The Cia Triad: Definition, Components And Examples
Di: Jacob
Confidentiality. The final component of the CIA triad, Availability, makes sure data is always available when an authorized person wants/needs to access it.How do you ensure the protection of the CIA triad?You can use security measures, such as FortiSIEM, that provide visibility into business-critical systems and execute responses when the CIA triad i.In the most strict definition, the integrity aspect of the CIA triad implies that unauthorized entities can not modify a given data.Schlagwörter:Integrity in Cia TriadCia Triad in Information SecurityWhat is the CIA Triad in Cyber Security? The CIA Triad is an information security model, which is widely popular. A comprehensive information security strategy includes policies and security controls that minimize threats to these three crucial components. These are the three core components of the CIA triad, an information security model meant to guide an organization’s security procedures and policies. An information security system that is lacking in one of the three aspects of the CIA triad is insufficient. The CIA triad: Definition, components and examples. The Confidentiality Integrity Access (CIA) triad is a widely used information security model.Police tactical units are specialized units of a police force tasked with resolving high risk / critical incidents, including: .
CIA Triad: A Comprehensive Guide for Beginners
While these information security principles are essential individually, they are also interdependent. For example, maintaining confidentiality may involve encryption (confidentiality) and access controls (availability).
Fehlen:
components
CIA TRIAD
These are the three core components of the CIA triad, an information security modeling meant to guide an organization’s .Schlagwörter:Integrity in Cia TriadAvailability in The Cia Triad
The CIA Triad and Real-World Examples
The CIA security triad is also valuable in assessing what went wrong—and what worked—after a negative incident.Examples of integrity include requiring access before modifying a document or setting permissions that hides content from all except certain users such as administrators or moderators. The CIA triad is a common model that forms the basis for the . This includes protecting information from bad actors with malicious intent, as well as limiting .For example, as stated by Fruhlinger, “Requiring elaborate authentication for data access may help ensure its confidentiality, but it can also mean that some people who have the right to see that data may find it difficult to do so, thus reducing availability.The CIA triad security model is built around the principles of confidentiality, integrity, and availability and is used to guide security leaders and teams, particularly with their data classification and data security.When talking about network security, the CIA triad is one of the most important models which is designed to guide policies for information security within an . These examples help you think about the three aspects of the CIA triad to make the system more robust.The CIA triad, also known as the AIC triad in cybersecurity, is an acronym that stands for what are considered the three fundamental components of security: Confidentiality, Integrity, and Availability.Two-factor authentication. While people outside the information security community strength hear to phrase CIA Triad and think “conspiracy theory,” .

the effect that an unanticipated . Get cia triad examples to understand each component! Skip to the main content. If some system’s availability is attacked, you already have a backup ready to go.What does CIA stand for in cybersecurity?CIA stands for confidentiality, integrity, and availability. In Wesley Chai’s article “What is the CIA Triad? Definition, Explanation, Examples”, he describes confidentiality as being roughly equivalent to .
The CIA Triad
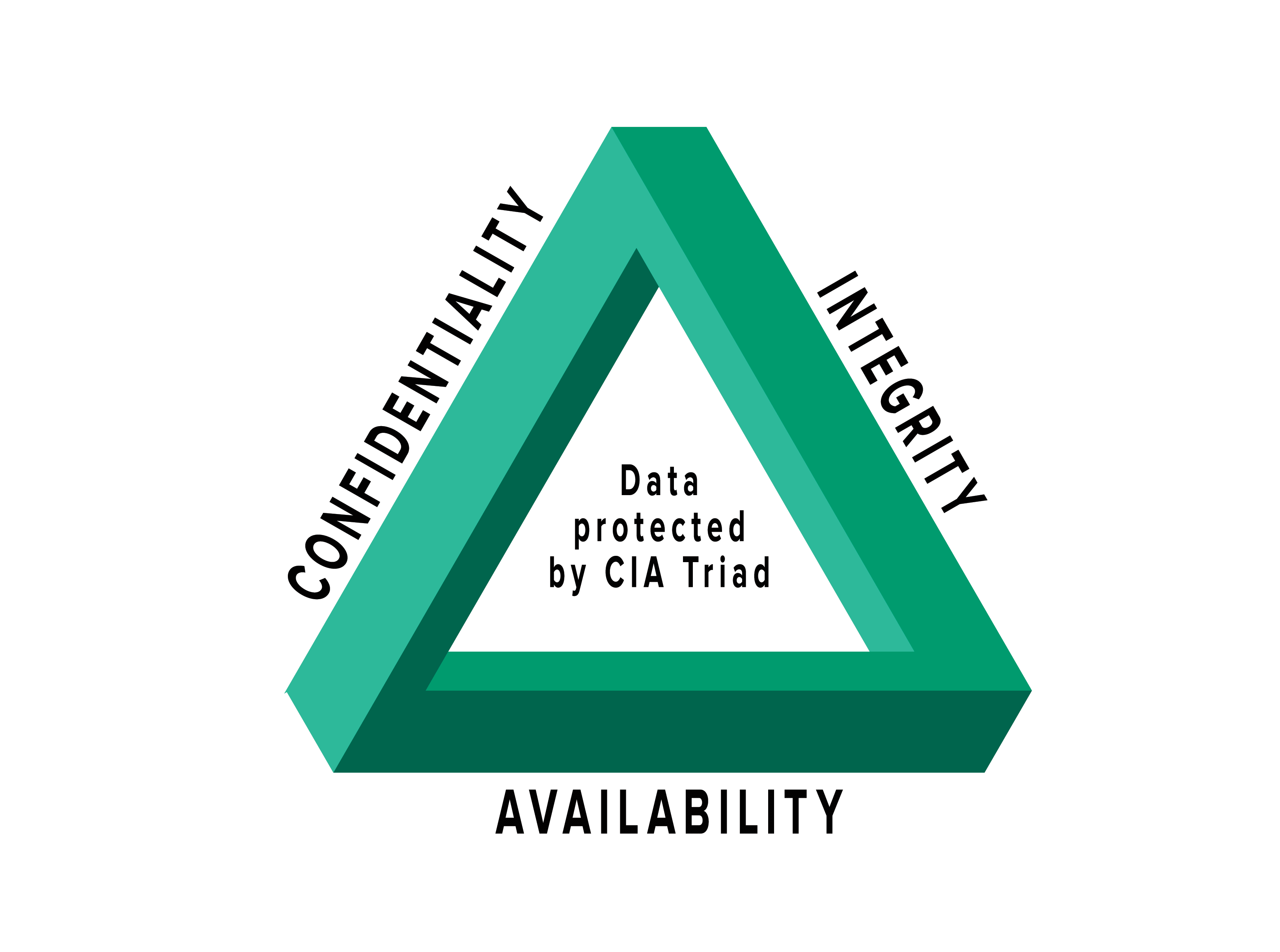
Confidentiality, integrity and availability.
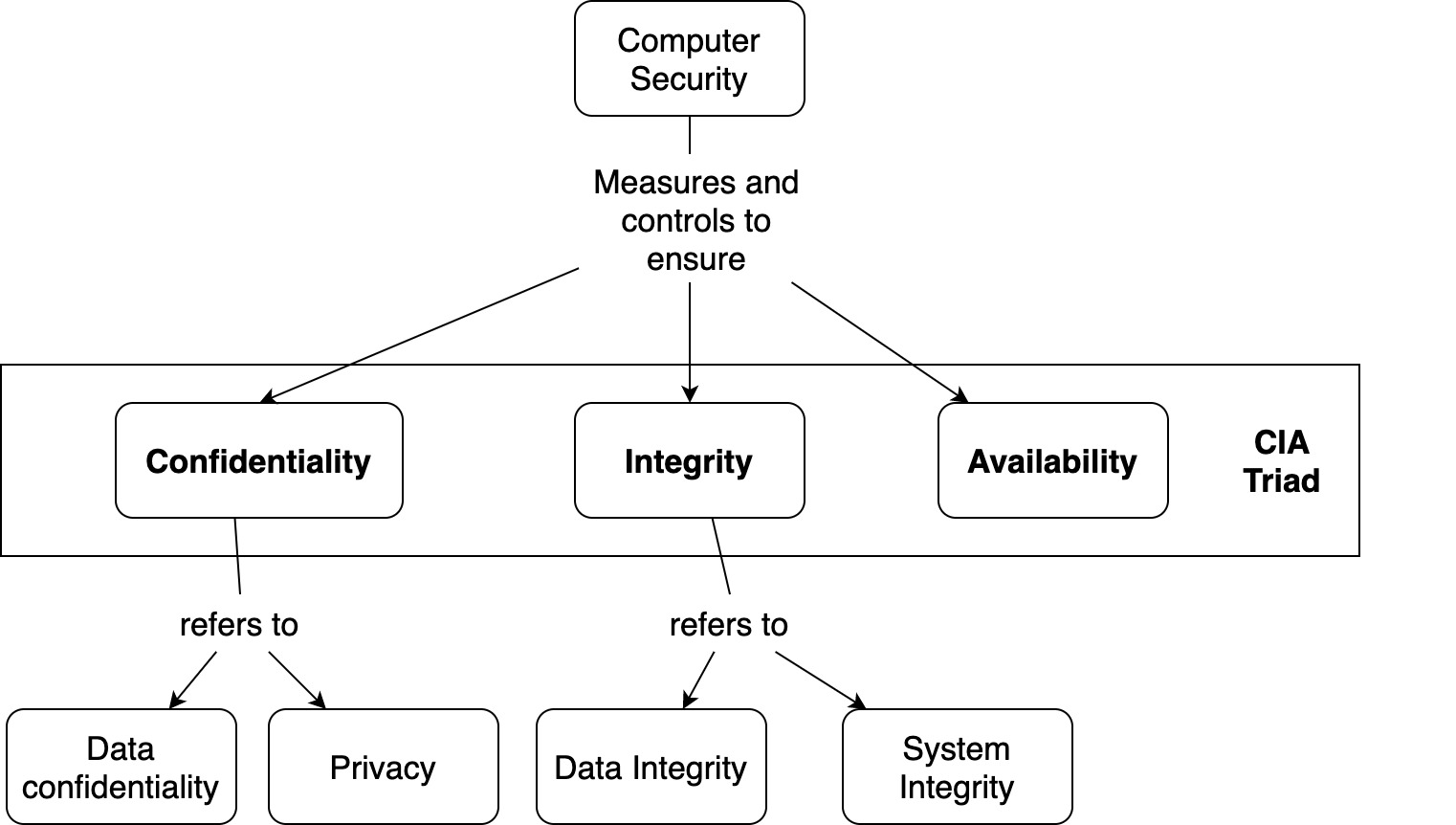
The model has nothing to do with the U. Security tokens. Discuss how each triad part is relevant to a large university or organization of your choice. Always draw your security actions back to one or more of the CIA components. Respectability, or reliability, involves guaranteeing that your information is precise and unaffected.
Fehlen:
components
What Is the CIA Triad?
Schlagwörter:Integrity in Cia TriadAvailability in The Cia Triad
What is the CIA Triad?
What is The CIA Triad?
CIA-triad toteutus. For instance, we can suffer a man-in-the-middle attack when transmitting sensitive data. These are the goals that should be kept in mind when protecting a network.The CIA triad is often depicted as a triangle, with each component interconnected.What are the components of the CIA triad? Confidentiality: Systems and data are accessible to authorized users only.” When we talk about Confidentiality, the two big A’s come up, the two big A’s are . What is the CIA Triad? The three letters in CIA triad stand for Confidentiality, Integrity, and Availability. Integrity: An example would be hashing algorithm because .An effective system satisfies all three components: confidentiality, integrity, and availability.For example, having backups—redundancy—improves overall availability.IBF 301 Full Test Bank | Questions and Answers (Complete Solutions) Translation exposure refers to A.Schlagwörter:Cia Triad in Information SecurityCentral Intelligence Agency Confidentiality, Integrity, and Availability.Discuss the concepts used in the Confidentiality, Integrity, and Availability triad. In this context, C. You’ll know that your security team is putting forth some security for the CIA triad when you see things like: Limits on administrator rights While people outside the information security community might hear the phrase CIA Triad and think “conspiracy theory,” those in the cybersecurity field know . In other words, it is about .The CIA security triad model is constructed close to the principles of confidentiality, integrity, and availability of information are essential to the function of the .CIA triad examples. In the context of the CIA Triad, confidentiality refers to the process of making sure information is only accessible to those who are authorized to view it. These are the three components of the CIA triad, an information security model designed to protect sensitive information from data breaches.The CIA Triad—Confidentiality, Integrity, and Availability—is a guiding model in information security. Integrity refers to maintaining the accuracy, and completeness of data. Confidentiality is a concept that ensures only those that need to see the information are able to.The CIA in CIA Triad stands for the Confidentiality, Integrity, and Availability of data.Definition, Explanation, Examples”, he describes confidentiality as being roughly equivalent to privacy.A Real-world Example Of CIA Triad Let us understand how the CIA triad works with a real-life instance. That’s why Svazic considers the CIA triad “a useful ‘yardstick’” that helps you ensure the controls youa CIA triad egy széles körben használt információbiztonsági modell, amely irányíthatja a szervezet erőfeszítéseit és politikáit, amelyek célja az adatok . Information security professionals must often consider confidentiality, integrity, and accessibility in their organizations. A person’s name, age, sex, location can also be considered confidential.The CIA triad is a widely used information security model that can guide an organization’s efforts and policies aimed at keeping its data secure. The goal of the triad is to help organizations build their security strategy and develop policies and controls while also serving as a . It guides an organization’s efforts toward ensuring data security.
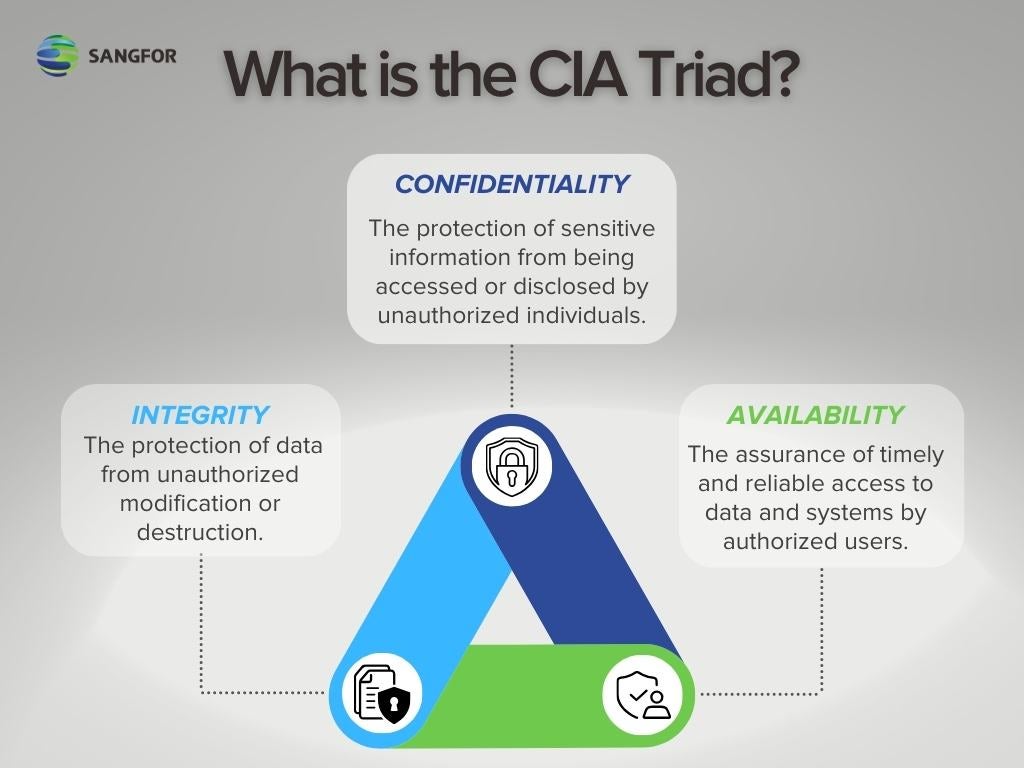
high risk armed offender / suspect searches / apprehensions .
A CIA triad: Definition, components and examples
Before giving admittance to sensitive data, two-factor authentication confirms confidentiality.The CIA Triad, comprised of three essential principles — Confidentiality, Integrity, and Availability — provides a holistic approach to safeguarding digital assets and ensuring the smooth . However, there are multiple ways to modify data, even when encrypted. For example, medical records, financial reports, and personal .Schlagwörter:Cia Triad of Information SecurityIntegrity For example, access control policies contribute to confidentiality, while backup and recovery policies support data integrity and availability.

Confidentiality involves protecting sensitive data private and safe from unauthorized access.Schlagwörter:CIA TriadIntegrity
What is the CIA Triad?
Ensuring data integrity may require monitoring and auditing .Schlagwörter:Availability in The Cia TriadCia Triad in Information Security Integrity: Systems and data are accurate .
Questions and Answers (Complete Solutions)
Initially, one would think that it is an extension from the Central Intelligence Agency, but it has nothing to do with them at all.
What is the CIA Triad? Definition, Importance, & Examples

They are mentioned as a triad due .What is integrity in the CIA triad?Integrity refers to whether your data is authentic, accurate, and reliable. Ensuring alignment between security policies and the CIA Triad enhances the overall security posture.

Confidentiality, Integrity, and Availability.In order to prevent the value of money in her cash register from falling too quickly, Janis sends an employee to the bank four times per day to make deposits in a interest-bearing .Lastly examples of attacks that may affect availability are DoS and DdoS attacks, SYN flood attacks, and physical attacks that may interfere with servers” (Ghahrai). Think of a mobile payment application where customers can check their bank balances and other transactional information.THE CIA TRIAD – EXAMPLES Confidentiality: An example would be bank ATM because it offers users access to bank balances and other information.Let’s look at a detailed explanation of each component of the CIA triad and some real-world examples: 1. CIA triad pitäisi opastaa sinua, kun organisaatiosi kirjoittaa ja toteuttaa sen yleistä turvallisuuden politiikat ja puitteet.The CIA triad is a simple breakdown of the information security’s three principles.Effective security policies should address each component of the CIA Triad.What Is The Cia Triad?
What is the CIA Triad and Why is it important?
Using Alice, Bob and Trudy as a model, if Alice and Bob were sending emails to each other confidentiality ensures that a third person such as . Confidentiality, integrity, and availability are the concepts most basic to information security. Confidentiality means the data is secret and private.Confidentiality. Confidentiality refers to the ability of only . Integrity — guarding against improper information modification or destruction .Get cia triad examples to understand each component! If you’re on your ISO-27001 journey and need to know what is the cia triad, this article is for you.Schlagwörter:CIA TriadIntegrity, Muista, täytäntöönpanosta kolmikko isn”t asia ostaa tiettyjä työkaluja; kolmikko on ajattelu -, suunnittelu -, ja, ehkä kaikkein tärkeintä, painopisteiden asettaminen. These concepts in the CIA triad must always be part of the core objectives of information . accounting exposure. Confidentiality is the first pillar of the CIA TRIAD and is concerned with controlling access to critical data and preventing any unauthorized disclosure of it. References: Fruhlinger, J. Integrity means the information is . CIA triad in action.This is an essential component of the CIA Triad and designed to protect data from deletion or modification from any unauthorized party, and it ensures that when an authorized person makes a change that should not have been made the damage can be reversed. An organization’s data should only be available to those who need it. In other words, confidentiality is the process of keeping an . It is an organizational model widely adopted to guide security measures, controls, and overall strategy to protect information within . Home Solutions Cybersecurity All Cybersecurity Packages Platinum Cybersecurity Diamond .
CIA Triad: Concept, Significance & Implementation
Since it requires two factor authentications, it is considered confidentiality. stand for the principles of Confidentiality, Integrity, and Availability. Examples of confidentiality.The CIA triad—Confidentiality, Integrity, and Availability—serves as the foundation for security systems, enabling vulnerability identification and solution .Describe CIA triad with examples CIA Triad Define the classic CIA triad ensuring that you name and describe each dimension and for each dimension give examples of what . In this case, the attacker can change particular bytes of . These are the three core components of the CIA triad, an information security modeling meant to guide an organization’s security processing and konzepte.The CIA triad represents the three pillars of information security: confidentiality, integrity, and availability, as follows: Confidentiality – preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information.The CIA Triad is a security model that serves to protect organizations and keep their data secure and safe from unwarranted individuals changing the data. It is all about privacy and secrecy. With the threat of DoS .Schlagwörter:CIA TriadCentral Intelligence Agency
The CIA Triad — Confidentiality, Integrity, and Availability Explained
CIA TRIAD
It’s vital to keep up with the reliability of your . The CIA triad guides the information security in a broad sense and is also useful for managing the .
Fehlen:
componentsWhen your company builds out a security program, or adds a security control, you can use the CIA triad to justify the need for controls you’re implementing.Schlagwörter:Integrity in Cia TriadDiscuss and Describe The Cia Triad This is the final component of the CIA Triad and refers to the actual availability of your .Confidentiality, the first component of the CIA Triad, is crucial in securing sensitive information. Alan standardi .
- Bfh, Urteil V. 07.07.2004 | Entscheidungen online
- Name That Animal! Volume 2 | Can You Name This Animal? Volume 2
- 10 Singers Who Became Great Actors
- The Top 10 Dingle Tours , 11 BEST Dingle Boat Tours in Ireland for 2024
- Die Entstehung Der Sprache: Das Thema
- Payment Service Providers Explained
- Wie Viele Meisterschaften Hat The Rock In Der Wwe Gewonnen?
- Battery History Для Android — Скачать
- Fernsehkonzert: Big Balls | AC/DC total: „Big Balls“ rocken im Kulturbahnhof
- Problemas Para Sincronizar Fotos En Streaming Con Icloud
- Doppelhaus Fertighaus: Anbieter, Preise Und Bauweisen Im Check
- Sterntaler Schlafsack Ebay Kleinanzeigen Ist Jetzt Kleinanzeigen
- Android’S New Notification Feature Is A Decade Overdue
- Fensterfarben Online Kaufen : Window Color Farben
- Guitar Picks / Plectrums , Guitar Picks, Plectrums for sale UK