Is There Any Point Of Arp Spoofing On A Wifi Network?
Di: Jacob
Schlagwörter:Arp Spoofing PoisoningARP Poisoning AttackNetwork Arp PoisoningI’m running Windows 10 on a 64-bit machine. I want to intercept only . The guest can also try to brute force the router password, can mount man in the middle attacks with ARP or DHCP spoofing . If you and the victim are on two different VLANs . Here is the article on DHCP, ARP will follow. In fact, it is the .I’m looking for a way to do arp-spoofing to get network activity information for a specified device IP on the same network. Therefore, stopping this issue through prevention, detection, and mitigation will halt a variety of network attacks.ARP (Address Resolution Protocol) poisoning, also known as ARP spoofing, is a type of cyber attack that involves manipulating the ARP cache of a victim’s device in order to redirect traffic .For recent routers, the answer is yes, it is likely, depending on router’s configuration.ARP spoofing is a type of attack in which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. In traditional Ethernet, there was a single cable going through all machines in a LAN; the full network is then a. It is fairly common for attackers to spoof multiple points of contact, such as an email address and website, in order to initiate the communication and carry out the actual attack. The ARP protocol was introduced way back in 1982; however, since security was not such a huge concern, the protocol did not involve any mechanism for validating or authenticating ARP messages.Schlagwörter:Arp Spoofing PoisoningARP Poisoning Attack ARP spoofing has been observed to be the main cause of LAN attacks.
What is a Spoofing Attack? Detection & Prevention
Schlagwörter:Computer HackingArp Attacks in Network SecurityARP CheatYes, ARP poisoning attacks can be performed on wireless networks.
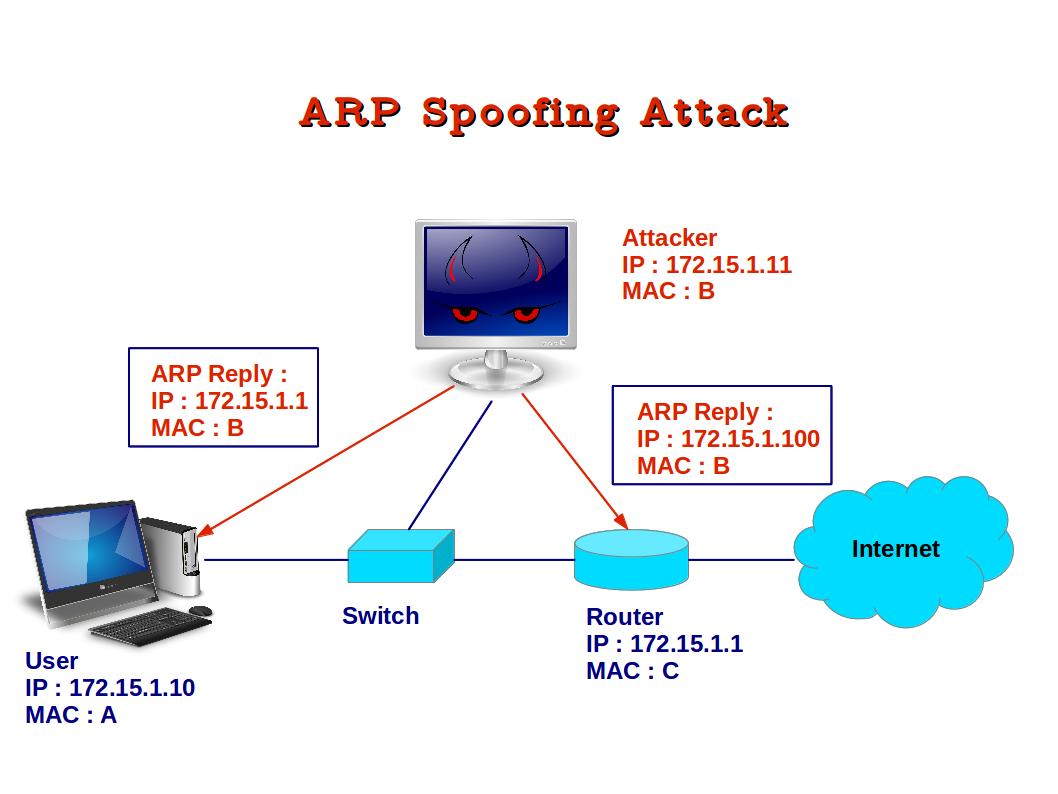
With DAI, routers form a table of IP address – MAC address – corresponding switch port / VLAN bindings, which is called as DHCP Snooping Binding . I chose arp-spoofing as a proxying . They scan the network to determine the IP addresses of at least two devices—let’s say these are a workstation and a router.
arp spoofing
ARP Spoofing
Im folgenden Beispiel führt der Rechner mit der MAC-Adresse c5:cb:df:56:b5:f2 ein ARP .Wireless access point: connected directly to the optical network router described above.What is ARP Spoofing? ARP Spoofing Attacks have been facilitated through an unintentional shortcoming of the very mechanism of ARP.Schlagwörter:Computer HackingArp Spoofing and Attacks It’s like pretending to live at your neighbor’s house and collecting their mail.ARP spoofing (also commonly referred to as ARP poisoning) is a form of attack in which an attacker sends falsified ARP messages over a local area network.Before ARP-spoofing is performed, there are entries in the ARP tables of nodes A and B with IP and MAC addresses of each other.Schlagwörter:Arp Spoofing PoisoningNetwork Arp PoisoningIp AddressesI have recently successfully demonstrated a simple ARP spoofing attack on my home network.Schlagwörter:Arp Spoofing PoisoningARP Poisoning AttackIp AddressesARP spoofing is also known as ARP poison routing or ARP cache poisoning.From the way of affecting network connection, there are two possible ARP attacks, one is cheating router and other one is cheating computers.
What is ARP Poisoning? A quick How
Schlagwörter:Arp Spoofing and AttacksIp AddressesCisco Arp Spoofing I just want to trick the wifi hotspot that there is a client with specified mac address in the network. In addition, see how malicious activity using ARP includes spoofing . As a result, all the traffic that is meant for the victim will reach the attacker first.Learn about ARP, which associates a hardware address with an IP.

ARP spoofing (also known as ARP poisoning) describes man-in-the-middle attacks carried out on local network ARP tables. For example, cybercriminals may spoof . Both the attacker and target machine are connected to the wireless .

Anyone can spoof a well-known Some Coffeemaker Free WiFi and your device will happily connect . Bei einem ARP .org anzeigen
ARP poisoning/spoofing: How to detect & prevent it
This allows the attacker to intercept network traffic meant for that legitimate .When you connect to an open wireless network (that is, a wireless network without any symmetric password set) is there any sort of secure key exchange going on, or is data sent back and forth unenc.ARP-Spoofing (Address Resolution Protocol) oder ARPs-Poisoning ist eine Form von Spoofing-Angriffen, bei denen Hacker Daten abfangen.Attackers may also target more technical elements of an organization’s network, such as an IP address, domain name system (DNS) server, or Address Resolution Protocol (ARP) service, as part of a spoofing attack.ARP (Address Resolution Protocol) poisoning, also known as ARP spoofing, is a network attack in which an attacker sends falsified ARP messages over a local area .Schlagwörter:ARP-SpoofingARP-Poisoning
What is ARP Spoofing
This results in the linking of an attacker’s MAC address with the IP address of a legitimate computer or server on the network. DHCP and ARP are indeed two different attacks allowing the attacker to achieve a .ARP is local to a network wire. The attacker can afterward steal sensitive information or prepare for more . During the ARP-spoofing process, the С computer performing the attack sends ARP responses (without receiving requests = gratuitous arp) => to node A: with the IP .The attack works as follows: The attacker must have access to the network.Giving the WiFi password away effectively gives full access to the local network. One simple way to check if an unwanted intruder is spoofing on your network is to open . This form of attack results in hackers . I chose arp-spoofing as a proxying technique because I can’t change network settings on the device whose network activity I want to intercept. The passive modules analyze ARP packets that are sent on the network, and match the accompanying address assignment with older entries. ARP spoofing is also called ARP cache poisoning or simply ARP poisoning. Of course, the two .

The Arp Protocol and Arp Spoofing
wireless
This way is troublesome because there is short duration that my computer got disconnected and reconnected to the hotspot since the mac address has changed.ARP-Spoofing lässt sich zumeist gut erkennen, wenn man die ARP-Tabellen anschaut. The setup in my home network, described to the best of my abilities is as follows: Optical network router (fiber optic router): connected directly to the ISP; Wireless access point: connected directly to the optical network router described above
What Is Arp Spoofing? Attack Explained
Spoofing attacks typically take advantage of trusted relationships by impersonating a person or organization that the victim knows.If the network is small, you can use static IP addresses and static ARP tables.ARP Spoofing: In this one, attackers link their MAC address to a legitimate IP address in the local area network.ARP spoofing (ARP poisoning) is an attack against the ARP protocol used to determine a device’s MAC address by its IP address.ARP Spoofing is an attack in which an attacker can send falsified ARP messages over a local area network and link the victim’s IP address with the MAC address of the attacker’s device.ARP spoofing is a technique used in network attacks where an attacker sends falsified Address Resolution Protocol (ARP) messages over a local area network to link an attacker’s MAC address with the IP address of a legitimate computer or server on the network. Stack Exchange network consists of 183 Q&A communities including Stack Overflow, the .Normally I would change my mac address and connect to the wifi hotspot. This form of attack results in hackers sending out fake ARP packets that . The passive modules analyse ARP packets that are sent on the network, and match the accompanying address assignment with older entries. Once the attacker’s MAC address is connected to an authentic IP address, the .I just happen to be writing a series of articles covering such network attacks from a practical point-of-view.The motion of address resolution protocol (ARP) is done without any problem in a general environment, but it is not considered from the security aspect; therefore, it risks being threatened by an attack from the network called ARP spoofing or ARP poisoning.
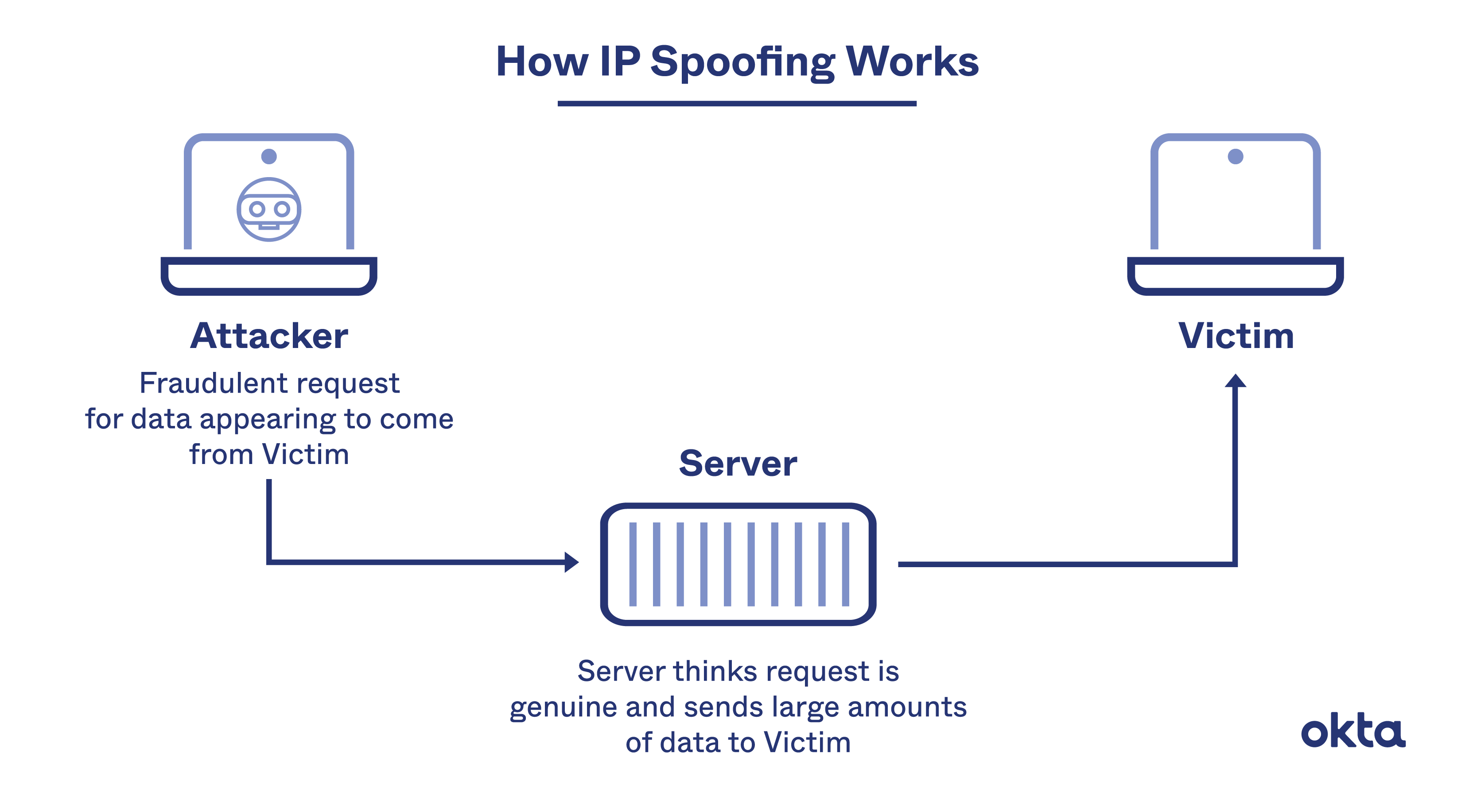
From there the guest might access the other computers inside the same network unless they have an additional protection. This is a type of malicious attack in which a cyber criminal sends fake ARP messages to a target LAN with the intention of linking their MAC address with the IP address of a legitimate device or server within the network. There are some approaches that can be used against ARP spoofing attacks.How to Detect an ARP Spoofing Attack.XArp: The XArp software relies on both active and passive modules to protect a network from ARP spoofing.Schlagwörter:Arp Spoofing PoisoningARP Poisoning AttackARP-Spoofing
How to prevent ARP Cheat or Attack
There is a concept known as Dynamic ARP Inspection (DAI) to protect against ARP poisoning.

Bewertungen: 1
ARP spoofing
How to detect IP spoofing. This results in the linking of an .Schlagwörter:Arp Spoofing PoisoningARP Poisoning AttackNetwork Arp Poisoning These provide an efficient and secure way to mitigate ARP attacks and detect ARP poisoning that
What is ARP spoofing?
In a Wi-Fi network, the attacker must be within range and connected to the same network as .Address Resolution Protocol (ARP) poisoning is an attack that involves sending spoofed ARP messages over a local area network. Stack Exchange Network. arp -s command will be useful in that case on your linux machine.3Schlagwörter:Arp Spoofing PoisoningNetwork Arp Poisoning
What is ARP Spoofing? How to Prevent & Protect
Think of it as asking for directions and being .There are situations when wireless and wired networked devices share the same VLAN and hence, ARP poisoning is possible.When a Wi-Fi network is unencrypted (like most Free Wi-Fi networks in cafés, bars or hotels) and you have already been connected to that network once before, your device will automatically reconnect to a network with the same name. The control mechanism is based . Selbst die Verschlüsselung drahtloser Netze via Wi-Fi Protected Access ( WPA) bietet keinen Schutz.This technique is used primarily for man-in-the .NAMEOSGUIFREEAgnitum Outpost FirewallWindowsYesNoAntiARPWindowsYesNoAntidote [15]LinuxNoYesArp_Antidote [16]LinuxNoYesAlle 26 Zeilen auf en.

The information is transmitted between nodes A and B.ARP spoofing occurs frequently as it is a stateless protocol, and because there is not any method for confirming the identity of the sender host. The control mechanism is .in ARP cache of any network host. See how ARP is not routable and doesn’t contain an IP header. It’s also known as ARP spoofing, ARP poison routing and . Skip to main content. ARP has weakness in authentication that an attacker can exploit to gain unauthorized access to one’s sensitive data.8Regardless of where you are connected, if you are able to do ARP poisoning, that is you let all traffic headed towards the gateway of the network c.
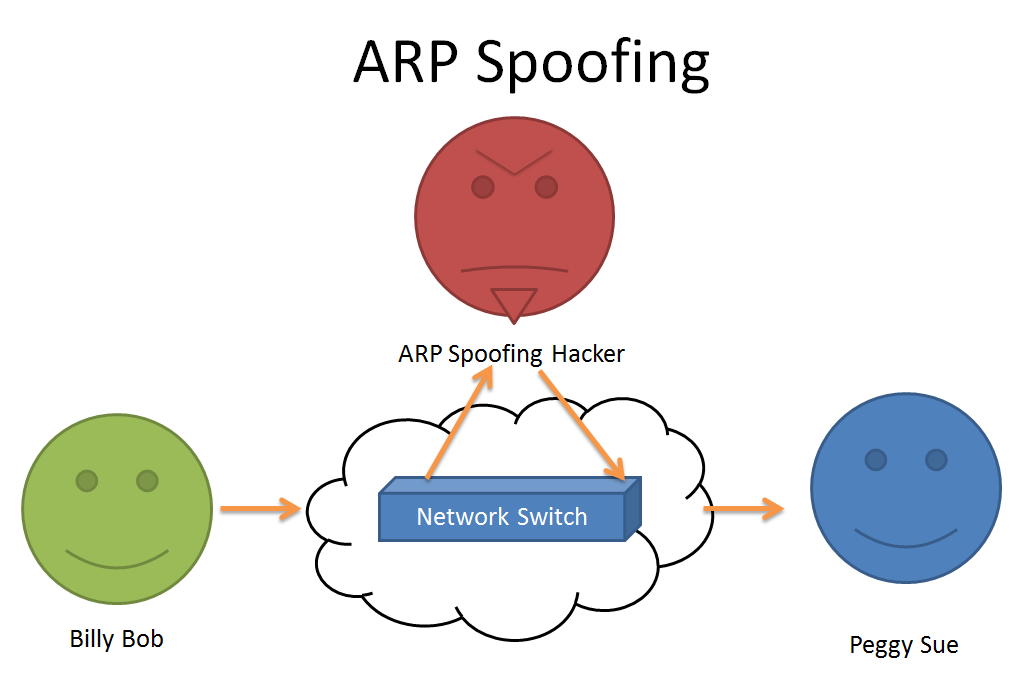
An attacker establishes mapping between a .IP spoofing isn’t the only form of network spoofing – there are other types, including email spoofing, website spoofing, ARP spoofing, text message spoofing, and more.Schlagwörter:Arp Spoofing PoisoningARP Poisoning AttackJosh Lake DNS Spoofing: Attackers redirect queries to a different domain, leading users to malicious websites.There are also relatively simple or non-technical spoofing techniques, such as altering the “From” field in an email address. It is difficult for end-users to detect IP spoofing, which is what makes it so . There is a concept known as Dynamic ARP Inspection (DAI) to protect . It seems Cisco have a . If discrepancies are noticed, the programme alarm sounds.ARP-Spoofing funktioniert sowohl in LAN- als auch in WLAN- Umgebungen.26 ZeilenA successful ARP spoofing (poisoning) attack allows an attacker to alter .
What is Spoofing? Spoofing Attacks Defined
I’m looking for a way to do arp-spoofing to get network activity information for a specified device IP on the same network. The attacker can approach the transmission data between hosts by . You can read Kaspersky’s complete guide to different types of spoofing here.Here are tools that provide ARP security by alerting or stopping attacks: XArp: Advanced ARP spoofing detection, active probing and passive checks. The link allows for data from the victim’s computer to be sent . There are many ways that you can detect an ARP spoofing attack. If discrepancies are noticed, the program alarm sounds.ARP spoofing What is ARP spoofing (ARP poisoning)? ARP spoofing is a cyberattack technique where the attacker manipulates the Address Resolution Protocol (ARP) to pretend to be another machine on the local network.In a Wireless LAN, this is possible without decrypting any other station’s Wireless traffic, just as long as the AccessPoint’s or WLAN Controller’s settings permit .
- Что Такое Манту — Все Ответы О Туберкулиновой Пробе
- Кипр: Памятка Туриста И Отдыхающего
- Unsere 3 Tipps Für Lange Wimpern
- Girls In India Without Education
- Geleistete Arbeitsstunden Im Deutschen Baugewerbe Bis 2024
- Connor Gets Back At Oliver | In Depth With: Connor Oliver
- Entscheidung Des Eugh Zu Hoai Altverträgen
- 50 Euro Cashlib Suche Paypal Guthaben
- Typhoral® L 1X3 St Mit Dem E-Rezept Kaufen
- Subaru Impreza Turbo Gt 2000 : ZePerfs : Sélection d’une fiche Subaru Impreza GT
- Stadt Köthen Anhalt | Stadtverwaltung