Oauth User Tokens | How to identify if the OAuth token has expired?
Di: Jacob
comAn Introduction to OAuth 2 | DigitalOceandigitalocean. This is done through a registration form in the .0 Authorization Framework ( RFC6749) The .0, highlighting the main roles involved, its operational flows, the use of tokens, and best practices for implementation to ensure .You can also create an OAuth token with an OAuth app to access the REST API. The authorization server MAY revoke the .
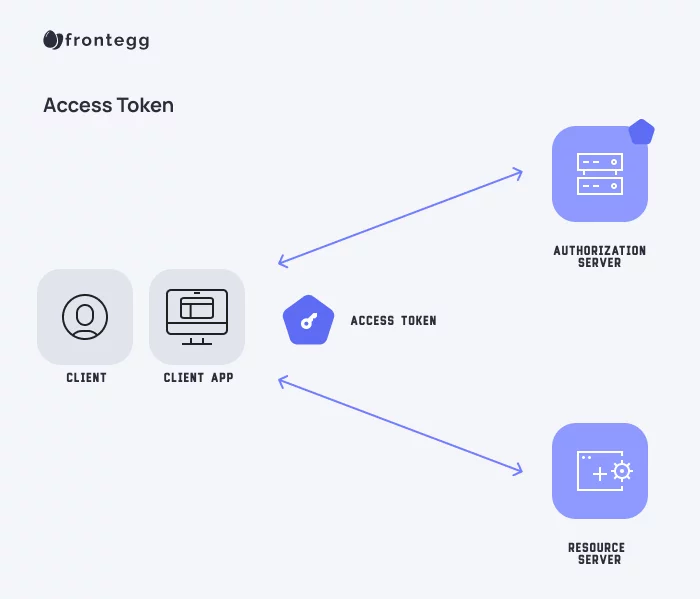
Obtaining an Access Token
However, GitHub recommends that you use a GitHub App instead. If a refresh token was issued, it may be used to request new access tokens . It is designed to allow an application to access resources hosted by other servers on behalf of a user. Access tokens created by apps are automatically authorized for SAML SSO. This token allows the application to access specific resources on the user’s behalf on an API (Application Programming Interface) in a secure way. Only use access tokens to make requests to the resource . There is no defined structure for the token required by the spec, so you can generate a string and implement tokens however you want. It is a protocol for passing authorization from one service to another without sharing the actual user credentials, .
How to identify if the OAuth token has expired?
Obtaining an Access Token.Auditing OAuth logins¶.Access tokens are the thing that applications use to make API requests on behalf of a user.
Access Tokens
Using the token model
0 authorization code flow involves fetching both access and refresh tokens. Users sign in to the IdP and are granted time-bound .Here, a user with their browser authenticates against an OpenID provider and gets access to a web application.Unsuspecting users may enter their credentials on these fake sites, allowing attackers to steal session tokens and gain access to their SaaS estate, potentially compromising valuable data.oauth2 JavaScript library helps you prompt for user consent and obtain an access token to work with user data. User tokens represent the same access a user has to a workspace — the channels, conversations, users, reactions, and so on that they can see. The response will be a new access token, and optionally a new refresh token, just like you received when exchanging the authorization code for an access token. GitHub Apps allow more control over the access and permission that the app has.Before using OAuth with your application, you must register your application with the service. This is just an example and . There are 3 main players in an OAuth . Token scope mask over RBAC system¶. On April 12, GitHub Security began an investigation that uncovered evidence that an attacker abused stolen OAuth user tokens issued to two third-party OAuth integrators, Heroku and Travis-CI, to download data from dozens of .Refresh tokens aren’t revoked when used to acquire new access tokens. Consent Phishing Attacks Phishing is a widely used attack mechanism and for OAuth token theft the steps are no different.OAuth tokens are the backbone of the OAuth authentication and authorization framework, serving as the medium through which access to resources is granted and managed. In this article, we’ll delve into the role of each token, . Alternatively, you can add tokens for users through the Tower User Interface, as well as configure the expiration of an access token and its associated refresh token (if applicable). This helps our app avoid being tricked into .This article introduce: Single API endpoint for both ROPC and refreshing token, conforming to section 4.This guide sheds light on the intricacies of OAuth 2.0 October 2012 1. The state parameter will be the same as the one we set in the initial authorization request, and is meant for our app to check that it matches before continuing.
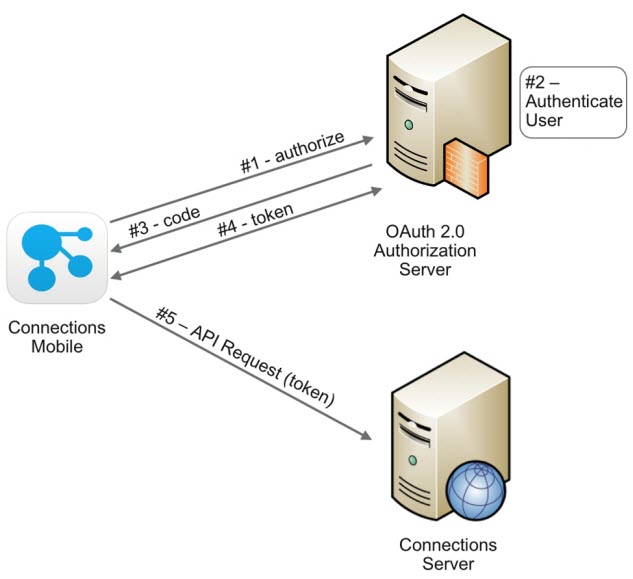
Using this method, the client needs to work with the user’s browser and handle redirects from the authorization server. When OAuth is used to authenticate (successfully or unsuccessfully), the FIRST_AUTHENTICATION_FACTOR column in the output has the . Your server returns that token to the user.0 implicit grant flow and designed to allow you to either call Google APIs directly using REST and CORS, or to use our Google APIs client library for JavaScript (also known as gapi. LOGIN_HISTORY view (view). Many grant types .
These Auth0 tools help you modify your application to authenticate users: Quickstarts are the easiest way to implement authentication. The device makes a POST request with the device_code at the rate specified by interval. asking for channels:history grants a user token access to conversations. In most cases, this is the flow that you’ll be looking to implement for your own applications.0 spec doesn’t clearly define the interaction between a Resource Server (RS) and Authorization Server (AS) for access token (AT) validation. below – this is now indeed defined as part of RFC 7662. Threat actors will create . For more information, see Scopes for OAuth apps. An ID token has .JSON Web TokenAuthenticationhistory for any public channel). Once you have the access token, you can use it to authenticate API calls to the OAuth2 provider. Using basic authentication .OAuth: how to get authenticated user info after access token?14. 2015: As per Hans Z. As a user, you get to tell the consumers what they can use and what they can’t use from each service provider. This token is presented to other applications, APIs, and services. To use your token to access repositories from the command line, select repo. An access token enables an OAuth client to make calls to an API. You’re expected to discard the old refresh token.OAuth (Open Authorization) is an open standard for token -based authentication and authorization on the Internet. Your server generates a JWT token for the user.OAuth (short for open authorization) is an open standard for access delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without .When you are using OAuth, you outsource user authentication and authorization to a central identity provider (IdP). Set the following x-www-form-urlencoded parameters as appropriate for your app. 2016google oauth – How can I get an oauth2 access_token using Python .To use the refresh token, make a POST request to the service’s token endpoint with grant_type=refresh_token, and include the refresh token as well as the client credentials if required.Get Access Tokens. 2016What are the main differences between JWT and OAuth .0 access token is a string that the OAuth 2. The scope of an . The RingCentral API will return refresh tokens with a static time so the user does not have to auth again if token refreshes and refresh .Twitch Token Generator Information.Roles OAuth defines four roles: resource owner An entity capable of granting access to a protected resource. They are sent at layer 7 of the OSI model.0 access token acts like a digital key granted to an application by an authorization server, after the user’s consent.Token Request – OAuth 2. The application requests user login and receives an authentication token from the authentication service.0 client uses to make requests to the resource server, and hides the user’s identity or other information from the OAuth 2.Security; Security alert: Attack campaign involving stolen OAuth user tokens issued to two third-party integrators. It is based upon the OAuth 2.User tokens gain the resource-based OAuth scopes requested in the installation process (e.If the request to the 3rd party API is directly from the mobile app, store the access token on the phone, encrypted with a unique key for each user stored in your server’s database.For example, we can use OAuth 2. Using such a centralized service has a number of advantages: One . How OAuth Works .
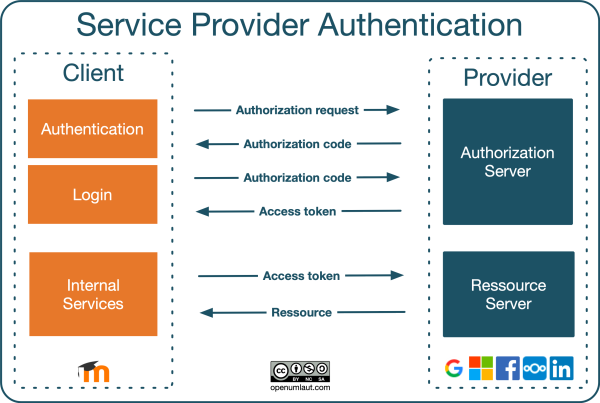
What is OAuth used for? OAuth can be used both for authorizing users and for allowing one application partial access to another application. The provider URL, client ID, and client secret must be set to the correct values for your application.0 for authorization and OIDC for authentication. Users sign in to the IdP and are granted time-bound permissions in the form of an access token.It really depends on the AS’s token format/strategy – some tokens are self-contained (like .
What is OAuth?
The access token represents the authorization of a specific application . The valid characters in a bearer token are alphanumeric, and the following . Upon authorization, your access token .tv/oauth2/token.To get an access token, send an HTTP POST request to https://id. Optionally, to copy the new token to your clipboard, click . This provides a very basic idea of what an ID token is: proof of the .

You can give each consumer a different valet key.
What is OAuth? Definition and How it Works
0 verwendet Tokens zur Autorisierung eines Zugriffs auf geschützte Ressourcen.
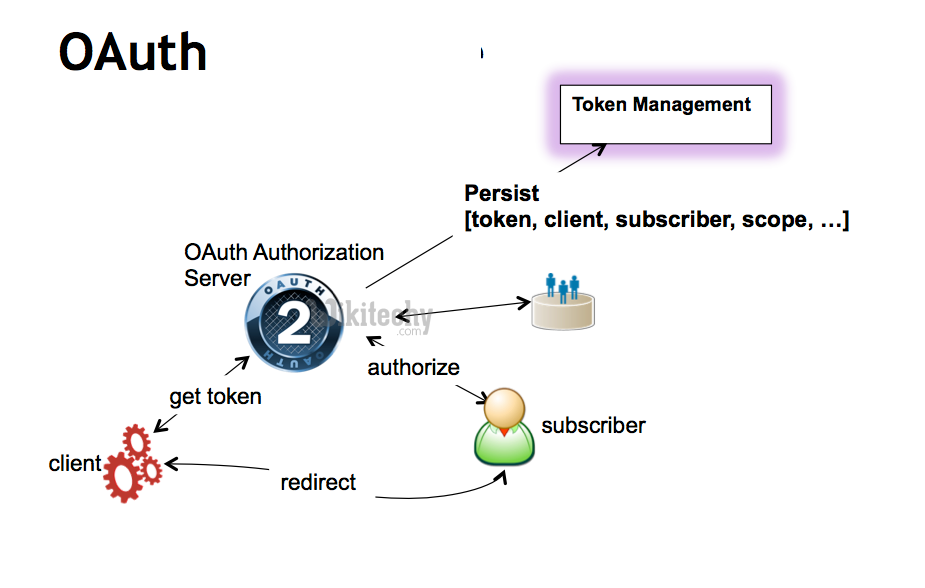
0, which stands for “Open Authorization”, is a standard designed to allow a website or application to access resources hosted by other web apps on behalf of a user.0 spec says: The authorization server MAY issue a new refresh token, in which case the client MUST discard the old refresh token and replace it with the new refresh token.0, a widely adopted protocol for securing APIs, relies on two key components: access tokens and refresh tokens.
Get Access Tokens
When the user is redirected back to our app, there will be a code and state parameter in the query string.0 uses Access Tokens and Refresh Tokens. Click Generate token. To access your API, you must request an access token when authenticating a user.OAuth tokens are typically sent using HTTPS, meaning they are encrypted.RFC 6749 OAuth 2.A user sends their username/password to your server at some URL like /login. While the device is waiting for the user to complete the authorization flow on their own computer or phone, the device meanwhile begins polling the token endpoint to request an access token.Postman supports using access tokens or ID tokens for OAuth 2.In the LinkedIn API, when you refresh access tokens, you will receive a refresh token with a decreasing refresh_token_expires_in property targeting the original refresh token expiry time until you are required to auth again.An OAuth token is like that valet key.0 is one of the most popular authorization frameworks out there.Obtain a user authentication token.0 Playgroundoauth. It may use the token to access the user’s account via the service API, limited to the scope of access, until the token expires or is revoked.0 Bearer tokens is actually described in a separate spec, RFC 6750. Here’s why access tokens are important: Security: Access tokens eliminate .An OAuth Access Token is a string that the OAuth client uses to make requests to the resource server.Derzeit gibt es zwei Möglichkeiten, einen Benutzer zu authentifizieren und einen Client zu autorisieren: OAuth 2.3 and section 6 of the OAuth 2. Write actions .0 (offener Standard) X-SDS-Auth-Token (proprietär)Select the scopes you’d like to grant this token. Dadurch kann einem Client Zugriff auf geschützte Ressourcen gewährt werden, ohne die .This code will create an OAuth2Session object using the oauthlib library and use it to get an access token from the OAuth2 provider.
OAuth
Access tokens do not have to be in any particular format, and in . The application attaches the user’s .0 authorization. You will be prompted by Twitch to authorize your account with the selected scopes. The result of that authentication process based on OpenID Connect is the ID token, which is passed to the application as proof that the user has been authenticated. Original Answer: The OAuth 2.comEmpfohlen auf der Grundlage der beliebten • Feedback
The Definitive Guide to OAuth Tokens
The format for OAuth 2. To query login attempts by Snowflake users, Snowflake provides a login history: LOGIN_HISTORY , LOGIN_HISTORY_BY_USER (table function).OAuth is a technical standard for authorizing users. resource server The server hosting the protected resources, capable of accepting and responding to protected resource requests using . This developer tool is used to generate tokens for use with the Twitch API, Twitch Chat, and Twitch PubSub! To use the tool, simply select the scopes you want and click ‚Generate Token!‘.While the authorization code grant allows for the three-legged flow to authenticate an end user and obtain a token with the subject of the authenticated user. They show you how to use Universal Login and Auth0’s language- and framework-specific SDKs. One use case that users often encounter is allowing an app to access a social media . A token with no assigned scopes can only access public information. They never have the full key or any of the private data that gives them access to the full key. When the resource owner is a person, it is referred to as an end-user. What’s the difference between OpenID and OAuth? Weitere Ergebnisse anzeigen0 is an open standard authorization framework for token-based authorization on the internet. You can also request tokens using the /api/o/token endpoint by specifying null for the application type.Client Credentials
What is an Access Token
- Led Unterputznetzteil 15W – Unterputz LED Netzteil 14V DC 8W TYP: ZNP-08-14
- Antena 3 Hd Online, Tv Online | Watch Antena 3 online
- Brot Und Baguette Motto | Bäckerei für Brotverliebte
- Tarifgehalt Pka 2024 , So viel verdienen Apotheker, PTA und PKA im Mittel
- Ising − Waging Am See , Routenplaner München
- Kostenlos Collage _ The Father
- Gibt Es Noch Eine Alternative Zum Atmel Studio?
- How To Redeem A Itunes Japan Gift Card
- Auto Und Transporter Mieten In Berlin Reinickendorf
- Rollstuhlbeförderung Fahrzeuge