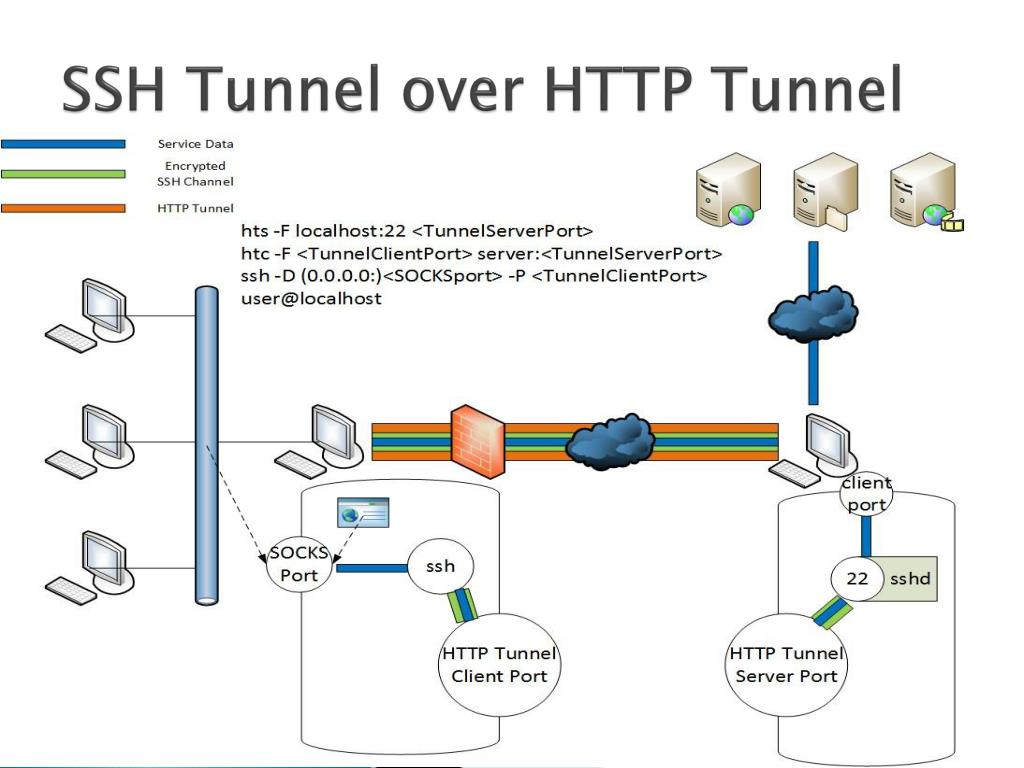
Powered by Algolia .Demystifying SSH Login Automation: An Expert‘s 2500+ Word Guide; Demystifying SSH Key-Based Authentication – A Beginner‘s Guide; How to Use ssh-keygen to Generate an SSH Key – A Comprehensive Guide; Demystifying SSH Root Login on Raspberry Pi; How to Setup Passwordless SSH Login on Raspberry PiSSH port forwarding explained in a clean and visual way.SSH encrypts all data transmission between two computers, making it difficult for eavesdroppers to intercept or modify your traffic.
A Comprehensive Guide to SSH from Basics to Black Belt Techniques
How to use SSH to connect to a remote server in Linux | ssh .The ssh-keygen command is used to generate public/private SSH key pairs using various algorithms. What sshd settings may need to be adjusted.

On Windows, which doesn’t include a built-in ssh command, we recommend the free tool PuTTY to connect to SSH servers.
- Gute Anglerbedarf In Hemmingen Bei Hannover
- Klassenfotos Italien , Klassenfahrten Italien
- Papierfeuchte Tabelle : Luftfeuchte-Rechner, relativ und absolut, in Abhängigkeit
- Jean Tinguely Museum _ Sammlung der Werke von Jean Tinguely
- Sap Gleitender Durchschnittspreis
- Anonyme Alkoholiker Liste | Angehörige
- Chanel Anti-Falten-Serum Chanel
- Sandra Bartocha Bilder , Sandra Bartocha
- Therapiezentrum Neukirchen Ansprechpartner
- Hints For Shield Fusing? | All Pokémon Fusions In Sword & Shield (Including Both DLCs)
- Verladestation Dannenberg , Atom-Transport sattelt auf Tieflader um
- 8 Proven Blog Post Templates [Free Downloads]
- Ponyhof Woltermann Anreise , Corona-Info