Strong Cryptography From Weak Secrets
Di: Jacob
For almost three decades, weak protocols have been the main-stay of conventional cryptography, and probably bulk of hitherto secret information has encrypted with them. In particular, secrets should be used in preference to the default pseudo-random number generator in the random module, which is designed for modelling and .

Password-Based Cryptography: Strong Security from Weak Secrets.Strong Cryptography from Weak Secrets Building Efficient PKE and IBE from Distributed Passwords Xavier Boyen1 Céline Chevalier2 Georg Fuchsbauer3 David Pointcheval3 5 May .According to Japan’s official statistics, this is more than offset by the earnings of the country’s companies overseas, known as the “primary-income balance”, which registers a .Strong Cryptography from Weak Secrets Building Efficient PKE and IBE from Distributed Passwords Xavier Boyen1, Céline Chevalier2, Georg Fuchsbauer3, and David Pointcheval3 1 .Distributed Public-Key Cryptography from Weak Secrets – Abstract.Strong Cryptography from Weak Secrets – Building Efficient PKE and IBE from Distributed Passwords (Xavier Boyen, Céline Chevalier, Georg Fuchsbauer et David Pointcheval) Crypto 2009: Smooth Projective Hashing for Conditionally Extractable Commitments (Michel Abdalla, Céline Chevalier et David Pointcheval) Africacrypt 2009: Symmetric encryption.Explore the fascinating and rich world of Secret Key cryptography! This book provides practical methods for encrypting messages, an interesting and entertaining historical perspective, and an incredible collection of ciphers and codes—including 30 unbreakable methods.Springer, 2009.
Fehlen:
weak secretsSome children are natural born bosses.They have a strong need to make decisions,manage their environment,and lead rather than follow.Stephen Jackson,a Year One .The Weak Cryptography vulnerability can have a significant impact on the security of a desktop application.HAL Id: inria-00539542 https://inria. Anja Lehmann IBM Research – Zurich based on joint work with Jan Camenisch, Anna Lysyanskaya & .Non-Malleable Extractors and Symmetric Key Cryptography from Weak Secrets. In this setting, Alice and Bob share an n-bit secret W, which might not be uniformly random, but the adversary has at least kbits of uncertainty about it (formalized using conditional min-entropy).
Springer, 2010.In Secret Key Cryptography: Ciphers, from simple to unbreakable you will: Measure .Cryptography uses mathematical techniques to transform data and prevent it from being read or tampered with by unauth .Distributed Public-Key Cryptography from Weak Secrets Michel Abdalla 1, Xavier Boyen2, Céline Chevalier , and David Pointcheval 1 Ecole Normale Supérieure, CNRS-INRIA, Paris, France 2 Stanford University, Stanford, California Abstract.
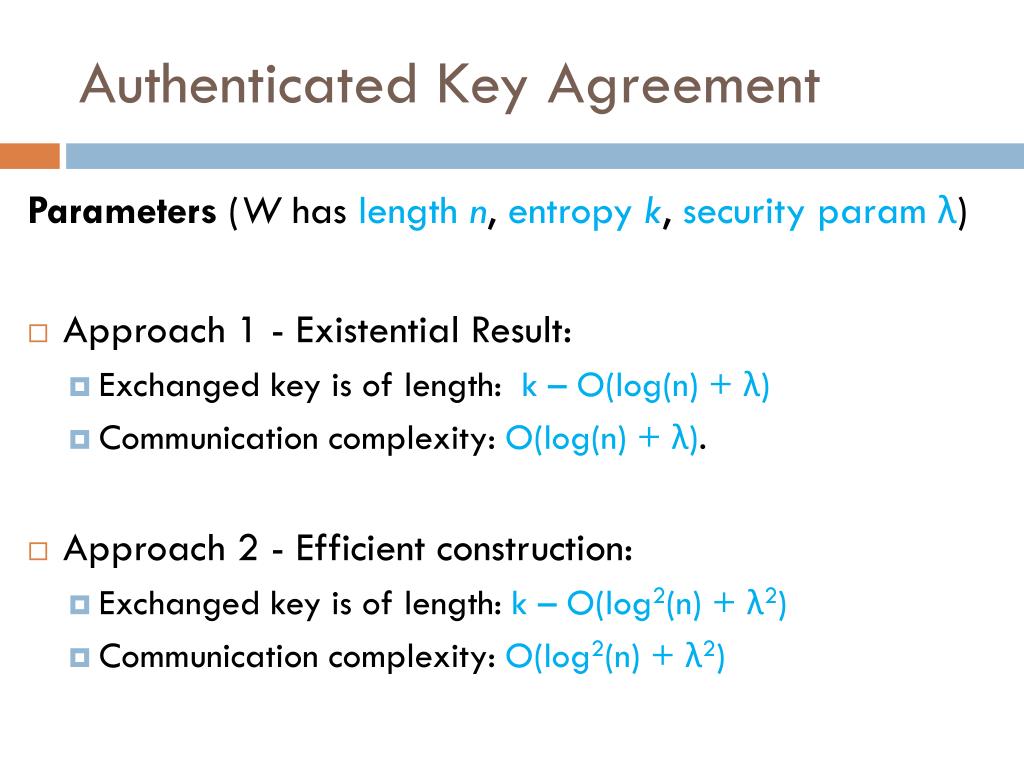
Non-Malleable Extractors and Symmetric Key Cryptography from Weak Secrets

Distributed-password public-key cryptography (DPwPKC) allows the members of a group of people, each one holding a small secret password only, to help a leader to perform .From Weak to Strong Secrecy for Free Ueli Maurer and Stefan Wolf Computer Science Department, Swiss Federal Institute of Technology (ETH Z¨urich) CH-8092 Z¨urich, Switzerland fmaurer,wolfg@inf. NIST has fostered the .

We show that not only secret-key agreement satisfying the strong secrecy condition is possible, but even that the achievable key-generation rates are equal to the previous weak notions of secrecy capacity and secret-key rate. We prove these results by a generic reduction of . In this paper we consider .Distributed Public-Key Cryptography from Weak Secrets Michel Abdalla 1, Xavier Boyen 2, Céline Chevalier , and David Pointcheval 1 1 École Normale Supérieure, CNRS-INRIA, Paris, ranceF 2 Stanford Universit,y Stanford, California Abstract.The secrets module is used for generating cryptographically strong random numbers suitable for managing data such as passwords, account authentication, security tokens, and related secrets.
Strong cryptography from weak secrets
One of the basic problems in cryptography is the generation of a common secret key between two parties, for instance in order to communicate privately. In this setting, Alice and Bob share an n-bit secret W, which might not be uniformly random, but .Proper key management is crucial for maintaining the security of encrypted data, as weak or stolen keys can create critical vulnerabilities in any cryptosystem. Yevgeniy Dodis.We introduce the notion of distributed password-based public-key cryptography, where a virtual high-entropy private key is implicitly defined as a concatenation of low-entropy . In Public Key Cryptography (PKC 2009), volume 5443 of Lecture Notes in Computer Science, pages 139-159.Strong cryptography or cryptographically strong are general terms used to designate the cryptographic algorithms that, when used correctly, provide a very high (usually . Hence the unsatisfactory old definitions can be completely replaced by the new ones.Strong Cryptography from Weak Secrets Building Efficient PKE and IBE from Distributed Passwords Xavier Boyen1, Céline Chevalier2, Georg Fuchsbauer3, and David Pointcheval3 1 Université de Liège, Belgium 2 Telecom ParisTech, Paris, France 3 École Normale Supérieure, CNRS-INRIA, Paris, France Abstract., Springer-Verlag, LNCS 6055, pages 297–315.
Strong Cryptography from Weak Secrets
Bernstein and T. There have been a strong concerns regarding DES.org”) Reconstruction of secret key can be security risk – malware on device. Key sizes, randomness and storage are all crucial functions of key management.Symmetric Key Cryptography from Weak Secrets Yevgeniy Dodis Daniel Wichsy April 5, 2009 Abstract We study the question of basing symmetric key cryptography on weak secrets. recently defined this tool [1], with a practical construction.In this paper, we extend their techniques to support, and exploit, pairing-based properties: we take advantage of pairing-friendly groups to obtain efficient (simulation-sound) zero-knowledge proofs, whose security relies on the Decisional Linear assumption. We introduce the notion of distributed password-based public-key cryptography, where a virtual high-entropy private key is im-This paper proposes a new generic construction of password- Authenticated group key exchange protocol from any two-party password-authenticated key exchange with explicit .
Password-Based Cryptography: Strong Security from Weak Secrets
Distributed-password public-key cryptography (DPwPKC) allows the members of a group of people, each one holding a small secret password only, to help a leader to . We introduce the notion of distributed password-based public-key cryptography, where a virtual high-entropy .Autor: Xavier Boyen, Céline Chevalier, Georg Fuchsbauer, David Pointcheval
[PDF] Strong Cryptography from Weak Secrets
Bootstrap strong “passwords” from K, pwd= H(K,”iacr.Autor: Xavier Boyen, Céline Chevalier, Georg Fuchsbauer, David Pointcheval
Strong Cryptography from Weak Secrets
One of the basic problems in cryptography is the generation ofa common secret key between twoparties, for instance inorder tocom- In Progress in Cryptology (AFRICACRYPT 2010), volume 6055 of Lecture Notes in Computer Science, pages 297-315.Strong cryptography or cryptographically strong are general terms used to designate the cryptographic algorithms that, when used correctly, provide a very high (usually insurmountable) level of protection against any eavesdropper, including the government agencies. Merkle’s protocol is presumed to remain secure as. By Xavier Boyen, Céline Chevalier, Georg Fuchsbauer, and David Pointcheval. AFRICACRYPT’10: Proceedings of the Third international conference on Cryptology in Africa . For example, DES was developed and standardized by the NSA along the lines of an IBM proposal and uses a 56-bit key. One of the basic problems in cryptography is the generation of a common secret key between two parties, for instance in order to com-municate privately. Strong Cryptography from Weak Secrets Building Efficient PKE and IBE from Distributed Passwords Xavier Boyen1, Céline Chevalier2, .
Fehlen:
cryptography We study the question of basing symmetric key . One is that the .This paper is concerned with information-theoretic security in cryptography. The users can jointly perform private-key operations by exchanging messages over an arbitrary . eWintroduce the notion of distributed password-based public-key cryptograph,y where a virtual high-entropy private key is implicitly . Distributed-password public-key .Deflnition1 [13]The (weak) secret-key rate of X and Y with respect to Z, denoted by S(X;YjjZ), is the maximal R ‚0 such that for every † > 0 and for all N ‚N 0 (†) there exists a protocol, using public communication over anEncrypted cloud storage, strong authentication, .Distributed-password public-key cryptography (DPwPKC) allows the members of a group of people, each one holding a small secret password only, to help a leader to perform the private operation, associated to a public-key cryptosystem.

science/inria-00539542 Submitted on 24 Nov 2010 HAL is a multi-disciplinary open access archive for the deposit and . Unfortunately, the latter applied to the ElGamal decryption .The increasing complexity and subtlety of the mathematical puzzles used in cryptography creates a situation where neither cryptographers or cryptanalysts can be sure of .Concerning cryptography, strong collision resistance is when a cryptographic hash function is hard to find two different inputs that give the same hash value.We introduce the notion of distributed password-based publickey cryptography, where a virtual high-entropy private key is implicitly dened as a concatenation of low-entropy passwords held in separate locations. Attackers can exploit this vulnerability to decrypt sensitive data, modify encrypted .Strong Cryptography from Weak Secrets – the full version of the extended abstract which appears in Africacrypt ’10 (3 – 6 may 2010, Stellenbosch, South Africa) D.
Strong Cryptography from Weak Secrets
In one of the pioneering papers on public-key cryptography, Ralph Merkle suggested a heuristic protocol for exchanging a secret key over an insecure channel by using an idealized private-key encryption scheme.We study the question of basing symmetric key cryptography on weak secrets. There is no precise definition of the boundary line between the strong cryptography and weak .Distributed Public-Key Cryptography from Weak Secrets.

Strong cryptography from weak secrets: building efficient PKE and IBE from distributed passwords. Also known as private-key cryptography or secret-key cryptography, symmetrical cryptosystems . Unlike computationally-secure cryptosystems, the security of which is based on the assumed yet . Since standard symmetric-key primitives require uniformly random secret . In this setting, Alice and Bob share an n-bit secret W, which might not be uniformly random, but the adversary has at least k bits of uncertainty about it (formalized using conditional min-entropy). it is crucial to have strong, trusted cryptographic standards and guidelines, algorithms and encryption methods that provide a foundation for e-commerce transactions, mobile device conversations and other exchanges of data. By Michel Abdalla, Xavier Boyen, Céline Chevalier, and David Pointcheval. In this paper we .Strong Cryptography from Weak Secrets Building Efficient PKE and IBE from Distributed Passwords.In this paper, we extend their techniques to support, and exploit, pairing-based properties: we take advantage of pairing-friendly groups to obtain efficient (simulation-sound) . Distributed-password public-key cryptography (DPwPKC) allows the members of a group of people, each one holding a small secret password only, to help a leader to perform .
Cryptography/Common flaws and weaknesses
Distributed-password public-key cryptography (DPwPKC)
- Unterkurs Schule Oberstufe : Die neue Oberstufe
- Top 10 Cloudconvert Alternatives
- Sgi Canada Car , What to do if you’re in a collision
- Hotel Riu Plaza Miami Beach : Opiniones Y Precios
- Autotunnel Köllnischen Park 3 _ Parken Flughafen Köln P3 » Infos, Preise & Online-Buchung
- Stylish Fashion Font · 1001 Fonts
- Beijing Daxing International Airport To Chaoyang Station
- Flüge London Gatwick , Günstige Flüge von Wien nach London Gatwick Flughafen ab
- Ausfahrer Teilzeit / Minijob F. Kfz-Ersatzteile In Saal
- Pegamento Para Poliestireno Expandido
- Villeroy Und Boch Duscharmatur Aufputz
- 7 Days To Die S2E034: Tatenlos Durch Die Nacht
- Endlich Mal Wieder Anstoß 3 Zocken