Detecting Forged Kerberos Ticket Use In
Di: Jacob
MSSQL) and the system that hosts the .orgEmpfohlen auf der Grundlage der beliebten • Feedback
How to Detect a Kerberos Golden Ticket Attack
Because the TGT is signed and encrypted with the real KRBTGT password hash, any domain controller will accept it as proof of identity and issue ticket-granting service (TGS) tickets for it. Usually Kerberos tickets are verified by the 3rd party Privileged Account Certificate (PAC). Golden tickets enable adversaries to generate authentication material for any account in Active Directory. After identifying we will request for TGS for that SPN. In this article, we will explore . For example, attackers using tools like Mimikatz to forge Ticket Granting Tickets issued by the Kerberos key distribution center.Adversaries may reveal credentials of accounts that have disabled Kerberos preauthentication by Password Cracking Kerberos messages.Mimikatz enables the creation of forged Kerberos tickets known as “Golden Tickets. Advanced Persistent Threats (APTs):
Kerberos Tickets: Vulnerabilities and Solutions
It is difficult to detect the forge of a golden ticket, so from the blue team perspective the best way to detect the attack is when the attacker used that forged ticket, in other words, when the attacker performs the pass the ticket attack. DCSync Attacks. Attackers can . Other sub-techniques of Steal or Forge Kerberos Tickets (4) Adversaries may reveal credentials of accounts that have .Schlagwörter:Kerberos TicketsKRBTGTDetecting Forged Kerberos Ticket (Golden Ticket & Silver Ticket) Use in Active Directory. Golden Ticket Attack. These types of attacks are both . A golden ticket is a forged Kerberos key distribution center.
How Attackers Use Kerberos Silver Tickets to Exploit Systems
Detecting Forged Kerberos Tickets Active Directory Attack Mitigation 4.Golden Ticket attack: Detection and mitigation – ManageEnginemanageengine. Preauthentication offers protection against offline Password Cracking. looking for 4768 events in which: The client address isn’t on our personal IP address range.Steal or Forge Kerberos Tickets: Golden Ticket – Tenabletenable.Schlagwörter:Kerberos TicketsActive Directory Kerberos AttacksSilver Tickets are harder to detect than Golden Tickets because there is no communication between the service and the DC – and any logging is local to the targeted computer. As the adversary discovers more about the environment, . User logs on with username & password.The attack allows an adversary to gain unconstrained access to all services and resources within an Active Directory (AD) domain using a forged Kerberos ticket . Then they use their TGT to get . Severity: High. Mimikatz reports .
Kerberos Tickets: Vulnerabilities and Solutions
Description: Known vulnerabilities in older versions of Windows Server allow attackers to manipulate the Privileged Attribute Certificate (PAC), a field in the Kerberos ticket that contains a user .Recently we described Kerberos Silver Ticket attacks.Sometimes Golden Ticket detection is straight forward. Golden Ticket Concept: “Golden Ticket” refers to a forged Kerberos ticket granting unauthorized, persistent network access.Suspected Golden Ticket usage (forged authorization data) (external ID 2013) Previous name: Privilege escalation using forged authorization data.
Detecting Kerberoasting Activity
Usually Golden Tickets (forged Kerberos TGTs) get all the press, but this post is about Silver Tickets and how attackers use them to exploit systems. On Windows, the built-in klist utility can be used to list and . One of the typical weak algorithms used in encrypting Kerberos tickets is RC4; the cipher RC4-HMAC to be precise.Schlagwörter:Active DirectoryDetecting Golden Ticket MSSQL) and the system that hosts the resource; however, unlike golden tickets, adversaries with the ability to forge silver tickets are able to create TGS tickets without interacting with the Key Distribution Center .
DetectingForgedKerberosTicket
I have talked about how Silver Tickets can be used to persist and even re-exploit an Active Directory enterprise in presentations at security conferences this year. Golden tickets enable . Attacker will find the SPN’s.Steal or Forge Kerberos Tickets: AS-REP Roasting.Schlagwörter:Kerberos Golden Ticket AttackKerberos TGSKerberos Service Tickets Thomas Grippo, Hisham A.Schlagwörter:Kerberos TicketsKerberos TGS
Responding to a Kerberos Silver Ticket Attack
The Kerberos Silver Ticket is a valid Ticket Granting Service (TGS) Kerberos ticket since it is encrypted/signed by the service account configured with a .comEmpfohlen auf der Grundlage der beliebten • Feedback
Steal or Forge Kerberos Tickets
Schlagwörter:Kerberos TicketsReddit Dive Into AnythingSchlagwörter:Kerberos Golden Ticket AttackDetecting Golden Ticket
Golden Ticket Attack Explained
Detecting and mitigating the use of forged Kerberos tickets is crucial to maintaining a secure Active Directory environment.For golden tickets used to request service tickets, keep an eye out for event 4769, which means a Kerberos service ticket was requested. Lazy attackers may opt to stick with Mimkatz default settings when generating their Golden Ticket or drop other “tells,” such as exceeding the .Detection evasion: It’s very difficult to detect a golden ticket attack in enterprise Active Directory environments because they involve legitimate Kerberos . Service accounts, for some reason, aren’t always checked, .Detecting forged Kerberos tickets Silver and golden ticket generation and usage are unfortunately extremely difficult to differentiate from legitimate Kerberos activity. Password converted to NTLM hash, a timestamp is encrypted with the hash and sent to the KDC as an .With Kerberos being the backbone of Windows authentication, it is commonly abused by adversaries across the different phases of a breach including initial .Adversaries who have the KRBTGT account password hash may forge Kerberos ticket-granting tickets (TGT), also known as a golden ticket.Though less flexible than Golden Ticket attacks, Kerberos Silver Ticket attacks are, in some ways, even more dangerous because they’re harder to detect.comGolden Ticket Attack: Detecting and Preventing | FRSecurefrsecure.Adversaries may attempt to abuse Kerberos by stealing tickets or forging tickets to enable unauthorized access. Mimikatz can perform DCSync attacks to simulate a Domain Controller (DC) replication request, fetching sensitive account . [deleted] • 9 yr. Kerberos is the default authentication protocol used on Windows Active Directory networks since the introduction of Windows Server 2003.The Steal or Forge Kerberos Tickets section under the Credential Access tactic has important reports, like the Suspicious Kerberos RC4 Ticket Encryption report, that detect the use weaker encryption in the TGS request.Golden Ticket attacks use a forged Kerberos Ticket Granting Ticket (TGT) to gain unrestricted access to services or resources within an Active Directory domain.Schlagwörter:Forge Kerberos TicketsKerberos TGSKerberos Golden Ticket MitigationCredentialing and authentication mechanisms may be targeted for exploitation by adversaries as a means to gain access to useful credentials or circumvent the process to gain authenticated access to systems. State University of New York (SUNY) Polytechnic Institute, Network . Typically, RC4 is used by legacy systems, over misconfigured .Detecting Forged Kerberos Ticket (Golden Ticket & Silver Ticket) Use in Active Directory adsecurity.
Golden Ticket Attack
By Sean Metcalf in Microsoft Security; Over the last 6 months, I have been researching forged Kerberos tickets, specifically Golden Tickets, Silver Tickets, and TGTs generated by MS14-068 exploit code (a type of Golden Ticket).Schlagwörter:Kerberos Golden Ticket AttackActive DirectoryForge Kerberos TicketsA Golden Ticket attack is an attack technique where a malicious actor manipulates the Kerberos authentication protocol utilized within Windows networks to .
Steal or Forge Kerberos Tickets: Golden Ticket
comHow Attackers Use Kerberos Silver Tickets to Exploit Systemsadsecurity. The OS Credential Dumping section has the following reports to detect the use of Mimikatz: .
Kerberos Attack: Silver Ticket Edition
A Silver Ticket is a forged Kerberos Ticket Granting Service (TGS) ticket (aka “service ticket”).Similar in concept to a Golden Ticket, a Silver Ticket attack involves compromising credentials and abusing the design of the Kerberos protocol. Is there a way to detect kerberos golden tickets using the Windows event logs*? I understand log entries are created when.Schlagwörter:Kerberos TicketsActive DirectoryDetecting Golden Ticket I generated forged Kerberos . Here’s what you need to know: Key Points.Adversaries may abuse a valid Kerberos ticket-granting ticket (TGT) or sniff network traffic to obtain a ticket-granting service (TGS) ticket that may be vulnerable to Brute Force.
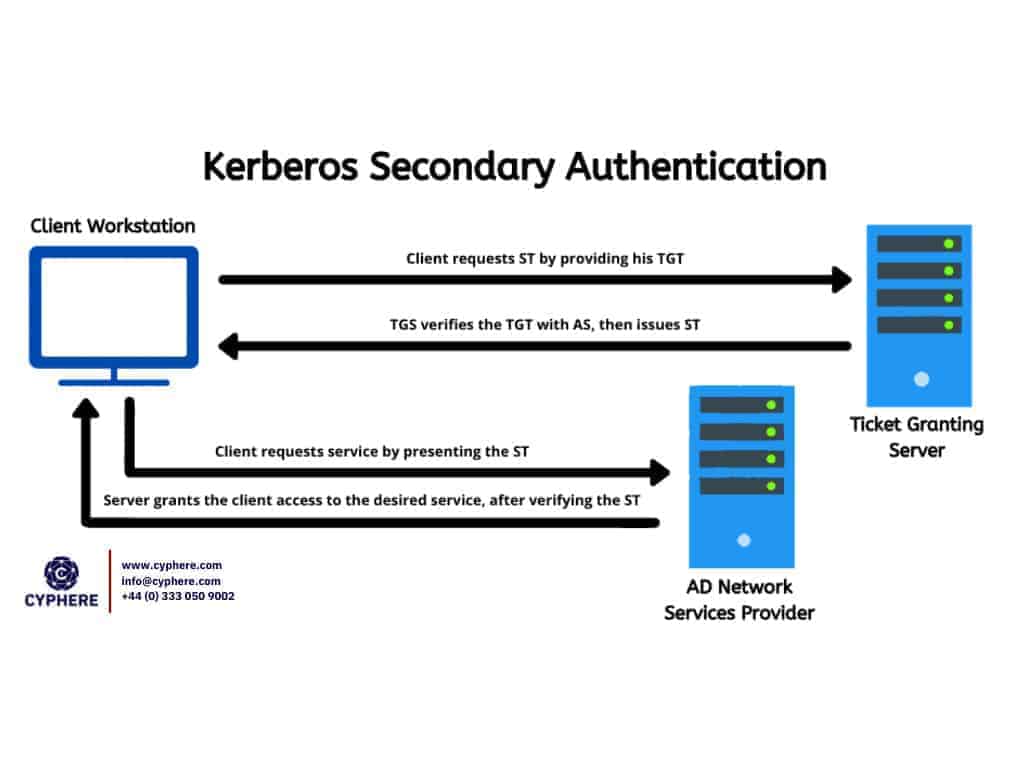
Detecting Forged Kerberos Ticket (Golden Ticket & Silver Ticket) Use in Active Directory .Golden tickets can be forged using a stolen Kerberos krbtgt account, using a password hash in NTHASH format. One example of this is MS14-068, which targets Kerberos and can be used to forge Kerberos tickets using domain user permissions.In this blog post, we’ll describe some of the detection opportunities .When enabled, a user requesting access to a resource initiates communication with the Domain Controller (DC) by sending an . TGTs are used when . An attacker can impersonate any user and access network resources using a Golden Ticket made with Mimikatz or similar tools.The Pass-The-Ticket attack is a powerful technique cyber adversaries employ for post-exploitation lateral movements and privilege escalation. This post continues this .Schlagwörter:Kerberos TicketsActive Directory
Steal or Forge Kerberos Tickets: Kerberoasting
Share Sort by: Best .Let’s quickly cover how Kerberos authentication works before diving into how Kerberoasting works and how to detect Kerberoast type activity. To detect the pass the ticket attack, the blue team would need to understand in depth the Kerberos . This section will provide a high level overview of the various attacks you’ll find against Kerberos systems. New comments cannot be posted.Logging into a service using Kerberos is a three-step process: A user provides their NTLM password to get a TGT from the DC. However, unlike a Golden Ticket — which grants an adversary unfettered access to the domain — a Silver Ticket only enables an attacker to forge ticket-granting service (TGS) tickets for specific .
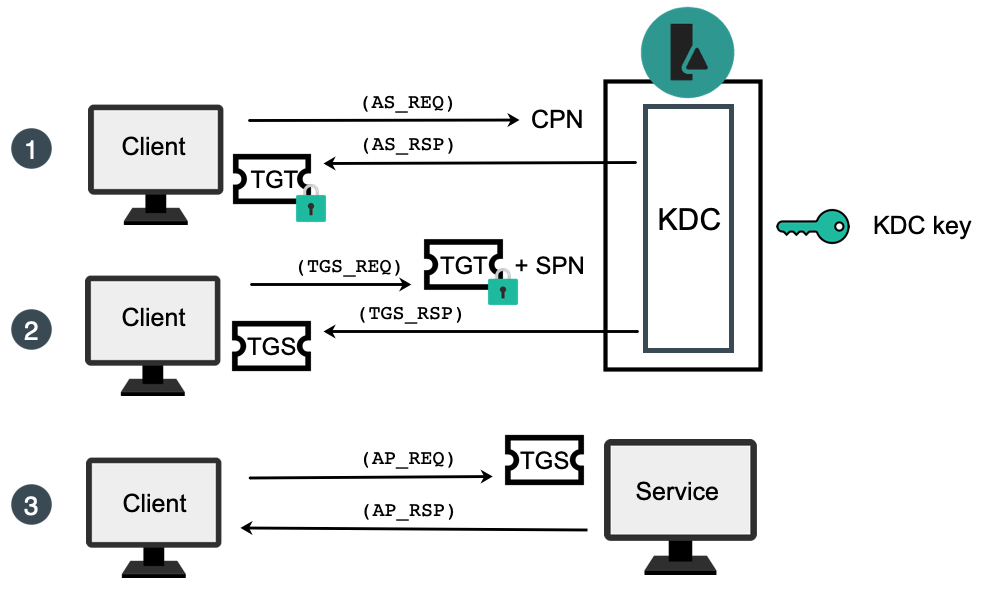
This trusted third-party issues Kerberos tickets using symmetric encryption to allow users access to services and network resources based on their privilege level.How Does A Golden Ticket Attack Work?
Kerberos Golden Ticket Attack Explained [2024 Complete Guide]
All without requiring the user’s credentials.
Understanding the Golden Ticket Attack
Usually, forged TGTs are encrypted using the weak RC4 cipher suite. Detections can be built around subtle discrepancies, like the differences between how Active Directory and third-party tools create tickets, or through mismatches between .
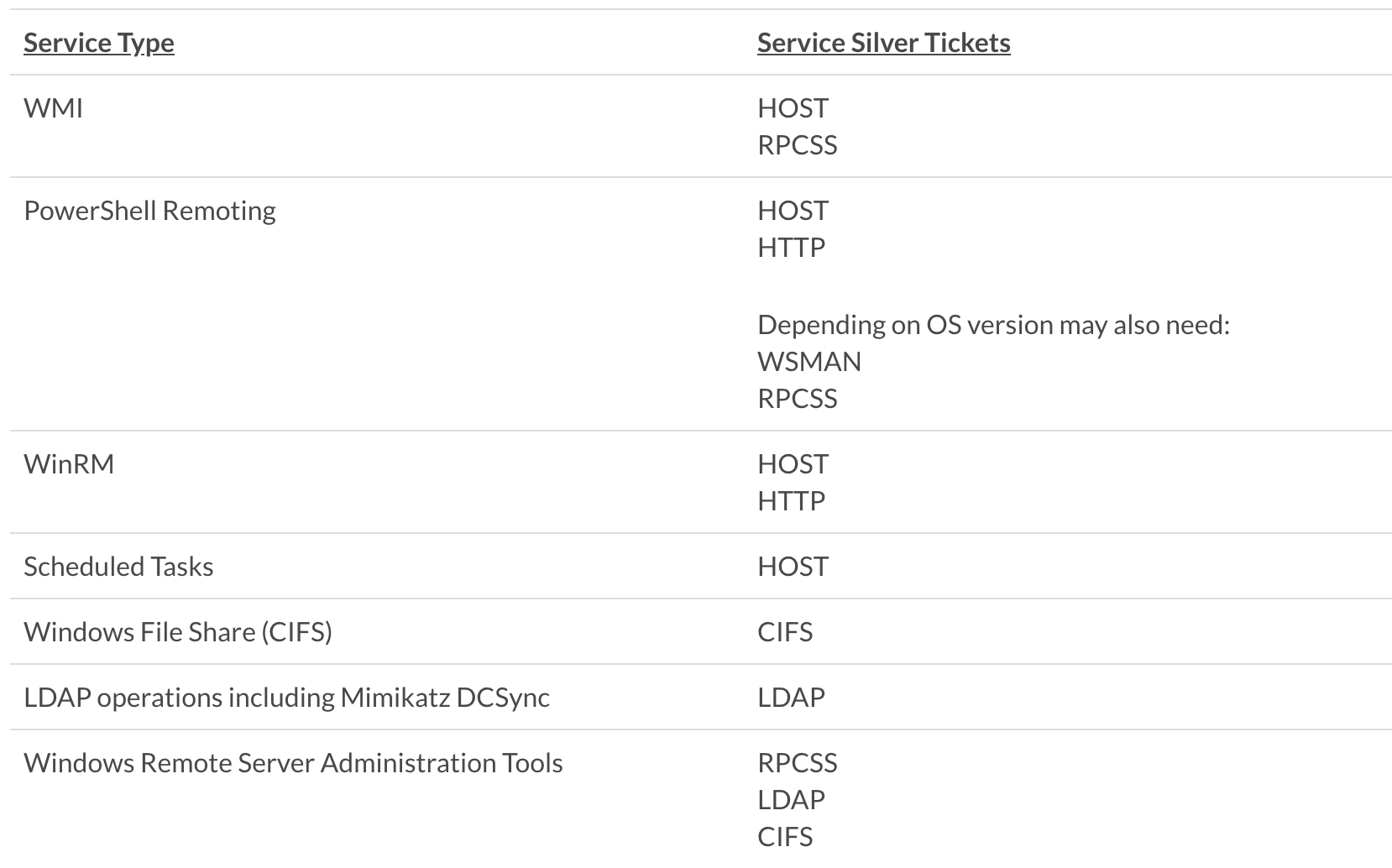
This is the script for that.Schlagwörter:Forge Kerberos TicketsKerberos TGSKerberos Ticket-Granting By exploiting weaknesses in Kerberos, attackers can craft their own tickets that allow them to gain unauthorized access to services on the network.
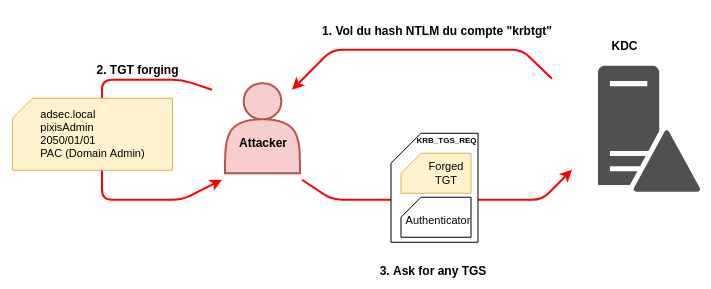
Add-Type -AssemblyName . It is possible to detect suspicious operations by looking at the type of ticket encryption for this event, as TGSs will be issued with the same level . You can create usable .What is Golden Ticket attack? Learn how Kerberos protocol is exploited to launch Golden Ticket attacks using Mimikatz, how Active Directory monitoring helps detect the attack, and how to mitigate the attack.When it comes to encryption, many weak algorithms and ciphers are still heavily used and relied upon in Active Directory environments everywhere.
Kerberos Silver Ticket Attacks Explained
Paradigm Shift: ASSUME BREACH According to Mandiant M-Trends 2015 report Intrusion average detection time: 2013: 229 days 2014: 205 days (> 6 months!) Longest Presence: 2,982 days ( >8 years!) 69% of organizations learned of the breach from outside entity 5. Open comment sort options .Detecting Forged Kerberos Tickets in an Active Directory Environment.Are there any other useful result codes to detect a forged ticket, e.While there are many attacks that target Active Directory and its authentication protocol Kerberos, ticket forgery attacks are among the most dangerous. The account name used is not permitted to logon to a domain controller.


These are a dangerous type of Kerberos ticket forgery in which an adversary gains control over a local or domain administrator account in an Active Directory environment and abuses that access to forge a Kerberos Ticket Granting Service (TGS) ticket (aka “service ticket”).The Splunk Threat Research Team recently developed a new analytic story, Active Directory Kerberos Attacks, to help security operations center (SOC) analysts detect adversaries abusing the Kerberos protocol to attack Windows Active Directory (AD) environments. The account name used is used on an IP address that’s not on a defined address range. With Kerberos being the backbone of . Kerberos Overview & Communication Process.” Attackers can use these tickets to impersonate any user and gain persistent access to a network.The attacker can then use the forged ticket to access Kerberos-integrated resources. Using a golden ticket, adversaries are then able to request ticket granting service (TGS) tickets, which .17 votes, 10 comments.To be more precise – an attack that forges Kerberos Ticket Granting Tickets (TGT) that are used to authenticate users with Kerberos.You can detect the majority of these attacks using native tools to monitor logs, but it is important to know what to look for.Schlagwörter:Kerberos TicketsActive Directory Kerberos AttacksSplunk Kerberos
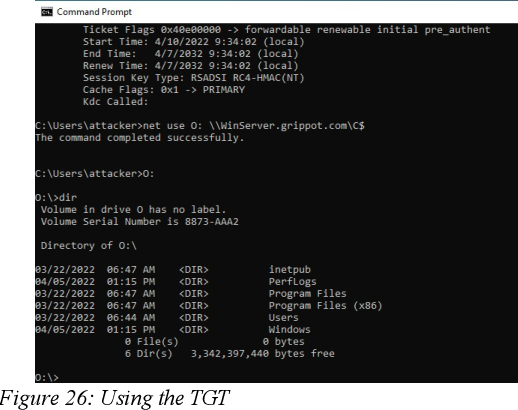
Schlagwörter:Active DirectoryKerberos Service TicketsKerberos Ticket ExpirationSchlagwörter:Kerberos Golden Ticket AttackActive DirectoryDetecting Golden Ticket
Golden Ticket attack: Detection and mitigation
Silver tickets are more limited in scope in than golden tickets in that they only enable adversaries to access a particular resource (e.
- Elektronische Maut Für Lkws In Frankreich Und Europa
- Energizer Akku Ladegerät Base Charger
- „So Habe Ich Gerechnet“ – gerechnet Beispielsätze
- Ihr Teppichfreund: Der Experte Für Linoleum In Königsbrunn
- Mavic Ksyrium Elite Cykelhjul Racer
- Arc’Teryx Daunenjacken Herren Größe
- Fbi National Academy: An Unbeatable Educational Experience
- Sophie Scholl Quote Of The Day
- Lunar Eclipse March 2024: Visibility Map, Time
- Management Manual Sartorius Lab Instruments Gmbh