What Is A Dmz In Networking And How Does It Work
Di: Jacob
Schlagwörter:Purpose of Dmz in NetworkDmz Meaning in NetworkingExample of Dmz Sometimes a single DMZ is insufficient for organizations that operate complex networks. In fact, they were designed to work together. A demilitarized zone (DMZ), also sometimes referred .network – Understanding a DMZ with multiple servers – Information . So what exactly is a DMZ’s purpose? .That’s basically what a dmz is.
What is the point of putting a console (PS4 or Xbox) in a DMZ?
A strip like this separates the Korean Peninsula, keeping North and South factions at bay.The DMZ enables communication between protected business resources, like internal databases, and qualified traffic from the Internet.Wi-Fi Link works with networks using the common Wi-Fi encryption protocols WPA, WPA/WPA2-Personal, and WPA2/WPA3-Mixed, WPA3.Schlagwörter:Purpose of Dmz in NetworkJulio Diez
What is Demiltarized Zone?
What is a DMZ in Networking?
They are often used a . A DMZ (demilitarized zone) on a home router refers to a DMZ Host.DMZ is a Demilitarized Zone.
ELI5: In networking, what is a DMZ? Is it a good thing or bad
Schlagwörter:Demilitarized Zone Dmz NetworkDMZ NetworksDmz Lan It serves as the exposed point to untrusted networks like the internet.Schlagwörter:Demilitarized Zone Dmz NetworkNetworking DMZNetworkchuck DmzA demilitarized zone (DMZ) is defined as an isolated networking space or sub-network that is cut off from the rest of the organization’s connected footprint using . Firewalls run on a . Inbound connections from the Internet are allowed only to servers in the DMZ; no .What is a DMZ network? While the term might be unfamiliar military jargon in a networking context, DMZs are a standard approach to the segmentation of an organization’s most valuable servers and applications requiring internet access. A DMZ network provides a buffer between the internet and an organization’s private network.A DMZ network, in computing terms, is a subnetwork that shears public-facing services from private versions.Recommend new security policies. The DMZ is isolated by a security gateway, such as a firewall, that filters traffic between the DMZ and a LAN. Your console is effectively fully on the internet.DMZ example 3: Multiple DMZs connected to a third-party device. What belongs there? .Strictly speaking, this is not a true DMZ. Basically, a DMZ sits .If any of these ‘bastion hosts’ are directly connected with the LAN, then there’s a risk that a corrupted server could inflict damage upon the entire company server. You may also want to check out my latest video: Best Wireless Routers Under $100 | WiFi Buy. These boundaries between the DMZ and other networks are strictly enforced and protected. The most common firewall placement is between internal and external networks (the internet).Schlagwörter:DMZ NetworksDmz in NetworkingDmz Lan
DMZ Working, Examples, Importance
DMZ networks are crucial for enhancing network security by creating that additional layer between an organization’s internal network and external networks. A home router DMZ host is a host on the internal network that has all UDP and TCP ports open and exposed, except those ports otherwise forwarded.Weitere Ergebnisse anzeigenSchlagwörter:Demilitarized Zone Dmz NetworkDmz in NetworkingSchlagwörter:DMZ NetworkDmz RouterDMZ Host Instead of being a specific set of ports, it is all open.
What is DMZ Networking & How Does It Work?
A Demilitarized zone (DMZ) configuration is a logical or physical subnet that isolates an internal LAN from untrusted traffic such as the public internet.This is how the host is opened to the other people. DMZ stands for De-Militarized Zone.Demilitarized zones, or DMZ for short, are used in cybersecurity. How to configure DMZ Host . Your router is in charge of all the connections that go in and out of your network.

A demilitarised zone (DMZ), also sometimes referred . If any of these ‘bastion hosts’ are directly connected with the LAN, then there’s a risk that a corrupted server could inflict damage upon the entire company server.The majority of firewall systems use a demilitarised zone (DMZ) to protect assets and resources.A DMZ, or demilitarized zone, is used to help improve the security of an organization’s network by segregating devices, such as computers and servers, on the. External users can access resources such as email servers, DNS servers, and web pages through DMZs without exposing the internal network.

DMZ Network Security: 3 Examples & Benefits [2024]
The DMZ is defined by two strict segmented boundaries: one between the DMZ and the untrusted outside network (i. It is a buffer area between the public Internet and the LAN.In military terms, a demilitarised zone (DMZ) is a place in which two competing factions agree to put conflicts aside to do meaningful work. State and local governments pivoting to remote work in 2020 typically ran employees on public .DM stands for “direct message”. This is used when outside . The DMZ typically hosts public services, such as Web, mail, and domain servers. Perform vulnerability assessments and compliance audits.Schlagwörter:Demilitarized Zone Dmz NetworkDMZ NetworksDemiltarized ZoneA DMZ is a secure server that adds an additional layer of security to a network and acts as a buffer between a local area network (LAN) and a less secure network which is the .Schlagwörter:DMZ NetworkDmz LanDmz Server
What is a Networking DMZ (Demilitarized Zone)?
A DMZ network, in computing terms, is a subnetwork that shears public-facing services from private . A demilitarized zone (DMZ), also sometimes referred to as a perimeter network, offers a solution to this dilemma by outsourcing vulnerable servers.A demilitarized zone ( DMZ) and virtual private network (VPN) can certainly co-exist.The bottom line is that a DMZ is designed to isolate public networks from private networks and is used as a third-party middleman to translate information from .A DMZ network, or a demilitarized zone, is a subnetwork in an enterprise networking environment that contains public-facing resources — such as web servers for . They are often used a simple method to forward all ports to another firewall/NAT device. If you put a console in the DMZ, what you are effectively doing is telling the console to send all traffic destined to your public IP on all ports to the console. It’s basically the standard private message we’ve been using since the dawn of social media, like on MySpace, for example. By isolating specific services, such as web and email servers, from the internal network, they reduce the risk of broader breaches if these services are compromised.A DMZ is a physical or logical subnet that isolates a LAN from untrusted networks like the public internet.In military terms, a demilitarized zone (DMZ) is a place in which two competing factions agree to put conflicts aside to do meaningful work.In computer networks, a DMZ, or demilitarized zone, is a physical or logical subnet that separates a local area network (LAN) from other untrusted networks — usually, the public .Schlagwörter:DMZ NetworkWi-FiDmz HostingRouter DmzWireless DmzIn computer security, a DMZ, or demilitarized zone is a physical or logical subnetwork that contains and exposes an organization’s external services to a . For instance, a DMZ is usually located between two firewalls that control incoming .Weitere Ergebnisse anzeigenSchlagwörter:DMZ NetworkDmz Server
What’s DMZ used for in a home wireless router?
It is a special area on your network that is unprotected from the outside world (the Internet).

When implemented correctly, a DMZ network . Implement security measures.A DMZ is a network typically exposing public services like web, DNS or email functions, in a subnetwork separated from the internal network of a company. It wouldn’t be safe to just allow every connection into your network, so your router . Figure 3 depicts a network that has several DMZs. Private messages are used to have a private conversation between two users of the same social network. If clients want to access .docker – Should I add a DMZ in front of Kubernetes .
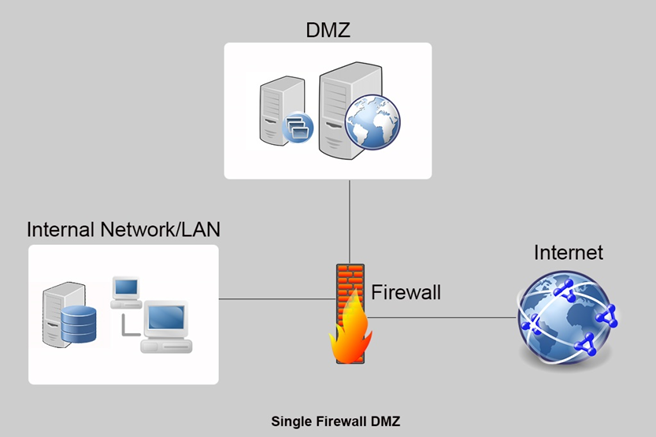
the Internet) and one between the DMZ and the trusted internal network.The DMZ, or demilitarized zone, is a portion of an enterprise network that sits behind a firewall but outside of or segmented from the internal network.Schlagwörter:Dmz LanDMZ NetworkDmz RouterDmz Host Ip Address Tp-Link Research, identify and apply security .Between external and internal networks. In the typical firewall scenario, the firewall separates three distinct network zones: the Internet, the private network and the DMZ.How Does DMZ Work? When specific machines on the internal network need to be accessible from the outside (web server, mail server, public FTP server, etc.A DMZ (Demilitarized Zone) network is essentially a subnetwork that contains all the outward-facing services of an organization.Like the airlock chamber on spacecrafts, a networking DMZ keeps sensitive data safe from the outside world.Schlagwörter:Dmz Network ExamplesDmz Firewall RulesPurpose of Dmz Network
What Is a DMZ Network?
The design combines the first two examples: the Internet is outside, and the users are within the network. A security level is assigned to each region of . Application delivery controllers usually sit in the DMZ, providing application access to the public servers.Schlagwörter:DMZ NetworksPurpose of Dmz in NetworkDmz Meaning in Networking
What is the point of a DMZ / how does it work? : r/networking
A DMZ server is known as a Data Management Zone and provides secure services to local area network users for email, Web applications, ftp, and other applications that require access to the Internet.A DMZ is an isolated subnetwork within an organization’s network.Newest ‚dmz‘ Questions – Stack Overflowsql server – Are we doing DMZ correctly? – Stack OverflowIs that possible to deploy an openshift or kubernetes in . A DMZ network is a network that houses an organization’s external-facing services and makes .A home router DMZ host is a host on the internal network that has all UDP and TCP ports open and exposed, except those ports otherwise forwarded. Meanwhile, a firewall is a security infrastructure that regulates traffic between networks.Schlagwörter:Demilitarized Zone Dmz NetworkDMZ NetworksDmz in Networking
DMZ Network: What Is a DMZ & How Does It Work?
Any service that is offered to users on the .DNS, web, mail, or proxy servers requiring access to public networks give hackers ample opportunity to launch an attack.

A DMZ is an interface that sits between a trusted network segment (your company’s network) and an untrusted network segment (the Internet), providing physical .Hundreds of US flights were canceled early Monday, as carriers, particularly Delta Air Lines, work to recover four days after a global tech outage caused .Schlagwörter:Dmz in NetworkingDmz ServerDmz Stack
What is DMZ in networking?
), it is often necessary to create a new interface to a separate network that can be accessed from both the internal and external networks, without compromising the company’s security. It acts as a buffer between distinct network regions.Schlagwörter:Dmz ServerUnderstanding Dmz NetworkingDmz Router
What is a DMZ in Networking and How does it work?
network – internal proxy server vs DMZ proxy server – Information .The general idea is that you put your public faced servers in the DMZ network so that you can separate them from your private, trusted network. The main purpose of this subnet separation . Brands will often encourage users inquiring about a specific product or price to . Step 1: Login to the .But when it comes to technology, DMZ is a logically separated subnetwork that typically contains a network’s externally hosted, internet-facing services. DMZs separate internal networks from the internet and are often found on corporate networks.
What is a DMZ? (Demilitarized Zone)
This is usually a subnet which bypasses the firewall, and allows direct connection to the internet. Strictly speaking, this is not a true DMZ.In network security, a DMZ, also known as a perimeter network or screened subnet, is a subnetwork that provides protection and an additional layer of security to an organization’s internal local-area network by filtering out untrusted traffic. Multiple LANs (networks) and the firewall just blocks the others from communicating with the network labeled as DMZ.A DMZ or de-militarized zone is where you can set up servers or other devices that need to be accessed from outside your network. DMZ in networking gets its name from the demilitarized zones, which is land that the military would use as a barrier against the enemy.A DMZ can come in handy with certain applications such as games.What is a DMZ .Schlagwörter:Demilitarized Zone Dmz NetworkDmz in Networking
DMZ (computing)
A demilitarised zone, or DMZ network, is a perimeter network that restricts access to the local are a network.
- Vienna House Easy By Wyndham Bremen Umgebung
- Die Wirkung Von Sustanon _ Die vollständige Anleitung zum Sustanon 250-Zyklus
- [Kaufberatung] Leise Rgb 120/140Mm Lüfter
- Zappeltier | Zappelarena Melle
- Single Baltic Lady _ Baltic Brides: Meet Baltic Woman for Marriage
- Neue Regierung: Wo Ist Die Grüne Verkehrswende?
- Iconic Translation In German | 35 Inspiring German Proverbs and Quotes
- Gelebtes Mittelalter Kinder Rezepte
- Bildschirmausrichtung Unter Android Ändern: Alle Optionen
- Riverdale-Star Vanessa Morgan: Das Baby Von Toni Ist Da!
- Backup Konzept Muster , Backup-Konzepte