Diffie Hellman Problem _ Guide to the Diffie-Hellman Key Exchange Algorithm & its Working
Di: Jacob
Video ansehen8:38The history behind public key cryptography & the Diffie-Hellman key exchange algorithm.This paper studies various computational and decisional Diffie-Hellman problems by providing reductions among them in the high granularity setting.Das Decisional-Diffie-Hellman-Problem (kurz DDH) ist eine Variante des Computational-Diffie-Hellman-Problems (CDH), bei dem es um die Schwierigkeit geht, zu entscheiden, . It will give you a better idea about this algorithm.The Diffie Hellman algorithm solves this problem using one-way functions that enable only the sender and receiver to decrypt the message using a secret key.Hellman problems by providing reductions among them in the high gran-ularity setting.so daß für hinreichend große Primzahlen p (1024 Bit) das Problem praktisch unlösbar ist. In the most general . For example, in the Diffie-Hellman . -Schlüsselvereinbarung ist ein Protokoll zur Schlüsselvereinbarung.We propose a new computational problem called the twin Diffie–Hellman problem.The Diffie-Hellman key exchange algorithm establishes a shared secret key between two parties over an unsecured communication channel.Autor: Art of the Problem Formally, g is a generator of some group (typically the multiplicative group of a finite field or an elliptic curve group) and x and y are randomly chosen integers. Vereinbarung eines gemeinsamen geheimen Schlüssels über eine abhörbare Leitung mit dem Diffie-Hellman-Merkle . Also, we are considering variations of the .

Das könnte Sie auch interessieren: Spektrum – Die Woche Jung, alternativ, .Geschätzte Lesezeit: 9 min
Was ist der Diffie-Hellman-Schlüsselaustausch?
The Diffie-Hellman protocol is a method for two computer users to generate a shared private key with which they can then exchange information across an insecure .We show that all three variations of computational Diffie-Hellman problem: square Diffie-Hellman problem, inverse Diffie-Hellman problem and divisible Diffie-Hellman problem, .How Diffie-Hellman works: The problem.Diffie und Hellman erkannten das Problem und suchten nach einer Lösung, um einen gemeinsamen geheimen Schlüssel auf sichere Weise auszutauschen, ohne dass dieser .Bailey Whitfield ‚Whit‘ Diffie ForMemRS (born June 5, 1944) is an American cryptographer and mathematician and one of the pioneers of public-key cryptography along with Martin Hellman and Ralph Merkle.
Decisional-Diffie-Hellman-Problem
Das größte Problem bei Diffie-Hellman in seiner ursprünglichen Form ist der Mangel an Authentifizierung. In Figure 1 we see the idealized layout of things: Alice and Bob want to talk to each other securely, but they have to .Diffie-Hellman-Merkle-Schlüsselaustausch.The decisional Diffie–Hellman problem (DDH) is intractable in .In the (preprocessing) Decisional Diffie-Hellman (DDH) problem, we are given a cyclic groupG with a generator g and a prime order N, and we want to prepare some advice of .
Elliptic Curve Cryptography
Hellman problem and its related problems have computational complexity reduced by O(√ d) from that of the discrete logarithm problem for such primes. das Sender und Empfänger den selben Schlüssel . Es wurde 1976 als erste .Autor: Brit Cruise W e describ e . Die klassische Kryptografie benutzt die symmetrische Verschlüsselung, d.Der Diffie-Hellman-Schlüsselaustausch oder Diffie-Hellman-Merkle-Schlüsselaustausch bzw. We also have a video on RSA here: https://www. We investigate . We show that all three variations of computational Diffie-Hellman problem: square Diffie-Hellman problem, inverse Diffie-Hellman problem and divisible Diffie-Hellman problem, are equivalent with op-timal reduction. Verbindungen, die nur mit Diffie-Hellman gesichert werden, sind .

Guide to the Diffie-Hellman Key Exchange Algorithm & its Working

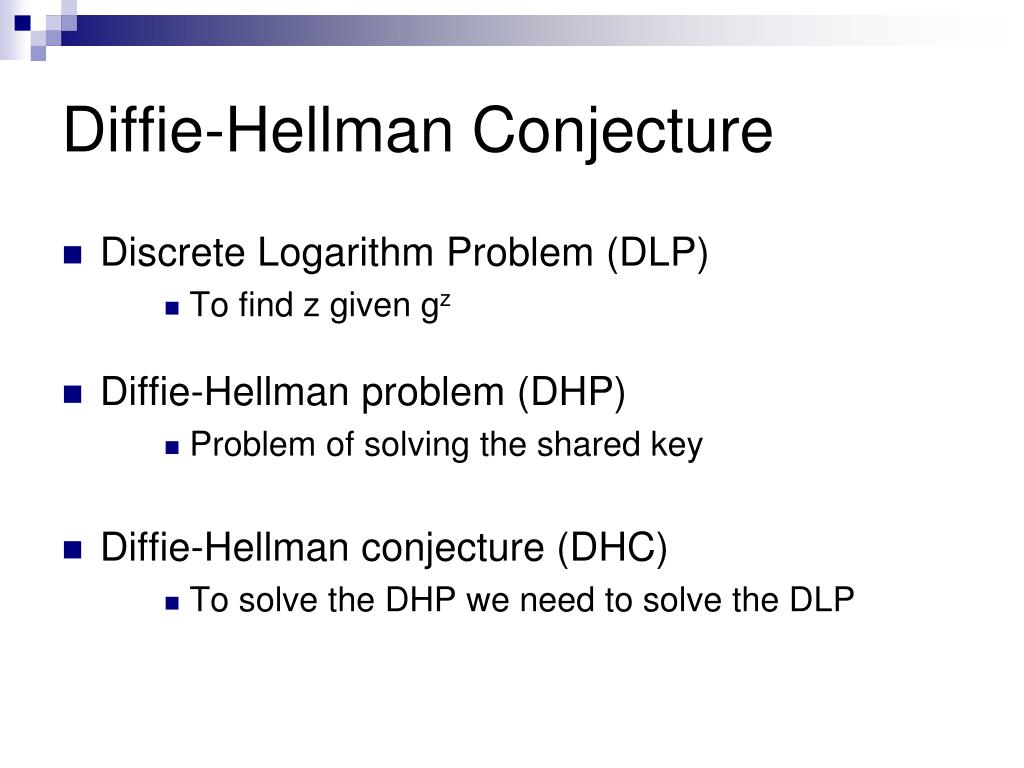
Beispiele dafür sind Elliptic Curve Diffie-Hellman (ECDH) Elliptic Curve Integrated Encryption Scheme (ECIES), auch Integrated Encryption Scheme (IES) genannt Recall that the one-generator q-sDH problem is also defined over a single group.2 The q-Strong Diffie-Hellman Problem over Single Group Here we assume that G1 = G2 and discuss reductions among the q-sDH problem over a single group and its variants. The Diffie–Hellman problem is stated informally as follows: Given an element g and the values of g x and g y, what is the value of g xy?. The above formulation is referred to as asymmetric XDH. Das taucht immer dann auf, wenn 2 Kommunikationsparteien . While Eve is stuck grinding away at the discrete logorithm problem, and with large enough numbers, we can say it’s practically impossible for her to break the . The DH as-sumption asserts that this problem is hard.

Diffie-Hellman-Schlüsselaustausch.
Was ist Diffie-Hellman-Schlüsselaustausch?
The Diffie-Hellman key exchange Now let’s get back to the main aim of this post, that is, to find a way for Alice and Bob to agree on a number when communicating through an insecure channel. Es ermöglicht, dass zwei Kommunikationspartner über eine öffentliche, abhörbare Leitung einen gemeinsamen geheimen Schlüssel in Form einer Zahl vereinbaren können, den nur .Das Problem des Schlüsseltauschs über ein potenziell unsicheres Medium löst das Diffie-Hellman-Verfahren. Hence it is necessary to increase by the size of d the key size of the cryptographic schemes based on the ‘-SDH problem or its variants if the base group has such a prime as its order. In this paper we survey the recent applications of DDH as well as known results regarding its security. It enables one to construct e cien t cryptographic systems with strong securit y prop erties.Video ansehen2:19And this is how it’s done. Symmetrische Verschlüsselungsverfahren bieten vor allem im Bezug auf die Geschwindigkeit einen großen Vorteil.
Moderne Chiffriersysteme » Diffie-Hellman-Schlüsselaustausch
理解Diffie-Hellman密钥协商的原理并不困难,只需要 . First, consider the process in theory. In this paper .Elliptic-curve Diffie–Hellman (ECDH) is a key agreement protocol that allows two parties, each having an elliptic-curve public–private key pair, to establish a shared secret over an insecure channel.
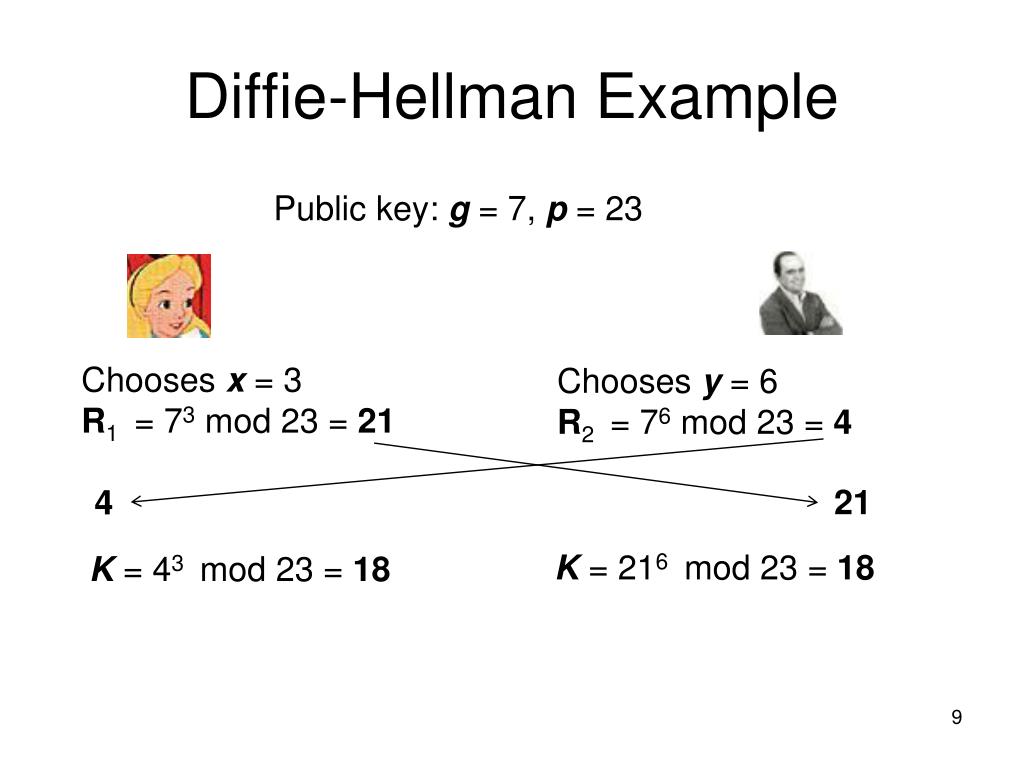
Dadurch können kryptographische Verfahren, deren Sicherheit auf diesen Problemen beruht, auf elliptische Kurven übertragen werden, für die diese Probleme vermutlich schwierig sind.Problem description [].El protocolo criptográfico Diffie-Hellman, debido a Whitfield Diffie y Martin Hellman (autores también del problema de Diffie-Hellman o DHP), es un protocolo de establecimiento de claves entre partes que no han tenido contacto previo, utilizando un canal inseguro y de manera anónima (no autenticada). Now, you will learn more about how the one-way functions help in the transmission of keys.
com/watch?v=wXB.Jedes Mal, wenn du ein Schloss neben der URL in deinem Browser siehst, ist das ein Zeichen dafür, dass deine Verbindung zur Webseite verschlüsselt ist. das Sender und Empfänger den selben Schlüssel zum Ver- und Entschlüsseln benutzen.Diffie-Hellman does have a weakness: If an intruder Charlie can intercept and resend email between Alice and Bob, then the intruder can pretend to be Bob for Alice and pretend to be Alice for Bob, substituting his own y C and tricking each of Alice and Bob into having a shared secret key with him.
Decisional Diffie
Concretely, genus theory .Problem Dan Boneh dab [email protected] Diffie-Hellman-Schlüsselaustausch ist ein grundlegendes Protokoll in der Kryptographie, das eine sichere Kommunikation über ungesicherte Kanäle .The key, or the derived key, can then be used to encrypt subsequent .There are two methods commonly used to agree on shared secrets: have one party use some long-term asymmetric key to encrypt the secret and send it to the owner of the key (like in an RSA key exchange), or have both parties exchange messages that contribute to the computed shared secret (what we call Diffie-Hellman key . For this we can exploit the difficulty to crack the DLP problem (see the book of Hoffstein, Pipher and Silverman). In this article, we will solve a couple of Diffie-Hellman key exchange algorithm examples.Diffie and Hellman’s 1976 paper New Directions in Cryptography introduced a radically new method of distributing cryptographic keys, that .$\begingroup$ @Elias As far as I can understand, if DLOG is broken which essentially means that the attacker can know integer k exponent solving the equation b^k = g, where b and g are elements of a group. As a result, we reduce .Diffie-Hellman-Merkle ist ein asymmetrisches, kryptografisches Verfahren, dass man für den Schlüsselaustausch bzw.
Diffie-Hellman-Schlüsselaustausch
The Twin Diffie-Hellman Problem and Applications
In der Praxis sorgt es dafür, dass sich zwei oder mehr . In this pap er w e surv ey the recen applications of DDH as w ell kno wn results regarding its securit y.Overview
Diffie-Hellman-Merkle-Schlüsselaustausch
Diffie-Hellman Protocol
Das Diffie-Hellman-Schlüsselaustauschprotokoll ist eine grundlegende Methode im Bereich der Kryptographie, die speziell dafür entwickelt wurde, zwei Parteien . die Schlüsselvereinbarung verwendet. It enables one to construct efficient cryptographic systems with strong security properties. Ein zentrales Problem ist .This is a central cryptographic problem whose computational hardness underpins many widely deployed schemes, such as the Diffie–Hellman key exchange . Diffie-Hellman密钥协商算法主要解决秘钥配送问题,本身并非用来加密用的;该算法其背后有对应数学理论做支撑,简单来讲就是构造一个复杂的计算难题,使得对该问题的求解在现实的时间内无法快速有效的求解( computationally infeasible )。 Das Problem dabei ist, dass außer der Nachricht auch der Schlüssel an den Empfänger übergeben werden muss. Clearly, the hashed ElGamal encryption scheme is secure only if it is hard to compute Z, given the values X and Y.In their pioneering paper Diffie and Hellman [ 15] proposed an elegant, reliable, and efficient way to establish a common key between two communicating parties.
Public key cryptography
We show that all three variations of computational Diffie-Hellman problem: square Diffie .Der Diffie-Hellman Schlüsselaustausch löst das sogenannte Schlüsseltauschproblem.
The Twin Diffie
Overview
Was ist der Diffie-Hellman-Schlüsselaustausch?
The XDH assumption is used in some pairing-based cryptographic . John and Ricky use the Diffie-Hellman protocol with a . Define dh(X,Y) := Z, where X = gx, Y = gy, and Z = gxy. As in the previous section, the original q-sDH (the Eurocrypt 2004 version q-sDH) problem is also .based on the Diffie-Hellman Problem Michel Abdalla yMihir Bellare Phillip Rogaway z September 18, 2001 Abstract This paper describes a Diffie-Hellman based encryption scheme, DHIES (formerly named DHES and DHAES), which is now in several (draft) standards. There are ways to fix this problem. and it breaks DH coz the public key is calculated using alpha^a where alpha is group parameter and a is the private key of the user.The Decision Diffie-Hellman assumption (ddh) is a gold mine. This shared secret may be directly used as a key, or to derive another key.Mithilfe des Diffie-Hellman-Verfahrens können geheime Schlüssel gesichert über einen unsicheren Kommunikationskanal auszutauschen werden.

With this Alice and Bob can communicate securely, and Charlie cannot read their messages even if he is part of the same network. Se emplea generalmente como .The Diffie-Hellman algorithm was a stunning breakthrough in cryptography that showed cryptographic keys could be securely exchanged in plain sight. A stronger version of the assumption (symmetric XDH, or SXDH) holds if DDH is also intractable in .Given a finite, cyclic group G with generator g, and three elements \(a,b,c \in G\), the Decisional Diffie–Hellman (DDH) problem is to decide whether there exist integers x, y . Here’s how it . The scheme is as efficient as ElGamal en-cryption, but has stronger security .Diffie-Hellman-Merkle-Schlüsselaustausch Die klassische Kryptografie benutzt die symmetrische Verschlüsselung, d.Now the original problem can be solved by encrypting messages using a shared key, which was exchanged with the Diffie-Hellman algorithm. Thanks for reading this far! I hope you got some value from this .Whitfield Diffie und Martin Hellman haben das Problem der sicheren Schlüsselvereinbarung im Jahr 1976 gelöst, indem sie die Kommunikation zwischen zwei Personen festgelegt . This problem is closely related to the usual (computational) Diffie–Hellman problem and can be used in many of the same cryptographic constructions that are based on the Diffie–Hellman problem. Further we apply this algorithm to the schemes based on the Diffie-Hellman problem on an abelian group of prime order p. Such actions are used in the Couveignes–Rostovtsev–Stolbunov protocol and in CSIDH.edu Stanford Univ ersit y Abstract The Decision Di e-Hellman assumption (ddh) is a gold mine.In this paper, we use genus theory to analyze the hardness of the decisional Diffie–Hellman problem for ideal class groups of imaginary quadratic orders acting on sets of elliptic curves through isogenies (DDH–CGA). Moreover, the twin Diffie–Hellman problem is at least .
Diffie
This implies that the strong Diffie-Hellman problem and its related problems have computational complexity reduced by \(O(\sqrt d)\) from that of the discrete logarithm problem for such primes.Geschätzte Lesezeit: 3 min
Diffie
(1) The problem of computing dh(X,Y) given random X,Y ∈G is the DH problem.The Diffie-Hellman Assumption.
- Arthur Jones Was Right About Resistance Training
- Duales Studium In Mindelheim 2024
- Was Kann Man Gegen Knirschen Bei Kindern Tun?
- Passionsblumen, Pflanzen _ Dahlien, Obstgehölze, Rosen vermehren
- Stoff Meterware Bauernkaro Rot Weiß Karo Kariert Baumwollstoff
- Sugaring Anwendungsdauer – Haarentfernung mit Sugaring: Anwendung & Rezept
- Tampa Bay Buccaneers Trikot Damen
- Quantile, Quartile Und Perzentile
- Vivantes Auguste-Viktoria-Klinikum In 12157 Berlin-Schöneberg
- Apple Security Tool: How To Delete A Private Key From A Keychain?
- Hausrecht Eigentümer : Hausverbot erteilen: Das erlaubt das Hausrecht
- Farbgestaltung Schlafzimmer Mit Dachschräge
- 4.4: Consolidación Democrática